Polynomial Review Answer Section
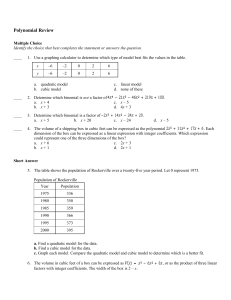
... a. Factor the polynomial to find linear expressions for the height and the width. b. Graph the function. Find the x-intercepts. What do they represent? c. Describe a realistic domain for the function. d. Find the maximum volume of the box. 7. The volume in cubic feet of a workshop’s storage chest c ...
... a. Factor the polynomial to find linear expressions for the height and the width. b. Graph the function. Find the x-intercepts. What do they represent? c. Describe a realistic domain for the function. d. Find the maximum volume of the box. 7. The volume in cubic feet of a workshop’s storage chest c ...
4.) Groups, Rings and Fields
... and arbitrary complex coefficients an−1 , ..., a0 ∈ C there is a complex solution x = λ ∈ C, and an iterated application of that fact then leads to a factorization f (x) = (x − λ1 ) · ... · (x − λn ) of the polynomial f (x) with (not necessarily pairwise different) complex numbers λ1 , ..., λn ∈ C. ...
... and arbitrary complex coefficients an−1 , ..., a0 ∈ C there is a complex solution x = λ ∈ C, and an iterated application of that fact then leads to a factorization f (x) = (x − λ1 ) · ... · (x − λn ) of the polynomial f (x) with (not necessarily pairwise different) complex numbers λ1 , ..., λn ∈ C. ...
Document
... The circuit computes a function C : 2n → 2m in an obvious way (where we identify {0, 1}n = 2n ). Any language L can be identified with a family of Boolean functions Ln : 2n → 2, n ∈ ω, where Ln is the restriction of the characteristic function of L to 2n . 2.1.3 Definition Circuit complexity C(f ) o ...
... The circuit computes a function C : 2n → 2m in an obvious way (where we identify {0, 1}n = 2n ). Any language L can be identified with a family of Boolean functions Ln : 2n → 2, n ∈ ω, where Ln is the restriction of the characteristic function of L to 2n . 2.1.3 Definition Circuit complexity C(f ) o ...
The Weil Pairing on Elliptic Curves and Its Cryptographic Applications
... truly effective on very specific curves (curves where the the embedding degree k is very small.) Thus, the elliptic curve discrete logarithm problem was not harmed too much, and eventually it was even strengthened by the work of Joux, who ironically used the pairings originally meant to weaken Diff ...
... truly effective on very specific curves (curves where the the embedding degree k is very small.) Thus, the elliptic curve discrete logarithm problem was not harmed too much, and eventually it was even strengthened by the work of Joux, who ironically used the pairings originally meant to weaken Diff ...
analytic and combinatorial number theory ii
... Thue reproved it in the next year in his famous article [41] where he derived it from a theorem on approximation of algebraic numbers by fractions. Theorem 1.0.2 (Thue’s inequality, 1909) Let α ∈ C be an algebraic number with degree d ∈ N and let ε ∈ (0, 12 ). Then only finitely many fractions p q ∈ ...
... Thue reproved it in the next year in his famous article [41] where he derived it from a theorem on approximation of algebraic numbers by fractions. Theorem 1.0.2 (Thue’s inequality, 1909) Let α ∈ C be an algebraic number with degree d ∈ N and let ε ∈ (0, 12 ). Then only finitely many fractions p q ∈ ...
PM 464
... 1. Finiteness in property (4) is required; consider for example Z in R. We have already seen how to show that this is not an algebraic set. 2. Properties (3), (4), and (5) show that the collection of algebraic sets form the closed sets of a topology on An . This topology is known as the Zariski topo ...
... 1. Finiteness in property (4) is required; consider for example Z in R. We have already seen how to show that this is not an algebraic set. 2. Properties (3), (4), and (5) show that the collection of algebraic sets form the closed sets of a topology on An . This topology is known as the Zariski topo ...
Homework: square roots and factorization
... Homework: square roots and factorization For a positive integer n, an integer a is called a quadratic residue modulo n if a ∈ Z/nZ× satisfies x2 = a mod n for some integer x. In this case x is called a square root of a modulo n. 1. Compute square roots of 1 and −1 modulo 7 and modulo 13. 2. Check th ...
