Beginners Guide to EDI X12 (including HIPAA)
... 3. Usually EDI files are sent over secure connections using encryption/decryption communications. Sometimes not just communications but EDI files are encrypted themselves. Encryption leaves ISA/GS part valid but all segments in the file unreadable. Unless EDI file is decrypted translator will not be ...
... 3. Usually EDI files are sent over secure connections using encryption/decryption communications. Sometimes not just communications but EDI files are encrypted themselves. Encryption leaves ISA/GS part valid but all segments in the file unreadable. Unless EDI file is decrypted translator will not be ...
Powering Your Organization's Web Applications with SAS® Software
... criteria such as which items were selected from a drop-down list or were checked in a group of check boxes. SAS/IntrNet, running on back-end servers, accepts the input from web pages, executes the specified SAS programs, processes data, and sends the result set back to the clients’ web browsers. Org ...
... criteria such as which items were selected from a drop-down list or were checked in a group of check boxes. SAS/IntrNet, running on back-end servers, accepts the input from web pages, executes the specified SAS programs, processes data, and sends the result set back to the clients’ web browsers. Org ...
files - prace
... I/O to only one file and/or to many files Contiguous and non-contiguous I/O Individual and collective I/O Asynchronous I/O ...
... I/O to only one file and/or to many files Contiguous and non-contiguous I/O Individual and collective I/O Asynchronous I/O ...
for COBOL
... can still take advantage of these indexes to retrieve records, while not using them for sorting. This is an architectural limitation, however, in practice does not have significant impact as the SQL engine is able to build temporary index files on the fly when necessary and use dynamic index techniq ...
... can still take advantage of these indexes to retrieve records, while not using them for sorting. This is an architectural limitation, however, in practice does not have significant impact as the SQL engine is able to build temporary index files on the fly when necessary and use dynamic index techniq ...
Backup types and strategies
... modified since the last full or incremental backup. These files will be marked as backed up by turning off their archive bit. Incremental backups are used in conjunction with full/normal backups. This allows a large full backup to be done, followed by much smaller incremental backups. The storage sp ...
... modified since the last full or incremental backup. These files will be marked as backed up by turning off their archive bit. Incremental backups are used in conjunction with full/normal backups. This allows a large full backup to be done, followed by much smaller incremental backups. The storage sp ...
Quick Start Guide
... Acronis is an extremely effective comprehensive data backup and recovery solution — Acronis True Image. It creates a data or disk backup copy stored in a compressed archive file that can be restored in case of an accident. ...
... Acronis is an extremely effective comprehensive data backup and recovery solution — Acronis True Image. It creates a data or disk backup copy stored in a compressed archive file that can be restored in case of an accident. ...
Acronis Disk Director Suite
... partitions — on the disk drive, you now can keep your operating system separate from your applications and data. In fact, each partition can contain its own operating system. How many partitions can I have on my hard disk? Physical hard disks can contain up to four primary partitions or up to three ...
... partitions — on the disk drive, you now can keep your operating system separate from your applications and data. In fact, each partition can contain its own operating system. How many partitions can I have on my hard disk? Physical hard disks can contain up to four primary partitions or up to three ...
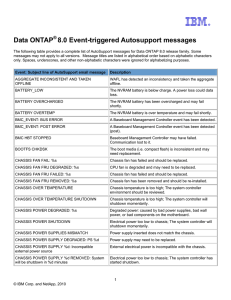
Data ONTAP® 8.0 Event-triggered Autosupport messages
... services is unresponsive. Disk shelf environmental conditions are unknown. ...
... services is unresponsive. Disk shelf environmental conditions are unknown. ...
5th unit OS Notes
... using a specific file organization. The procedure to be used for accessing records in a file, whether by a sequential search or by address calculation, is determined by the file organization. The access method module uses this procedure to access records. It may also use some advanced techniques in ...
... using a specific file organization. The procedure to be used for accessing records in a file, whether by a sequential search or by address calculation, is determined by the file organization. The access method module uses this procedure to access records. It may also use some advanced techniques in ...
MySQL Cluster - Villanova Computer Science
... Data consistency within each cluster is guaranteed as normal, but data consistency across the two clusters is not because of asynchronous ...
... Data consistency within each cluster is guaranteed as normal, but data consistency across the two clusters is not because of asynchronous ...
PowerPoint **
... underlining file system. Sometime divide large file into small sub-files (chunks) for parallel access, which improves the performance ...
... underlining file system. Sometime divide large file into small sub-files (chunks) for parallel access, which improves the performance ...
document
... – AD can be extended to support applications – A number of MS applications utilise AD (Exchange, SMS, ISA to name a ...
... – AD can be extended to support applications – A number of MS applications utilise AD (Exchange, SMS, ISA to name a ...
