Toward a truly personal computer
... Next 50 yrs: IA rather than AI? Intelligence Augmentation: human + machine = super intelligence ...
... Next 50 yrs: IA rather than AI? Intelligence Augmentation: human + machine = super intelligence ...
How Do We Know That We Know? The Accessibility Model
... information pertaining to the presence of the solicited item in memory and that this information appears in a ready-made format. At first sight, this solution to the question of how one knows that one knows appears to raise the homunculus problem of how the monitor itself can know. However, the idea ...
... information pertaining to the presence of the solicited item in memory and that this information appears in a ready-made format. At first sight, this solution to the question of how one knows that one knows appears to raise the homunculus problem of how the monitor itself can know. However, the idea ...
Organisational Intelligence and Distributed AI
... The analysis of this chapter starts from organisational theory, and from this it draws conclusions for the design, and possible organisational applications, of Distributed AI systems. We first review how the concept of organisations has emerged from non-organised "blackbox" entities to so-called "co ...
... The analysis of this chapter starts from organisational theory, and from this it draws conclusions for the design, and possible organisational applications, of Distributed AI systems. We first review how the concept of organisations has emerged from non-organised "blackbox" entities to so-called "co ...
Toward a truly personal computer
... Copyright 1997 ACM, Association for Computing The files on this disk or server have been provided by ACM. Copyright and all rights therein are maintained by ACM. It is understood that all persons copying this information will adhere to the terms and constraints invoked by ACM’s copyright. These wo ...
... Copyright 1997 ACM, Association for Computing The files on this disk or server have been provided by ACM. Copyright and all rights therein are maintained by ACM. It is understood that all persons copying this information will adhere to the terms and constraints invoked by ACM’s copyright. These wo ...
Efficiently Gathering Information in Costly Domains
... In many settings characterized by uncertainty agents can engage in information gathering actions before making decisions. For example, consider an e-commerce application in which a buyer needs to choose between several suppliers of a product or service (in absence of a built-in reputation system). T ...
... In many settings characterized by uncertainty agents can engage in information gathering actions before making decisions. For example, consider an e-commerce application in which a buyer needs to choose between several suppliers of a product or service (in absence of a built-in reputation system). T ...
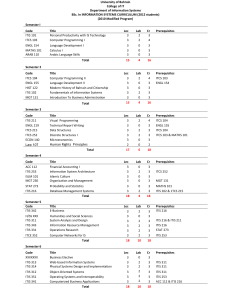
BSc in IS Plan for 2012
... The Course presents the basic concepts and methodologies for the discipline known as Enterprise IS/IT architecting within a framework, structure, and methodology. Enterprise IS/IT architecting is a necessary step for designing and developing of information systems. It includes the definition of the ...
... The Course presents the basic concepts and methodologies for the discipline known as Enterprise IS/IT architecting within a framework, structure, and methodology. Enterprise IS/IT architecting is a necessary step for designing and developing of information systems. It includes the definition of the ...
Artificial Intelligence, Ontologies, and Common Sense
... • How could Cyc’s knowledge-base affect the design of information organization and retrieval systems? ...
... • How could Cyc’s knowledge-base affect the design of information organization and retrieval systems? ...
Global Information Grid (GIG)
... processes, and personnel for collecting, processing, storing, disseminating, and managing information on demand to warfighters, policy makers, and support personnel. The GIG includes all owned and leased communications and computing systems and services, software (including applications), data, secu ...
... processes, and personnel for collecting, processing, storing, disseminating, and managing information on demand to warfighters, policy makers, and support personnel. The GIG includes all owned and leased communications and computing systems and services, software (including applications), data, secu ...
Intelligence virtual analyst capability
... analysts is not a lack of data – in some ways they are drowning in data – but rather managing and making sense of the large amount of data being presented to them. This overload problem (at the information and cognition levels) has recently been addressed using a variety of tools that allow extracti ...
... analysts is not a lack of data – in some ways they are drowning in data – but rather managing and making sense of the large amount of data being presented to them. This overload problem (at the information and cognition levels) has recently been addressed using a variety of tools that allow extracti ...
AISB/IACAP World Congress 2012 Natural Computing
... growing in the topology of road networks; chemical oscillations set up to perform boolean operations. What are the relevant abstractions? Are they just the discrete TM again? At this stage in the development of unconventional (or non-Turing) computation, I think that this is the wrong question. Firs ...
... growing in the topology of road networks; chemical oscillations set up to perform boolean operations. What are the relevant abstractions? Are they just the discrete TM again? At this stage in the development of unconventional (or non-Turing) computation, I think that this is the wrong question. Firs ...
AISB/IACAP World Congress 2012 Natural Computing
... growing in the topology of road networks; chemical oscillations set up to perform boolean operations. What are the relevant abstractions? Are they just the discrete TM again? At this stage in the development of unconventional (or non-Turing) computation, I think that this is the wrong question. Firs ...
... growing in the topology of road networks; chemical oscillations set up to perform boolean operations. What are the relevant abstractions? Are they just the discrete TM again? At this stage in the development of unconventional (or non-Turing) computation, I think that this is the wrong question. Firs ...
Diagrammatic Representation and Reasoning: Some Distinctions
... predicates and then proceeding with reasoning as usual, but instead involves projection onto spatial representations and extraction of new predicates. That is, the spatial representation is inextricably involved in the whole process of reasoning. A useful model is one where the agent's cognitive sta ...
... predicates and then proceeding with reasoning as usual, but instead involves projection onto spatial representations and extraction of new predicates. That is, the spatial representation is inextricably involved in the whole process of reasoning. A useful model is one where the agent's cognitive sta ...
