1.1. OS Introduction Operating System types
... o 1.2.7. Handheld Systems Textbook - Silberschatz, Chapter 1 ...
... o 1.2.7. Handheld Systems Textbook - Silberschatz, Chapter 1 ...
Windows Server 2008 - Dr. Edward E. Boas, Jr., Professor
... • Guidelines checklist for software installation (cont): – Make sure the software is well documented and supported by the vendor – Determine, in advance, how to back up important files associated with the software – Determine if running the program requires adjustments to page or swap files used by ...
... • Guidelines checklist for software installation (cont): – Make sure the software is well documented and supported by the vendor – Determine, in advance, how to back up important files associated with the software – Determine if running the program requires adjustments to page or swap files used by ...
Chapter 6 Introduction to Network Operating Systems
... runs on many different computers and was first released in 1991. • Linux is portable, which means versions can be found running on name brand or clone PCs. • Linux offers many features adopted from other versions of UNIX. ...
... runs on many different computers and was first released in 1991. • Linux is portable, which means versions can be found running on name brand or clone PCs. • Linux offers many features adopted from other versions of UNIX. ...
lec4
... • If there are n processes in the ready queue and the time quantum is q, then each process gets 1/n of the CPU time in chunks of at most q time units at once. No process waits more than (n-1)q time units. ...
... • If there are n processes in the ready queue and the time quantum is q, then each process gets 1/n of the CPU time in chunks of at most q time units at once. No process waits more than (n-1)q time units. ...
notes - University of Arizona Computer Science
... Append stdout to a file: wc foo.c >> /tmp/foo Write stdout & stderr to a file: wc foo.c >& /tmp/foo Ignore stdout: wc foo.c > /dev/null Read stdin from a file: wc < foo.c Read stdin from a device: wc < /dev/null ...
... Append stdout to a file: wc foo.c >> /tmp/foo Write stdout & stderr to a file: wc foo.c >& /tmp/foo Ignore stdout: wc foo.c > /dev/null Read stdin from a file: wc < foo.c Read stdin from a device: wc < /dev/null ...
02_08_05_scheduling
... • The ready queue is treated as a circular queue, and the CPU scheduler rotates among the processes in the ready queue, giving each a time slice, after which it is preempted by a timer interrupt and another process is started – useful for time sharing multitasking systems - most widely used scheduli ...
... • The ready queue is treated as a circular queue, and the CPU scheduler rotates among the processes in the ready queue, giving each a time slice, after which it is preempted by a timer interrupt and another process is started – useful for time sharing multitasking systems - most widely used scheduli ...
Introduction to Operating Systems
... E.g., allows sharing of code pages between processes Plus many other optimizations ...
... E.g., allows sharing of code pages between processes Plus many other optimizations ...
DeadLocks
... – Must guarantee that whenever a process requests a resource, it does not hold any other resources. – Require process to request and be allocated all its resources before it begins execution, or allow process to request resources only when the process has none. – Low resource utilization; starvation ...
... – Must guarantee that whenever a process requests a resource, it does not hold any other resources. – Require process to request and be allocated all its resources before it begins execution, or allow process to request resources only when the process has none. – Low resource utilization; starvation ...
Name (Please print legibly)
... e) An example of disallowing mutually exclusive access to resources 20. Which of the following lock request sequences results in a deadlock? Assume that no locks are released in each of the sequences below. Assume no resources were locked at the beginning of each sequence. Assume that a request for ...
... e) An example of disallowing mutually exclusive access to resources 20. Which of the following lock request sequences results in a deadlock? Assume that no locks are released in each of the sequences below. Assume no resources were locked at the beginning of each sequence. Assume that a request for ...
CS111—Operating System Principles
... Somewhere inside the ROM on i386 machines, we can find a Basic Input/Output System (BIOS), which knows how to access storage devices. The BIOS code first executes the Power-On Self Test (POST), which checks memory and devices for their presence and correct operation. (During this time, you will hear ...
... Somewhere inside the ROM on i386 machines, we can find a Basic Input/Output System (BIOS), which knows how to access storage devices. The BIOS code first executes the Power-On Self Test (POST), which checks memory and devices for their presence and correct operation. (During this time, you will hear ...
MachOs-by-Doug-Hill-Liza-Hill-Josh-Mickley-Alex
... • A task is the basic unit of resource allocation. It includes a virtual address space, access to resources, and may include one or more threads. • A thread is a sequence of instruction executions. All threads within a task share the resources of that task. ...
... • A task is the basic unit of resource allocation. It includes a virtual address space, access to resources, and may include one or more threads. • A thread is a sequence of instruction executions. All threads within a task share the resources of that task. ...