DANS: Preferred formats
... To create a table, for instance, spreadsheet software will be used more often than a word processor. This is because data tables require specific properties which are better supported by specialized software. This may include the ability to sort data, to use formulas, to set up a filter, and so on. ...
... To create a table, for instance, spreadsheet software will be used more often than a word processor. This is because data tables require specific properties which are better supported by specialized software. This may include the ability to sort data, to use formulas, to set up a filter, and so on. ...
the Nilfs version 1: overview
... In the local file system, there are three kinds of mappings. First, the file block address is mapped to the disk block address. In traditional file systems, it is managed by an index array in the inode structure and by indirect blocks. Second, the inode numbers are mapped to the disk block address c ...
... In the local file system, there are three kinds of mappings. First, the file block address is mapped to the disk block address. In traditional file systems, it is managed by an index array in the inode structure and by indirect blocks. Second, the inode numbers are mapped to the disk block address c ...
Defeating Encrypted and Deniable File Systems
... that a customs agent asks if Alice uses TrueCrypt. The only answer Alice can supply is “yes,” since evidence of TrueCrypt’s usage is stored in the Windows registry (and cannot be safely or reliably deleted, according to the TrueCrypt documentation). Next, suppose that the customs agent asks Alice to ...
... that a customs agent asks if Alice uses TrueCrypt. The only answer Alice can supply is “yes,” since evidence of TrueCrypt’s usage is stored in the Windows registry (and cannot be safely or reliably deleted, according to the TrueCrypt documentation). Next, suppose that the customs agent asks Alice to ...
Defeating Encrypted and Deniable File Systems
... that a customs agent asks if Alice uses TrueCrypt. The only answer Alice can supply is “yes,” since evidence of TrueCrypt’s usage is stored in the Windows registry (and cannot be safely or reliably deleted, according to the TrueCrypt documentation). Next, suppose that the customs agent asks Alice to ...
... that a customs agent asks if Alice uses TrueCrypt. The only answer Alice can supply is “yes,” since evidence of TrueCrypt’s usage is stored in the Windows registry (and cannot be safely or reliably deleted, according to the TrueCrypt documentation). Next, suppose that the customs agent asks Alice to ...
Computer Performance Storage Devices & Size
... A silicon chip is a piece of almost pure silicon, usually less than one centimeter square and about half a millimeter thick. A silicon chip contains millions of transistors (devices that control the flow of electric current) and other tiny electronic circuit components, packed and interconnected in ...
... A silicon chip is a piece of almost pure silicon, usually less than one centimeter square and about half a millimeter thick. A silicon chip contains millions of transistors (devices that control the flow of electric current) and other tiny electronic circuit components, packed and interconnected in ...
Chapter 7 File system data structures
... disk accesses expensive enough to justify this tradeoff. Modern operating systems with larger caches and faster disks use more efficient in-memory data structures. The disk structure, however, with its inodes and direct blocks and indirect blocks, has been remarkably persistent. BSD’s UFS/FFS and Li ...
... disk accesses expensive enough to justify this tradeoff. Modern operating systems with larger caches and faster disks use more efficient in-memory data structures. The disk structure, however, with its inodes and direct blocks and indirect blocks, has been remarkably persistent. BSD’s UFS/FFS and Li ...
Chapter 7 File system data structures
... inode; calls itrunc to truncate the file to zero bytes, freeing the data blocks; sets the type to 0 (unallocated); writes the change to disk; and finally unlocks the inode (39553967). The locking protocol in iput deserves a closer look. The first part with examining is that when locking ip, iput sim ...
... inode; calls itrunc to truncate the file to zero bytes, freeing the data blocks; sets the type to 0 (unallocated); writes the change to disk; and finally unlocks the inode (39553967). The locking protocol in iput deserves a closer look. The first part with examining is that when locking ip, iput sim ...
Project Description Userspace Deduplication File System using FUSE
... Requirement 1: Define and implement the core on-disk data structures and mechanisms required for file and directory creation, retrieval, and destruction (see Table I in the LFS paper [3]). You should document these data structures and fully describe them in your writeup. Requirement 2: Implement a s ...
... Requirement 1: Define and implement the core on-disk data structures and mechanisms required for file and directory creation, retrieval, and destruction (see Table I in the LFS paper [3]). You should document these data structures and fully describe them in your writeup. Requirement 2: Implement a s ...
Fundamentals of Database Systems
... be transferred. Disk rotation moves the block under the readwrite head for reading or writing. A physical disk block (hardware) address consists of a cylinder number (imaginery collection of tracks of same radius from all recoreded surfaces), the track number or surface number (within the cylinder), ...
... be transferred. Disk rotation moves the block under the readwrite head for reading or writing. A physical disk block (hardware) address consists of a cylinder number (imaginery collection of tracks of same radius from all recoreded surfaces), the track number or surface number (within the cylinder), ...