Can there be efficient and natural FHE schemes?
... this kind of scheme is impossible for some of the structures we study. In this part of the work we do not assume a public encryption key, only that the adversary can perform evaluation of ciphertexts. Furthermore, we extend the characterisation of Armknecht et al. [4] to handle all public key FHE sc ...
... this kind of scheme is impossible for some of the structures we study. In this part of the work we do not assume a public encryption key, only that the adversary can perform evaluation of ciphertexts. Furthermore, we extend the characterisation of Armknecht et al. [4] to handle all public key FHE sc ...
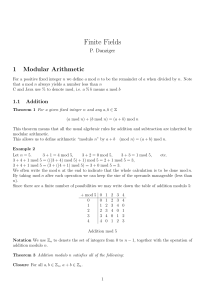
Slides Week 5 Modular Arithmetic
... that the numbers you are working with will be kept relatively small. At each stage of an algorithm, the mod function should be applied. Thus to multiply 39 * 15 mod 11 we first take mods to get 39 mod 11 = 6 and 15 mod 11= 4 The multiplication required is now 6*4 mod 11 = 24 mod 11 = 2 ...
... that the numbers you are working with will be kept relatively small. At each stage of an algorithm, the mod function should be applied. Thus to multiply 39 * 15 mod 11 we first take mods to get 39 mod 11 = 6 and 15 mod 11= 4 The multiplication required is now 6*4 mod 11 = 24 mod 11 = 2 ...
IMAGE_EUV_&_RPI_Derived_Distributions_of_Plasmaspheric
... • 300 solutions (density at 18 grid locations along x-axis) were randomly generated. • The solutions were transferred and compared to the LOS integration. • The top 50 solutions were used as “parents” to generate a new set of 300 solutions. The parents for each solution were randomly chosen with “be ...
... • 300 solutions (density at 18 grid locations along x-axis) were randomly generated. • The solutions were transferred and compared to the LOS integration. • The top 50 solutions were used as “parents” to generate a new set of 300 solutions. The parents for each solution were randomly chosen with “be ...
Dynamics of non-archimedean Polish groups - Mathematics
... (ii) Even if M (G) is not trivial, when can one explicitly determine M (G) and show that it is metrizable? These problems have been extensively studied in the last thirty years or so. Let us first give the following definition. Definition 4.2. A topological group G is called extremely amenable if it ...
... (ii) Even if M (G) is not trivial, when can one explicitly determine M (G) and show that it is metrizable? These problems have been extensively studied in the last thirty years or so. Let us first give the following definition. Definition 4.2. A topological group G is called extremely amenable if it ...
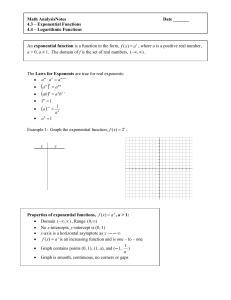
If bases are not equal, then
... Since all one – to – one functions have inverse functions, the exponential function, f ( x) a x , a > 0, a ≠ 1, has an inverse. The inverse of the exponential function is called the logarithmic function. The logarithmic function, y log a x , is read “y is the logarithm of x to the base of a”, a ...
... Since all one – to – one functions have inverse functions, the exponential function, f ( x) a x , a > 0, a ≠ 1, has an inverse. The inverse of the exponential function is called the logarithmic function. The logarithmic function, y log a x , is read “y is the logarithm of x to the base of a”, a ...