M. Mirhakkak
... admission control check and computes the bandwidth, within the range (sl, sh), that it can allocate to the flow. Assuming the admission control test passes, the Resv message is propagated upstream towards S. The Resv message also contains a “receiver measurement specification” value, denoted mr. The ...
... admission control check and computes the bandwidth, within the range (sl, sh), that it can allocate to the flow. Assuming the admission control test passes, the Resv message is propagated upstream towards S. The Resv message also contains a “receiver measurement specification” value, denoted mr. The ...
EECC694 - Shaaban
... • BGP is intended for use between networks owned by different organizations (Backbone Providers). • BGP is often referred to as a tool for "policy" routing, because – It may not take into account network constraints such as available bandwidth or network load. – The primary routing protocol that Int ...
... • BGP is intended for use between networks owned by different organizations (Backbone Providers). • BGP is often referred to as a tool for "policy" routing, because – It may not take into account network constraints such as available bandwidth or network load. – The primary routing protocol that Int ...
Document
... After home registration, the MN should initiate a correspondent registration for each node that already appears in the MN’s Binding Update List The initiated procedures can be used to either update or delete binding information in the CN ...
... After home registration, the MN should initiate a correspondent registration for each node that already appears in the MN’s Binding Update List The initiated procedures can be used to either update or delete binding information in the CN ...
SNMP, DHCP and Security
... procedure) is designed to “hide” (work in spite of) these problems. However, retransmission uses bandwidth that could be used for other traffic if the error did not occur. A good network manager will root out such problems before they become more severe. ...
... procedure) is designed to “hide” (work in spite of) these problems. However, retransmission uses bandwidth that could be used for other traffic if the error did not occur. A good network manager will root out such problems before they become more severe. ...
Internet - DePaul University
... Internet Control Message Protocol (ICMP) • ICMP – Used by routers and nodes – Performs error reporting for the Internet Protocol • ICMP reports errors such as invalid IP address, invalid port address, and the packet has hopped too many times ...
... Internet Control Message Protocol (ICMP) • ICMP – Used by routers and nodes – Performs error reporting for the Internet Protocol • ICMP reports errors such as invalid IP address, invalid port address, and the packet has hopped too many times ...
download
... in TCP/IP – Transport entity identification • Generally only one per host • If more than one, then usually one of each type – Specify transport protocol (TCP, UDP) – Host address • An attached network device • In an internet, a global internet address ...
... in TCP/IP – Transport entity identification • Generally only one per host • If more than one, then usually one of each type – Specify transport protocol (TCP, UDP) – Host address • An attached network device • In an internet, a global internet address ...
Solving remote access problems
... • Receive connect from PFL and verify access to resource is allowed • Connect to application server using selected protocol • Act as network layer gateway • Send data back to PFL over SSL ...
... • Receive connect from PFL and verify access to resource is allowed • Connect to application server using selected protocol • Act as network layer gateway • Send data back to PFL over SSL ...
ch20
... The network layer protocol in the TCP/IP protocol suite is currently IPv4. Although IPv4 is well designed, data communication has evolved since the inception of IPv4 in the 1970s. IPv4 has some deficiencies that make it unsuitable for the fast-growing Internet. Topics discussed in this section: ...
... The network layer protocol in the TCP/IP protocol suite is currently IPv4. Although IPv4 is well designed, data communication has evolved since the inception of IPv4 in the 1970s. IPv4 has some deficiencies that make it unsuitable for the fast-growing Internet. Topics discussed in this section: ...
SS7
... load. If one of the STPs fails or isolation occurs because of signaling link failure, the other STP takes the full load until the problem with its mate has been rectified. Integrated STP (SP with STP): combine the functionality of an SSP and an STP. They are both the source and destination for MTP u ...
... load. If one of the STPs fails or isolation occurs because of signaling link failure, the other STP takes the full load until the problem with its mate has been rectified. Integrated STP (SP with STP): combine the functionality of an SSP and an STP. They are both the source and destination for MTP u ...
Signaling and Network Control
... load. If one of the STPs fails or isolation occurs because of signaling link failure, the other STP takes the full load until the problem with its mate has been rectified. Integrated STP (SP with STP): combine the functionality of an SSP and an STP. They are both the source and destination for MTP u ...
... load. If one of the STPs fails or isolation occurs because of signaling link failure, the other STP takes the full load until the problem with its mate has been rectified. Integrated STP (SP with STP): combine the functionality of an SSP and an STP. They are both the source and destination for MTP u ...
EECS 700: Network Security
... – Many firewalls inspect packet without reassemble. If the TCP header is fragmented and the filter rule is based on TCP, it may fail – Firewall examine the SYN bit • Tiny fragment attack: Firewall only check the first fragment. The minimum fragment is 68 bytes (ICMP requirement), but the SYN bit may ...
... – Many firewalls inspect packet without reassemble. If the TCP header is fragmented and the filter rule is based on TCP, it may fail – Firewall examine the SYN bit • Tiny fragment attack: Firewall only check the first fragment. The minimum fragment is 68 bytes (ICMP requirement), but the SYN bit may ...
- Hawking
... If an error occurs: If your PC obtains IP addresses automatically, the Setup Wizard cannot get the PC’s IP to setup its network configuration, IP, etc. To solve the problem, connect your PC to a router with a DHCP server or specify your IP in your IP address in the Windows Network dialog box. For IP ...
