ppt
... Why does Sandboxing slow down normal execution? Why does it speed up inter-module communication compared to Mach? What is a jump-table and why is it needed? On balance is Sandboxing a win or loss? o o ...
... Why does Sandboxing slow down normal execution? Why does it speed up inter-module communication compared to Mach? What is a jump-table and why is it needed? On balance is Sandboxing a win or loss? o o ...
Chapter 4-1
... Share via access limitation – each user is checked for access availability of an object Share by compatibilities- dynamic creation of shared objects Limit use of an object- user has varying access to an object Each has a varying level of granularity - Greater granularity creates greater access contr ...
... Share via access limitation – each user is checked for access availability of an object Share by compatibilities- dynamic creation of shared objects Limit use of an object- user has varying access to an object Each has a varying level of granularity - Greater granularity creates greater access contr ...
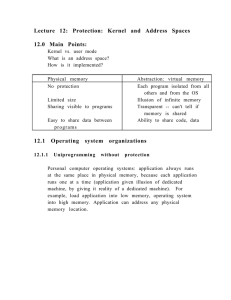
Lecture 12: Protection: Kernel and Address Spaces 12.0 Main Points
... saves current program counter jumps to handler in kernel handler saves previous state of any registers it uses Context switching between programs: same as with threads, except now also save and restore pointer to translation table. To resume a program, re-load registers, and jump to old PC. How does ...
... saves current program counter jumps to handler in kernel handler saves previous state of any registers it uses Context switching between programs: same as with threads, except now also save and restore pointer to translation table. To resume a program, re-load registers, and jump to old PC. How does ...
Operating Systems
... Process states, Process Scheduling, Process hierarchy, Threads, Threading issues, Multithreading models, Non-pre-emptive and pre-emptive scheduling algorithms, Concurrent processes, Critical section, Semaphores, methods for inter-process communication, Deadlocks. [1] Page 101 to 113, Page 115 to 122 ...
... Process states, Process Scheduling, Process hierarchy, Threads, Threading issues, Multithreading models, Non-pre-emptive and pre-emptive scheduling algorithms, Concurrent processes, Critical section, Semaphores, methods for inter-process communication, Deadlocks. [1] Page 101 to 113, Page 115 to 122 ...
Topic 1: Introduction to Computers and Programming
... Modern software development is done in high-level languages, with few exceptions. High-level language is first compiled from source code to assembly and then assembler into machine code. Modern compilers perform the assembler function as well. Compiled source code is called an object file. ...
... Modern software development is done in high-level languages, with few exceptions. High-level language is first compiled from source code to assembly and then assembler into machine code. Modern compilers perform the assembler function as well. Compiled source code is called an object file. ...
over view of operating system
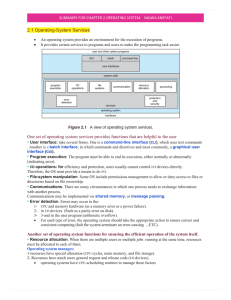
... System-call interface maintains a table indexed according to these Numbers The system call interface invokes intended system call in OS kernel and returns status of the system call and any return values The caller need know nothing about how the system call is implemented Just needs to ob ...
... System-call interface maintains a table indexed according to these Numbers The system call interface invokes intended system call in OS kernel and returns status of the system call and any return values The caller need know nothing about how the system call is implemented Just needs to ob ...
Transparency Description
... A complex algorithm is going to be executed. Which one is cheaper? Using a multicomputer or a multiprocessor? What’s the idea behind the DSM? What’s the idea behind a middleware? What’s the problems of using a middleware system? What’s the difference of policy and mechanism? Why open distributed sys ...
... A complex algorithm is going to be executed. Which one is cheaper? Using a multicomputer or a multiprocessor? What’s the idea behind the DSM? What’s the idea behind a middleware? What’s the problems of using a middleware system? What’s the difference of policy and mechanism? Why open distributed sys ...
PDF
... • Round robin allocation of slices. • Library operating system responsible for context switching. • It the time a process takes is excessive, it is ...
... • Round robin allocation of slices. • Library operating system responsible for context switching. • It the time a process takes is excessive, it is ...
