Behavioral Health Services
... see HCPCS Level II code M0064, CPT code 90863, the appropriate level of E/M service, or the appropriate psychotherapy with E/M service code. Follow third-party payer guidelines when selecting the appropriate code for these services. If a specimen is transported to an outside laboratory, report 99000 ...
... see HCPCS Level II code M0064, CPT code 90863, the appropriate level of E/M service, or the appropriate psychotherapy with E/M service code. Follow third-party payer guidelines when selecting the appropriate code for these services. If a specimen is transported to an outside laboratory, report 99000 ...
Locality Preserving Hashing Kang Zhao, Hongtao Lu and Jincheng Mei
... where bk is a bias, f (·) is an arbitrary function and sgn(·) is the sign function. Then the corresponding {0, 1} code can be given by 12 (1 + yik ). Broadly, hashing methods can be roughly divided into two main categories (Gong and Lazebnik 2011; Liu et al. 2011): data-independent methods and data- ...
... where bk is a bias, f (·) is an arbitrary function and sgn(·) is the sign function. Then the corresponding {0, 1} code can be given by 12 (1 + yik ). Broadly, hashing methods can be roughly divided into two main categories (Gong and Lazebnik 2011; Liu et al. 2011): data-independent methods and data- ...
Coding for Interactive Communication
... Tree codes will be described below. Following standard usage in complexity theory, an “oracle” is any procedure which, on request, produces a local description of the tree code; one unit of time is charged for this service. Thus any polynomial time algorithm for this task will result in polynomial t ...
... Tree codes will be described below. Following standard usage in complexity theory, an “oracle” is any procedure which, on request, produces a local description of the tree code; one unit of time is charged for this service. Thus any polynomial time algorithm for this task will result in polynomial t ...
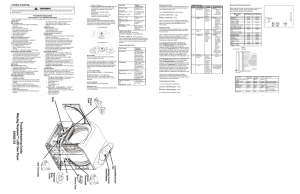
Troubleshooting Guide Maytag Neptune™ LED Gas Dryer 6390 2110
... Press Air Fluff and Time (^) to enter Service Mode. Press the Wrinkle Release key to access the Diagnostic Codes. Scroll through the Diagnostic Codes by pressing the Temperature (^) key. The first time the key is pressed the newest code will be displayed. Each additional key press shows the next cod ...
... Press Air Fluff and Time (^) to enter Service Mode. Press the Wrinkle Release key to access the Diagnostic Codes. Scroll through the Diagnostic Codes by pressing the Temperature (^) key. The first time the key is pressed the newest code will be displayed. Each additional key press shows the next cod ...
UPD6121
... Each of the higher 8 bits of the custom code is set to “1” when a diode is connected between the CCS pin and the corresponding KI/O pin, and is set to “0” when no diode is connected. If a pull-up resistor is connected to the KI/O pin corresponding to one of the lower 8 bits of the custom code’, the ...
... Each of the higher 8 bits of the custom code is set to “1” when a diode is connected between the CCS pin and the corresponding KI/O pin, and is set to “0” when no diode is connected. If a pull-up resistor is connected to the KI/O pin corresponding to one of the lower 8 bits of the custom code’, the ...
Content identification: machine learning meets coding 1
... R̂Z (j) = R̂Z (−j) j<0 with −l ≤ j ≤ l. We then average the R̂Z (j)’s for all the noise realizations. Figure 2 illustrates the resulting autocorrelation sequences of channel noises. We had M = 100 classes and used randomly generated binary values as the elements of the coding matrix C. There were 10 ...
... R̂Z (j) = R̂Z (−j) j<0 with −l ≤ j ≤ l. We then average the R̂Z (j)’s for all the noise realizations. Figure 2 illustrates the resulting autocorrelation sequences of channel noises. We had M = 100 classes and used randomly generated binary values as the elements of the coding matrix C. There were 10 ...
pdf file
... specific channel models in exchange for guaranteed universal performance for arbitrary channel models. Many results have been found for binary-input/symmetric-output (BI-SO) channels, including Burshtein et al. [13] on the soft bit value for the maximum a posteriori probability (MAP) decoder, Khande ...