... Homework: square roots and factorization For a positive integer n, an integer a is called a quadratic residue modulo n if a ∈ Z/nZ× satisfies x2 = a mod n for some integer x. In this case x is called a square root of a modulo n. 1. Compute square roots of 1 and −1 modulo 7 and modulo 13. 2. Check th ...
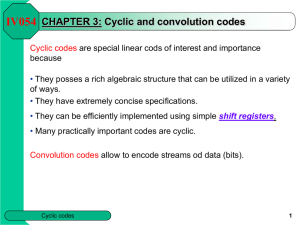
CHAPTER 3: Cyclic Codes
... A codeword of a cyclic code is usually denoted a0 a1…an -1 and to each such a codeword the polynomial a0 + a1 x + a2 x2 + … + an -1 xn -1 will be associated. NOTATION : Fq[x] denotes the set of all polynomials over GF(q ). deg (f(x )) = the largest m such that xm has a non-zero coefficient in f(x). ...
... A codeword of a cyclic code is usually denoted a0 a1…an -1 and to each such a codeword the polynomial a0 + a1 x + a2 x2 + … + an -1 xn -1 will be associated. NOTATION : Fq[x] denotes the set of all polynomials over GF(q ). deg (f(x )) = the largest m such that xm has a non-zero coefficient in f(x). ...
Application of the graded Posner theorem
... Let G be a group and F an algebraically closed of 0 characteristic and A, B two f.d. G-simple F-algebras. Then, A is G-isomorphic to B iff idG (A) = idG (B ). Notice that the theorem is easy when G = {e }. Indeed, A = Mn (F), B = Mm (F) and n2 = exp(A) is determined by id (A). We now show how one ca ...
... Let G be a group and F an algebraically closed of 0 characteristic and A, B two f.d. G-simple F-algebras. Then, A is G-isomorphic to B iff idG (A) = idG (B ). Notice that the theorem is easy when G = {e }. Indeed, A = Mn (F), B = Mm (F) and n2 = exp(A) is determined by id (A). We now show how one ca ...
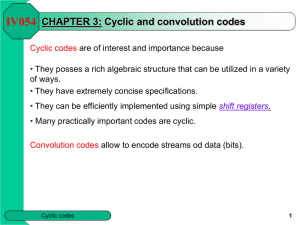
CHAPTER 3: Cyclic Codes
... A codeword of a cyclic code is usually denoted a0 a1…an -1 and to each such a codeword the polynomial a0 + a1 x + a2 x2 + … + an -1 xn -1 will be associated. NOTATION : Fq[x] denotes the set of all polynomials over GF(q ). deg (f(x )) = the largest m such that xm has a non-zero coefficient in f(x). ...
... A codeword of a cyclic code is usually denoted a0 a1…an -1 and to each such a codeword the polynomial a0 + a1 x + a2 x2 + … + an -1 xn -1 will be associated. NOTATION : Fq[x] denotes the set of all polynomials over GF(q ). deg (f(x )) = the largest m such that xm has a non-zero coefficient in f(x). ...
(pdf)
... Thus, sn (and therefore all higher powers of s) can be expressed as R-linear combinations of sn−1 , . . . , s, 1. Thus, R[s] = R1 + Rs + · · · + Rsn−1 , which means that R[s] is a finitely generated R-module, as desired. ...
... Thus, sn (and therefore all higher powers of s) can be expressed as R-linear combinations of sn−1 , . . . , s, 1. Thus, R[s] = R1 + Rs + · · · + Rsn−1 , which means that R[s] is a finitely generated R-module, as desired. ...
FOUNDATIONS OF ALGEBRAIC GEOMETRY CLASS 27
... Hence we can get a bunch of invertible sheaves, by taking differences of these two. In fact we “usually get them all”! It is very hard to describe an invertible sheaf on a finite type k-scheme that is not describable in such a way. For example, we will see soon that there are none if the scheme is n ...
... Hence we can get a bunch of invertible sheaves, by taking differences of these two. In fact we “usually get them all”! It is very hard to describe an invertible sheaf on a finite type k-scheme that is not describable in such a way. For example, we will see soon that there are none if the scheme is n ...