A Topic-driven Summarization using K-mean
... system automatically generates a summary of a given document and helps people to make effective decisions in less time. In this paper two methods have been proposed for query-focused multi-document summarization that uses k-mean clustering, term-frequency and inversesentence- frequency method for se ...
... system automatically generates a summary of a given document and helps people to make effective decisions in less time. In this paper two methods have been proposed for query-focused multi-document summarization that uses k-mean clustering, term-frequency and inversesentence- frequency method for se ...
Induction and Decision Trees
... •Objective: find a concise decision tree that agrees with the examples • “concise” instead of “optimal” because the latter is NPcomplete • So we will perform heuristic approximations to the problem • Aiming at getting good solutions but not necessarily optimal •Sometimes the algorithm do generate op ...
... •Objective: find a concise decision tree that agrees with the examples • “concise” instead of “optimal” because the latter is NPcomplete • So we will perform heuristic approximations to the problem • Aiming at getting good solutions but not necessarily optimal •Sometimes the algorithm do generate op ...
Knowledge Engineering 2017
... monsters of the id; they can be used in any possible way for war, invasion of privacy, and human destruction. In this case, machines are only extensions of humans and can be used as their warriors. This issue both leads to and stems from the area of human knowledge ability. Humans must recognize the ...
... monsters of the id; they can be used in any possible way for war, invasion of privacy, and human destruction. In this case, machines are only extensions of humans and can be used as their warriors. This issue both leads to and stems from the area of human knowledge ability. Humans must recognize the ...
Organizing Data and Information
... artificial intelligence that can understand natural language. Learning systems include hardware and software that allows a system to “learn” from the results of its actions or environment – that is, learn from experience. Learning systems require feedback on the results of their actions or decisions ...
... artificial intelligence that can understand natural language. Learning systems include hardware and software that allows a system to “learn” from the results of its actions or environment – that is, learn from experience. Learning systems require feedback on the results of their actions or decisions ...
FREE Sample Here - Find the cheapest test bank for your
... mapped, without any specific improvements or changes to existing processes. ________________________________________ 82. ____________ information encompasses all of the information contained within a single business process or unit of work and its primary purpose is to support the performing of dail ...
... mapped, without any specific improvements or changes to existing processes. ________________________________________ 82. ____________ information encompasses all of the information contained within a single business process or unit of work and its primary purpose is to support the performing of dail ...
Chapter 04 Decision Support and Artificial Intelligence
... 49. What is the difference between an expert system and a genetic algorithm? a. An expert system uses a genetic algorithm to assist in understanding the problem b. An expert system provides more accurate solutions that a genetic algorithm C. A genetic algorithm provides you with the best solution; a ...
... 49. What is the difference between an expert system and a genetic algorithm? a. An expert system uses a genetic algorithm to assist in understanding the problem b. An expert system provides more accurate solutions that a genetic algorithm C. A genetic algorithm provides you with the best solution; a ...
AAAI Proceedings Template - Advances in Cognitive Systems
... researchers have sought to create an artificial system capable of human-like intelligence (McCarthy et. al., 1955). Expert systems using if-then production rules have captured experts’ knowledge and simulated the logical inference of experts in a field of discipline (Hayes-Roth, Waterman, Lenat, 198 ...
... researchers have sought to create an artificial system capable of human-like intelligence (McCarthy et. al., 1955). Expert systems using if-then production rules have captured experts’ knowledge and simulated the logical inference of experts in a field of discipline (Hayes-Roth, Waterman, Lenat, 198 ...
Dimensions of integration in embedded and extended cognitive
... and powerful in problem-solving than an embodied agent without such artifacts. 2 “Brains like ours need media, objects, and other people to function fully as minds” (Sutton 2010, p. 205). On a complementarity view, artifacts or other resources do not just augment existing brain functions by external ...
... and powerful in problem-solving than an embodied agent without such artifacts. 2 “Brains like ours need media, objects, and other people to function fully as minds” (Sutton 2010, p. 205). On a complementarity view, artifacts or other resources do not just augment existing brain functions by external ...
Curriculum Vitae - University of Miami School of Business
... Cell phone: 786 459 4774 Email: [email protected] ...
... Cell phone: 786 459 4774 Email: [email protected] ...
Chapter 02 Strategic Decision Making
... A. By building models out of organizational information to lend insight into important business issues and opportunities B. By building models out of transactional information only to lend insight into important business issues and opportunities C. By building models out of analytical information on ...
... A. By building models out of organizational information to lend insight into important business issues and opportunities B. By building models out of transactional information only to lend insight into important business issues and opportunities C. By building models out of analytical information on ...
Fiqure 4: The Binomail distribution
... With the rapid growth of documents, web pages and other different textual content, great challenges of relatedness have been posed to the current content based systems. Semantic technology plays a vital role and offers a feasible approach to documents management in which it makes possible to retriev ...
... With the rapid growth of documents, web pages and other different textual content, great challenges of relatedness have been posed to the current content based systems. Semantic technology plays a vital role and offers a feasible approach to documents management in which it makes possible to retriev ...
Information Technology and Artificial Intelligence
... Kurzweil believes that the exponential evolution of computation, defined as the capacity to remember and solve problems, is inevitable. Clearly animals, if not life in general, have demonstrated increasing computational abilities throughout evolution. This increasing computational capacity, first wi ...
... Kurzweil believes that the exponential evolution of computation, defined as the capacity to remember and solve problems, is inevitable. Clearly animals, if not life in general, have demonstrated increasing computational abilities throughout evolution. This increasing computational capacity, first wi ...