Operating Systems
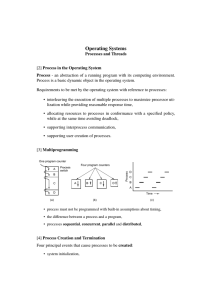
... Process - an abstraction of a running program with its computing environment. Process is a basic dynamic object in the operating system. Requirements to be met by the operating system with reference to processes: • interleaving the execution of multiple processes to maximize processor utilization wh ...
... Process - an abstraction of a running program with its computing environment. Process is a basic dynamic object in the operating system. Requirements to be met by the operating system with reference to processes: • interleaving the execution of multiple processes to maximize processor utilization wh ...
Advanced Computer Architectures
... setting up the process description allocating an address space loading the program into the allocated address space, and passing the process description to the scheduler process states ready to run running wait ...
... setting up the process description allocating an address space loading the program into the allocated address space, and passing the process description to the scheduler process states ready to run running wait ...
Final Exam 2004 PowerPoint
... – A secure “tunnel” through the Internet – Windows XP support two VPN protocols: – Point-to-Point-Tunneling Protocol (PPTP) (9x+) • Allows you to establish a secure remote access pipeline over the public Internet and to “tunnel” IPX or TCP/IP traffic inside ...
... – A secure “tunnel” through the Internet – Windows XP support two VPN protocols: – Point-to-Point-Tunneling Protocol (PPTP) (9x+) • Allows you to establish a secure remote access pipeline over the public Internet and to “tunnel” IPX or TCP/IP traffic inside ...
Operating Systems 2230 Lecture 8: Complexity of I/O Devices
... Application: the expected use of a device affects the software policies and priorities employed by an operating system. For example, different output devices may be supported at different priorities (particularly in a real-time, alert-based system) and otherwise identical disk drives may be managed ...
... Application: the expected use of a device affects the software policies and priorities employed by an operating system. For example, different output devices may be supported at different priorities (particularly in a real-time, alert-based system) and otherwise identical disk drives may be managed ...
Introduction to Object Technology
... scheduling priority of the process. In some systems, several values are required (e.g., default, current, highest-allowable) ••Scheduling-related information: This will depend on the scheduling algorithm used. Examples are the amount of time that the process has been waiting and the amount of time t ...
... scheduling priority of the process. In some systems, several values are required (e.g., default, current, highest-allowable) ••Scheduling-related information: This will depend on the scheduling algorithm used. Examples are the amount of time that the process has been waiting and the amount of time t ...
Process Description and Control
... • File tables: provides information about – the existence of files – their location on secondary memory ...
... • File tables: provides information about – the existence of files – their location on secondary memory ...
Tutorial 2: Question 1: The services and functions provided by an
... The services and functions provided by an operating system can be divided into two main categories. Briefly describe the two categories and discuss how they differ. Question 2: Describe three general methods for passing parameters to the operating system. Question 3: Describe how you could obtain a ...
... The services and functions provided by an operating system can be divided into two main categories. Briefly describe the two categories and discuss how they differ. Question 2: Describe three general methods for passing parameters to the operating system. Question 3: Describe how you could obtain a ...
Document
... ∗ memory mapping • interrupts – used by device for asynchronous notification (e.g., of request completion) – handled by interrupt handlers in the operating system ...
... ∗ memory mapping • interrupts – used by device for asynchronous notification (e.g., of request completion) – handled by interrupt handlers in the operating system ...
lec03-concurrency
... – Internally concurrent because have to deal with concurrent requests by multiple users – But no protection needed within kernel ...
... – Internally concurrent because have to deal with concurrent requests by multiple users – But no protection needed within kernel ...
BackDoors
... but he would be better off choosing a service that never gets used and that is either activated manually or even completely disabled. It is sufficient to remove it using the srvinstw.exe utility and again to install a new service with the same name. By doing so, the hacker considerably reduces possi ...
... but he would be better off choosing a service that never gets used and that is either activated manually or even completely disabled. It is sufficient to remove it using the srvinstw.exe utility and again to install a new service with the same name. By doing so, the hacker considerably reduces possi ...
File System Maintenance (continued)
... • A file can be found by using the find command: – atime for last accessed time – ctime for last changed time – mtime for last modification time – name for the filename, including the use of wildcard searches ...
... • A file can be found by using the find command: – atime for last accessed time – ctime for last changed time – mtime for last modification time – name for the filename, including the use of wildcard searches ...
CS 111 Processes
... A process may be create several new processes, via a create-process system call, during the course of execution. The creating process is called a Parent process, and new processes are called the Children of that process. Each of these new processes may in turn create other processes forming a tree o ...
... A process may be create several new processes, via a create-process system call, during the course of execution. The creating process is called a Parent process, and new processes are called the Children of that process. Each of these new processes may in turn create other processes forming a tree o ...