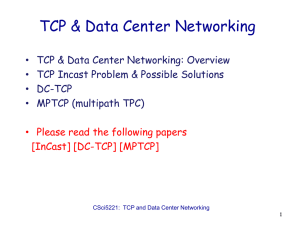
computer networks sample question bank
... secondary ring. In case of failure of a node or a fiber link, the ring is restored the by wrapping up the primary ring to the secondary ring. Further improvement in reliability can achieve by using dual ring of trees and dual homing mechanism. It will provide multiple paths and if one path fails, an ...
... secondary ring. In case of failure of a node or a fiber link, the ring is restored the by wrapping up the primary ring to the secondary ring. Further improvement in reliability can achieve by using dual ring of trees and dual homing mechanism. It will provide multiple paths and if one path fails, an ...
security engineering
... An attacker modifies the recorded packet to check if bit0 of the message is a 0 and sends it on the network. – If the base station responds with an ACK, bit0 is 0. – If the base station responds with a NACK, bit0 is 1. ...
... An attacker modifies the recorded packet to check if bit0 of the message is a 0 and sends it on the network. – If the base station responds with an ACK, bit0 is 0. – If the base station responds with a NACK, bit0 is 1. ...
pptx - CSE Labs User Home Pages
... congestion control work? Maintain a congestion window wr, one window for each path, where r ∊ R ranges over the set of available paths. Design goal 3: - Increase wr for each ACK on path r, by ...
... congestion control work? Maintain a congestion window wr, one window for each path, where r ∊ R ranges over the set of available paths. Design goal 3: - Increase wr for each ACK on path r, by ...
Chapter 1 - Lecturer
... Routing Processes: How Routes Are Learned • Routing requires that every hop, or router, along the path to a packet's destination have a route to forward the packet. • The routing table contains the information to make packet forwarding decisions. • Information is learned in two ways: • Manual confi ...
... Routing Processes: How Routes Are Learned • Routing requires that every hop, or router, along the path to a packet's destination have a route to forward the packet. • The routing table contains the information to make packet forwarding decisions. • Information is learned in two ways: • Manual confi ...
Packet Optical Networking for LTE Cell Tower Backhaul
... Connection-Oriented Ethernet (COE) FAQs What is COE ? Industry term defining a point-to-point implementation of Carrier Ethernet • Tracked by industry analysts for past few years ...
... Connection-Oriented Ethernet (COE) FAQs What is COE ? Industry term defining a point-to-point implementation of Carrier Ethernet • Tracked by industry analysts for past few years ...
Lecture3P1 - UniMAP Portal
... stream delivered error-free and without loss or duplication? Sequencing: Are messages or information stream delivered in order? ARQ protocols combine error detection, retransmission, and sequence numbering to provide reliability & sequencing Examples: TCP and HDLC ...
... stream delivered error-free and without loss or duplication? Sequencing: Are messages or information stream delivered in order? ARQ protocols combine error detection, retransmission, and sequence numbering to provide reliability & sequencing Examples: TCP and HDLC ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... optimized routing length in OLSR, which means that AOHR is immune from topological structures. Sharp Hybrid Adaptive Routing Protocol (SHARP), is designed to dynamically adapt to changing network characteristics and traffic behavior [5]. SHARP is driven by the fundamental trade-off between proactive ...
... optimized routing length in OLSR, which means that AOHR is immune from topological structures. Sharp Hybrid Adaptive Routing Protocol (SHARP), is designed to dynamically adapt to changing network characteristics and traffic behavior [5]. SHARP is driven by the fundamental trade-off between proactive ...
Part 10, CIPHER TECHNIQUES
... – Host enciphers message so host at other end of communication can read it – Message cannot be read at intermediate hosts Slide #10-28 ...
... – Host enciphers message so host at other end of communication can read it – Message cannot be read at intermediate hosts Slide #10-28 ...
Week6LectureNote
... Routing Processes: How Routes Are Learned • Routing requires that every hop, or router, along the path to a packet's destination have a route to forward the packet. • The routing table contains the information to make packet forwarding decisions. • Information is learned in two ways: • Manual confi ...
... Routing Processes: How Routes Are Learned • Routing requires that every hop, or router, along the path to a packet's destination have a route to forward the packet. • The routing table contains the information to make packet forwarding decisions. • Information is learned in two ways: • Manual confi ...
Module 6: Configuring Routing by Using Routing and Remote Access
... A router that is not dedicated to performing routing only, but performs routing as one of multiple processes running on the router computer ...
... A router that is not dedicated to performing routing only, but performs routing as one of multiple processes running on the router computer ...
Streaming
... ignored at the receiver Delay jitter is handled by using timestamps, sequence numbers, and delaying playout at receivers either a fixed or a variable amount With fixed playout delay, the delay should be as ...
... ignored at the receiver Delay jitter is handled by using timestamps, sequence numbers, and delaying playout at receivers either a fixed or a variable amount With fixed playout delay, the delay should be as ...