LN29 - WSU EECS
... us: security analysis of cloud management interfaces. In CCSW 2011. [Hacigümüs et al. ICDE’02] H. Hacigümüs et al. Providing database as a ...
... us: security analysis of cloud management interfaces. In CCSW 2011. [Hacigümüs et al. ICDE’02] H. Hacigümüs et al. Providing database as a ...
HOW TO COUNT CURVES: FROM 19th CENTURY PROBLEMS TO
... The origins of topology date from the fundamental work of Euler in the 18th Century and the most basic topological invariant is still named after him. Topology is often referred to as rubber sheet geometry. Consider a ring made from rubber. One can bend and stretch it (cutting is not allowed) and it ...
... The origins of topology date from the fundamental work of Euler in the 18th Century and the most basic topological invariant is still named after him. Topology is often referred to as rubber sheet geometry. Consider a ring made from rubber. One can bend and stretch it (cutting is not allowed) and it ...
Ontology of Quantum Space interpreted by Quantum Real Numbers.
... classical standard real number values. Similarly the quantum distance between a pair of particles may be small even though the classical distance between them is large. According to this theory, the ontology of quantum particles is the same as that of non-relativistic particles of classical mechanic ...
... classical standard real number values. Similarly the quantum distance between a pair of particles may be small even though the classical distance between them is large. According to this theory, the ontology of quantum particles is the same as that of non-relativistic particles of classical mechanic ...
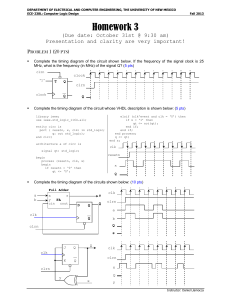
Homework 3 - Daniel Llamocca
... If we want the output bits to change every 1 second (for example) a straightforward solution is to modify the clock frequency to 1 Hz. But this can be a hard problem if a precise input clock is required. ...
... If we want the output bits to change every 1 second (for example) a straightforward solution is to modify the clock frequency to 1 Hz. But this can be a hard problem if a precise input clock is required. ...
PPT - University of Maryland at College Park
... Usually only covers common cases Hard to consider all inputs (may be impossible) Example Bart Miller was able to crash most UNIX utilities with randomly generated inputs ...
... Usually only covers common cases Hard to consider all inputs (may be impossible) Example Bart Miller was able to crash most UNIX utilities with randomly generated inputs ...
munich-2006
... Two readout modes of U2F card through USB: polled: ALTRO data is read channel by channel – SLOW pushed: Data driven – FAST Code: Example C code from the BoNus experiment ...
... Two readout modes of U2F card through USB: polled: ALTRO data is read channel by channel – SLOW pushed: Data driven – FAST Code: Example C code from the BoNus experiment ...
bloggrosholzippoliti072308
... bring a subject matter (logic) into alignment with an algebraic structure; and this task is harder than he thought it was. It requires an adjustment of the algebra, and an adjustment of the subject matter. The task of applying an abstract algebraic structure to a problem in a mathematical domain (wh ...
... bring a subject matter (logic) into alignment with an algebraic structure; and this task is harder than he thought it was. It requires an adjustment of the algebra, and an adjustment of the subject matter. The task of applying an abstract algebraic structure to a problem in a mathematical domain (wh ...
column in IEEE Distributed Systems
... To achieve these goals, we must meet the challenges of providing A syntax for representing metadata Vocabularies for expressing the metadata Metadata for lots of Web pages We're well under way to meeting the first challenge. The W3C (World Wide Web Consortium) has defined such open standards for met ...
... To achieve these goals, we must meet the challenges of providing A syntax for representing metadata Vocabularies for expressing the metadata Metadata for lots of Web pages We're well under way to meeting the first challenge. The W3C (World Wide Web Consortium) has defined such open standards for met ...
MATHS 2016-17 (final).indd
... Contents: Topological Spaces • New Spaces from Old Ones • Connectednes • Compactness • The Separation and Countability Axioms • Special Topics • Metrizability and Paracompactness • The Fundamental Group and Covering Spaces • Applications of Homotopy • Appendix ISBN: 9789380108117 | 406pp | Paperback ...
... Contents: Topological Spaces • New Spaces from Old Ones • Connectednes • Compactness • The Separation and Countability Axioms • Special Topics • Metrizability and Paracompactness • The Fundamental Group and Covering Spaces • Applications of Homotopy • Appendix ISBN: 9789380108117 | 406pp | Paperback ...
Theoretical computer science

Theoretical computer science is a division or subset of general computer science and mathematics that focuses on more abstract or mathematical aspects of computing and includes the theory of computation.It is not easy to circumscribe the theory areas precisely and the ACM's Special Interest Group on Algorithms and Computation Theory (SIGACT) describes its mission as the promotion of theoretical computer science and notes:Template:""To this list, the ACM's journal Transactions on Computation Theory adds coding theory, computational learning theory and theoretical computer science aspects of areas such as databases, information retrieval, economic models and networks. Despite this broad scope, the ""theory people"" in computer science self-identify as different from the ""applied people."" Some characterize themselves as doing the ""(more fundamental) 'science(s)' underlying the field of computing."" Other ""theory-applied people"" suggest that it is impossible to separate theory and application. This means that the so-called ""theory people"" regularly use experimental science(s) done in less-theoretical areas such as software system research. It also means that there is more cooperation than mutually exclusive competition between theory and application.