Using the SEL System Control Library for Computer
... Software failures are the reason SEL designed a hardware watchdog into each of its computers. The watchdog provides a mechanism, independent of software, to restore normal operation after a catastrophic system lockup. Before the introduction of the SSC library, supervision of the watchdog was provid ...
... Software failures are the reason SEL designed a hardware watchdog into each of its computers. The watchdog provides a mechanism, independent of software, to restore normal operation after a catastrophic system lockup. Before the introduction of the SSC library, supervision of the watchdog was provid ...
Design and Implementation of Globally
... Camera controller code can be modified at runtime to account for changes in the tracking algorithm etc. Load balancing and resilience to fault is provided by the multiple servers providing source code for GUIListener clients and the one-to-many communication protocol. ...
... Camera controller code can be modified at runtime to account for changes in the tracking algorithm etc. Load balancing and resilience to fault is provided by the multiple servers providing source code for GUIListener clients and the one-to-many communication protocol. ...
OS and Computer Architecture
... Users, servers, and storage devices are all dispersed among the various sites. The OS must carry out its file services across the network and manage multiple, independent storage devices. ...
... Users, servers, and storage devices are all dispersed among the various sites. The OS must carry out its file services across the network and manage multiple, independent storage devices. ...
Introduction to Operating Systems: A Look at Unix Introduction to
... Microsoft, with 95, 98, NT, and 2000 has made the OS both more accessible and more opaque Ü In order to fully understand Unix, it is important to have a better structural model of operating systems Ü ...
... Microsoft, with 95, 98, NT, and 2000 has made the OS both more accessible and more opaque Ü In order to fully understand Unix, it is important to have a better structural model of operating systems Ü ...
CSS430: Introduction - UW Faculty Web Server
... multiprogramming. Each user has at least one separate program in memory. A program in execution is referred to as a process. Process switch occur so frequently that the users can interact with each program while it is running. File system allows users to access data and program interactively. CSS430 ...
... multiprogramming. Each user has at least one separate program in memory. A program in execution is referred to as a process. Process switch occur so frequently that the users can interact with each program while it is running. File system allows users to access data and program interactively. CSS430 ...
Design of MS-DOS
... - Design Principles / Fundamentals - Basis of many other Disk(based) Operating Systems. • The first personal computer DOS, called Personal Computer Disk Operating System, was developed for IBM by Microsoft Corporation. • MS retained the rights to market a Microsoft version, called MS-DOS. PC-DOS and ...
... - Design Principles / Fundamentals - Basis of many other Disk(based) Operating Systems. • The first personal computer DOS, called Personal Computer Disk Operating System, was developed for IBM by Microsoft Corporation. • MS retained the rights to market a Microsoft version, called MS-DOS. PC-DOS and ...
CMPU1022 Operating Systems 1
... 9. Discuss networked, client-server and distributed operating systems and how they differ from single user operating systems 10. Display and perform proficient command line interaction with various operating systems ...
... 9. Discuss networked, client-server and distributed operating systems and how they differ from single user operating systems 10. Display and perform proficient command line interaction with various operating systems ...
Introduction to Operating Systems
... onto the physical memory of the machine. A memory reference within one running program does not affect the address space of other processes (or the OS itself); as far as the running program is concerned, it has physical memory all to itself. The reality, however, is that physical memory is a shared ...
... onto the physical memory of the machine. A memory reference within one running program does not affect the address space of other processes (or the OS itself); as far as the running program is concerned, it has physical memory all to itself. The reality, however, is that physical memory is a shared ...
Operating Systems Principles Lecture 1: Introduction
... Because the user is present and interacting with the computer, the computer system must respond quickly to user requests, otherwise user productivity could suffer. Timesharing systems were developed to multiprogram large number of simultaneous interactive users. ...
... Because the user is present and interacting with the computer, the computer system must respond quickly to user requests, otherwise user productivity could suffer. Timesharing systems were developed to multiprogram large number of simultaneous interactive users. ...
FAT:
... system HPFS contained several important new features. When Microsoft created their new operating system, they borrowed many of these concepts for NTFS. When Microsoft created their new operating system, they borrowed many of these concepts for NTFS. Probably as a result of this common ancestry, HPFS ...
