Shape modeling and matching in identifying protein structure from
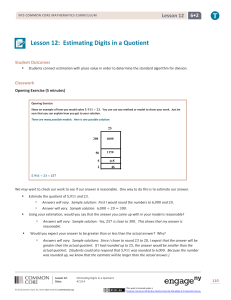
... the lengths of helices as well as their connectivity. In particular, the graph representing the density volume is obtained by computing a skeleton that encodes the topology of the high-density regions (Figure 1 (d)). Using the shape representations, helix correspondence reduces to a constrained erro ...
... the lengths of helices as well as their connectivity. In particular, the graph representing the density volume is obtained by computing a skeleton that encodes the topology of the high-density regions (Figure 1 (d)). Using the shape representations, helix correspondence reduces to a constrained erro ...
Distributed Spectrum Management and Relay
... Proposed Solution Algorithm – Monotonicity Decompose original problem into two subproblems Design distributed algorithm for each subproblem Perform two algorithms iteratively Monotonicity condition is easily satisfied by each subproblem ...
... Proposed Solution Algorithm – Monotonicity Decompose original problem into two subproblems Design distributed algorithm for each subproblem Perform two algorithms iteratively Monotonicity condition is easily satisfied by each subproblem ...
Thomas L. Magnanti and Georgia Perakis
... Motivated by the celebrity of these geometric algorithms for solving linear programming problems, in this paper we examine the question of whether similar geometric algorithms will efficiently solve variational inequality problems. The general geometric framework, which we describe in detail in Sect ...
... Motivated by the celebrity of these geometric algorithms for solving linear programming problems, in this paper we examine the question of whether similar geometric algorithms will efficiently solve variational inequality problems. The general geometric framework, which we describe in detail in Sect ...
A Dynamic Programming Approach to De Novo Peptide Sequencing
... n COOH). These two ions are complementary because joining them determines the original peptide sequence. This dissociation process fragments a large number of molecules of the same peptide sequence, and ideally, the resulting ions contain all possible pre x subsequences and suÆx subsequences. Table ...
... n COOH). These two ions are complementary because joining them determines the original peptide sequence. This dissociation process fragments a large number of molecules of the same peptide sequence, and ideally, the resulting ions contain all possible pre x subsequences and suÆx subsequences. Table ...
Reinforcement Learning for Neural Networks using Swarm Intelligence
... candidate solution for a given problem. Second, when an ant follows a path, the amount of pheromone deposit on that path is proportional to the quality of the corresponding candidate solution for the target problem. Third, when an ant has to choose between two or more paths, the path(s) with a large ...
... candidate solution for a given problem. Second, when an ant follows a path, the amount of pheromone deposit on that path is proportional to the quality of the corresponding candidate solution for the target problem. Third, when an ant has to choose between two or more paths, the path(s) with a large ...
Detecting Wormhole Attacks in Wireless Sensor Networks
... antenna and knows its physical location. Other nodes in the network use the anchor nodes to locate themselves. Since a wormhole produces shortcuts in a network, the directional antennas deployed in the anchor nodes help detect the attack; nodes can then defend against the attack by discarding incorr ...
... antenna and knows its physical location. Other nodes in the network use the anchor nodes to locate themselves. Since a wormhole produces shortcuts in a network, the directional antennas deployed in the anchor nodes help detect the attack; nodes can then defend against the attack by discarding incorr ...
NOVEL TRANSFORMATION TECHNIQUES USING Q-HEAPS WITH APPLICATIONS TO COMPUTATIONAL GEOMETRY
... versions of the original query. Finally, a non-empty output at a node no longer ensures that we can afford to search each of its children, since none of them may contain an output object. Doing so would result in an O(f log² n) term in the overall search complexity, where f is the output size. In th ...
... versions of the original query. Finally, a non-empty output at a node no longer ensures that we can afford to search each of its children, since none of them may contain an output object. Doing so would result in an O(f log² n) term in the overall search complexity, where f is the output size. In th ...
Global Consistency for Continuous Constraints
... provide relatively poor results when applied to continuous CSPs: they ensure neither completeness nor convergence in the general case (a good insight into the problems encountered can be found in [1]). However, Faltings [5] has shown that some undesirable features of propagation algorithms with inte ...
... provide relatively poor results when applied to continuous CSPs: they ensure neither completeness nor convergence in the general case (a good insight into the problems encountered can be found in [1]). However, Faltings [5] has shown that some undesirable features of propagation algorithms with inte ...
pptx - Electrical and Computer Engineering
... finding solutions to the other problems? To answer this, we must define a reduction of a problem – A reduction is a transformation of one problem A into another problem B such that the solution to B yields a solution to A – A reduction that may be preformed in polynomial time is said to be a ...
... finding solutions to the other problems? To answer this, we must define a reduction of a problem – A reduction is a transformation of one problem A into another problem B such that the solution to B yields a solution to A – A reduction that may be preformed in polynomial time is said to be a ...
Rotamer Packing Problem - NUS School of Computing
... • In a case study using insulin structure of 76 residues, the initial number of rotamer configurations is 2.7E+76 • After 9 iterations, only 7200 are left. ...
... • In a case study using insulin structure of 76 residues, the initial number of rotamer configurations is 2.7E+76 • After 9 iterations, only 7200 are left. ...
Blame Trees - Edward Z. Yang
... modifications to old versions of document, a confluently persistent structure additionally supports a merge operation. Any two documents can be merged, which means that the version dependencies can form a directed acyclic graph (DAG). Our paper presents an implementation of this data structure which ...
... modifications to old versions of document, a confluently persistent structure additionally supports a merge operation. Any two documents can be merged, which means that the version dependencies can form a directed acyclic graph (DAG). Our paper presents an implementation of this data structure which ...