... If an error occurs: If your PC obtains IP addresses automatically, the Setup Wizard cannot get the PC’s IP to setup its network configuration, IP, etc. To solve the problem, connect your PC to a router with a DHCP server or specify your IP in your IP address in the Windows Network dialog box. For IP ...
PPT
... • Replace Sp with Sg for outgoing packets • Replace Sg with Sp for incoming packets • How many hosts can have active transfers at one time? Lecture 8: 9-20-01 ...
... • Replace Sp with Sg for outgoing packets • Replace Sg with Sp for incoming packets • How many hosts can have active transfers at one time? Lecture 8: 9-20-01 ...
CSE-555 Protocol Engineering
... Obvious solution to recover from reordered messages Use a large seq # to encode original order of messages With 16-bit seq #, we can number 65,536 subsequent messages How long it takes the counter to wrap around? Example: message length = 128 bits ...
... Obvious solution to recover from reordered messages Use a large seq # to encode original order of messages With 16-bit seq #, we can number 65,536 subsequent messages How long it takes the counter to wrap around? Example: message length = 128 bits ...
2.1 Use case: Login request
... When this section is entered and first form is not edited, on the page will be shown only the first form while other two are forms are disabled and hidden. By submitting the Management general form other two forms will be shown automatically and available for adding/editing. h. Relations section is ...
... When this section is entered and first form is not edited, on the page will be shown only the first form while other two are forms are disabled and hidden. By submitting the Management general form other two forms will be shown automatically and available for adding/editing. h. Relations section is ...
Transmission Control Protocol/Internet Protocol for the PC: an Ethernet implementation
... for the implementation of the communications package Transmission Control Protocol/Internet Protocol for the PC. A User's Manual is included as an appendix. The manual is specifically written for use in the Administrative Sciences Department Informations Systems laboratory at the Naval Postgraduate ...
... for the implementation of the communications package Transmission Control Protocol/Internet Protocol for the PC. A User's Manual is included as an appendix. The manual is specifically written for use in the Administrative Sciences Department Informations Systems laboratory at the Naval Postgraduate ...
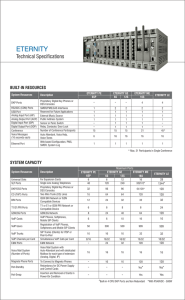
ETERNITY Technical Specifications
... Direct Dialing-In (DDI on T1/E1/PRI) Direct Inward Dialing (DID) Direct Inward System Access (DISA) Direct Outward System Access (DOSA) ...
... Direct Dialing-In (DDI on T1/E1/PRI) Direct Inward Dialing (DID) Direct Inward System Access (DISA) Direct Outward System Access (DOSA) ...
Title Goes Here - Binus Repository
... Sequence number: identifies its place in sequence (byte # in overall message) Acknowledgement number: specifies the next byte # in sequence, if destination does not receive it in X amount of time, will notify sender ...
... Sequence number: identifies its place in sequence (byte # in overall message) Acknowledgement number: specifies the next byte # in sequence, if destination does not receive it in X amount of time, will notify sender ...
unit3
... • TCP uses the connection, not the protocol port, as its fundamental abstraction; connections are identified by a pair of endpoints, i.e., (18.26.0.36, 1069) and (128.10.2.3, 25). • An endpoint is a pair of integers = (host, port). • Because TCP identifies a connection by a pair of endpoints, a give ...
... • TCP uses the connection, not the protocol port, as its fundamental abstraction; connections are identified by a pair of endpoints, i.e., (18.26.0.36, 1069) and (128.10.2.3, 25). • An endpoint is a pair of integers = (host, port). • Because TCP identifies a connection by a pair of endpoints, a give ...
Functions of the Layers
... • The complexity of the communication task is reduced by using multiple protocol layers: • Each protocol is implemented independently • Each protocol is responsible for a specific subtask • Protocols are grouped in a hierarchy • A structured set of protocols is called a communications architecture o ...
... • The complexity of the communication task is reduced by using multiple protocol layers: • Each protocol is implemented independently • Each protocol is responsible for a specific subtask • Protocols are grouped in a hierarchy • A structured set of protocols is called a communications architecture o ...
layers
... » the IP datagram is passed to the ethernet driver which prepares a frame » frame contains destination and source physical addresses but IP datagram in the frame contains the destination IP address of the PC » the frame is broadcast over the ethernet » router picks up the frame and passes the datagr ...
... » the IP datagram is passed to the ethernet driver which prepares a frame » frame contains destination and source physical addresses but IP datagram in the frame contains the destination IP address of the PC » the frame is broadcast over the ethernet » router picks up the frame and passes the datagr ...
Text String Activation
... For single Message Center connection use RS232 wiring method. For multiple Message Center operation use RS485 wiring method. A PLC can be used to send a complete message to one or more Message Centers. Or the PLC can activate a previously loaded message in one or more Message Centers. A PLC can be u ...
... For single Message Center connection use RS232 wiring method. For multiple Message Center operation use RS485 wiring method. A PLC can be used to send a complete message to one or more Message Centers. Or the PLC can activate a previously loaded message in one or more Message Centers. A PLC can be u ...
Chapter 7 outline
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...