... specific channel models in exchange for guaranteed universal performance for arbitrary channel models. Many results have been found for binary-input/symmetric-output (BI-SO) channels, including Burshtein et al. [13] on the soft bit value for the maximum a posteriori probability (MAP) decoder, Khande ...
lecture1424353946
... required. Below are a few examples of codes which permit error detection and error correction after detection. ...
... required. Below are a few examples of codes which permit error detection and error correction after detection. ...
Maths and the Binary Code
... • Numbers are encoded in different data formats to give them meaning ...
... • Numbers are encoded in different data formats to give them meaning ...
(attached) Annual Chargemaster Review
... codes with direct patient contact (99354–99357). The instructions were revised to clarify that these time-based add-on codes may be reported in addition to the primary E/M service (at any level), which has a typical or specified time published in the CPT code book. As a result of this clarification, ...
... codes with direct patient contact (99354–99357). The instructions were revised to clarify that these time-based add-on codes may be reported in addition to the primary E/M service (at any level), which has a typical or specified time published in the CPT code book. As a result of this clarification, ...
Codon-Anticodon Interaction and Genetic Code
... • Anticodons minimizing the conjectured operator Taver in very good agreement with the observed ones for mitochondria of animals. • Results depending only of the sign of two coupling constants. • One may expect a more complicated pattern in the general case, following the biological species. Might h ...
... • Anticodons minimizing the conjectured operator Taver in very good agreement with the observed ones for mitochondria of animals. • Results depending only of the sign of two coupling constants. • One may expect a more complicated pattern in the general case, following the biological species. Might h ...
Sparse Degrees Analysis for LT Codes Optimization
... WCCI 2012 IEEE World Congress on Computational Intelligence ...
... WCCI 2012 IEEE World Congress on Computational Intelligence ...
Chp. 2, Part I - comp
... • Choice of the divisor polynomial: – Express a corrupted message received by a receiver as P(x) + E(x), where E(x) is an error polynomial. – Errors go undetected if E(x) is divisible by C(x). ...
... • Choice of the divisor polynomial: – Express a corrupted message received by a receiver as P(x) + E(x), where E(x) is an error polynomial. – Errors go undetected if E(x) is divisible by C(x). ...
2 - Google Groups
... (GDEs & BCs), significant effects are needed to derive sensitivity equations and BCs. Discrete sensitivity only requires nominal understanding of the equations and algorithms Continuous sensitivity usually requires more changes to existing codes, while discrete sensitivity needs less changes and m ...
... (GDEs & BCs), significant effects are needed to derive sensitivity equations and BCs. Discrete sensitivity only requires nominal understanding of the equations and algorithms Continuous sensitivity usually requires more changes to existing codes, while discrete sensitivity needs less changes and m ...
Lecture 3
... In each STS-3 frame we have 3x810 = 2430 bytes. Interleave bytes --1st byte of first STS-1, 1st byte of 2nd STS-1 and so on. ...
... In each STS-3 frame we have 3x810 = 2430 bytes. Interleave bytes --1st byte of first STS-1, 1st byte of 2nd STS-1 and so on. ...
View File - University of Engineering and Technology, Taxila
... • For voice the acceptable error rate is 1 in 100 bits or 10 -2 • Data packet and messaging systems requires error rates up to 10-5 • Where this error rate is unachievable, retransmit the data (Automatic Repeat Request) • Error detection is the process of determining whether the a block of data is i ...
... • For voice the acceptable error rate is 1 in 100 bits or 10 -2 • Data packet and messaging systems requires error rates up to 10-5 • Where this error rate is unachievable, retransmit the data (Automatic Repeat Request) • Error detection is the process of determining whether the a block of data is i ...
2D Geometry Lesson
... 1. Explain to students that they will be coding shapes using the iPad Hopscotch App 2. Watch YouTube Video on Shreddies 3. To prove that a square and diamond are the same shape, have students use Hopscotch to code both shapes. 4. You may want to get students started by showing how to leave a trail. ...
... 1. Explain to students that they will be coding shapes using the iPad Hopscotch App 2. Watch YouTube Video on Shreddies 3. To prove that a square and diamond are the same shape, have students use Hopscotch to code both shapes. 4. You may want to get students started by showing how to leave a trail. ...