... system HPFS contained several important new features. When Microsoft created their new operating system, they borrowed many of these concepts for NTFS. When Microsoft created their new operating system, they borrowed many of these concepts for NTFS. Probably as a result of this common ancestry, HPFS ...
Summary for chapter 2 OPERATING SYSTEM nAJWA kNEFATI
... For either files or directories, we need to be able to determine the values of various attributes and perhaps to reset them. File attributes include the file name, file type, protection codes, accounting information, and so on. At least two system calls, get file attributes () and set file attri ...
... For either files or directories, we need to be able to determine the values of various attributes and perhaps to reset them. File attributes include the file name, file type, protection codes, accounting information, and so on. At least two system calls, get file attributes () and set file attri ...
CS4273 Distributed System Technologies and Programming Tutorial on Java Networking
... Distributed System Technologies and Programming Tutorial on Java Networking 1. After you put your cgi program in place, you’d like to test if the cgi program can be started properly. a) Write the commands of using “telnet” to let the http server start your cgi program. b) List all possible ways to s ...
... Distributed System Technologies and Programming Tutorial on Java Networking 1. After you put your cgi program in place, you’d like to test if the cgi program can be started properly. a) Write the commands of using “telnet” to let the http server start your cgi program. b) List all possible ways to s ...
2. OS Components
... but to halt the system. At other times, it might terminate an error-causing process or return an error code to a process for the process to detect and possibly correct. Another set of operating system functions exists not for helping the user but rather for ensuring the efficient operation of the sy ...
... but to halt the system. At other times, it might terminate an error-causing process or return an error code to a process for the process to detect and possibly correct. Another set of operating system functions exists not for helping the user but rather for ensuring the efficient operation of the sy ...
Interface
... Invoke code (let the object do work on the caller’s behalf) Mutate the object’s public/private state ...
... Invoke code (let the object do work on the caller’s behalf) Mutate the object’s public/private state ...
Interface - Duke University
... Invoke code (let the object do work on the caller’s behalf) Mutate the object’s public/private state ...
... Invoke code (let the object do work on the caller’s behalf) Mutate the object’s public/private state ...
Library (computing)
In computer science, a library is a collection of non-volatile resources used by computer programs, often to develop software. These may include configuration data, documentation, help data, message templates, pre-written code and subroutines, classes, values or type specifications. In IBM's OS/360 and its successors they are referred to as partitioned data sets.In computer science, a library is a collection of implementations of behavior, written in terms of a language, that has a well-defined interface by which the behavior is invoked. This means that as long as a higher level program uses a library to make system calls, it does not need to be re-written to implement those system calls over and over again. In addition, the behavior is provided for reuse by multiple independent programs. A program invokes the library-provided behavior via a mechanism of the language. For example, in a simple imperative language such as C, the behavior in a library is invoked by using C's normal function-call. What distinguishes the call as being to a library, versus being to another function in the same program, is the way that the code is organized in the system. Library code is organized in such a way that it can be used by multiple programs that have no connection to each other, while code that is part of a program is organized to only be used within that one program. This distinction can gain a hierarchical notion when a program grows large, such as a multi-million-line program. In that case, there may be internal libraries that are reused by independent sub-portions of the large program. The distinguishing feature is that a library is organized for the purposes of being reused by independent programs or sub-programs, and the user only needs to know the interface, and not the internal details of the library.The value of a library is the reuse of the behavior. When a program invokes a library, it gains the behavior implemented inside that library without having to implement that behavior itself. Libraries encourage the sharing of code in a modular fashion, and ease the distribution of the code. The behavior implemented by a library can be connected to the invoking program at different program lifecycle phases. If the code of the library is accessed during the build of the invoking program, then the library is called a static library. An alternative is to build the executable of the invoking program and distribute that, independently from the library implementation. The library behavior is connected after the executable has been invoked to be executed, either as part of the process of starting the execution, or in the middle of execution. In this case the library is called a dynamic library. A dynamic library can be loaded and linked as part of preparing a program for execution, by the linker. Alternatively, in the middle of execution, an application may explicitly request that a module be loaded.Most compiled languages have a standard library although programmers can also create their own custom libraries. Most modern software systems provide libraries that implement the majority of system services. Such libraries have commoditized the services which a modern application requires. As such, most code used by modern applications is provided in these system libraries.