Computer network- Chapter 3: Data link layer
... Efforts focus on improving both B and L, both of which will decrease efficiency. In all theatrical researches on performance evaluation of Ethernet, it’s assumed that traffic is Poisson but in real data they are not Poisson, but self similar. ...
... Efforts focus on improving both B and L, both of which will decrease efficiency. In all theatrical researches on performance evaluation of Ethernet, it’s assumed that traffic is Poisson but in real data they are not Poisson, but self similar. ...
Guide to TCP/IP, Third Edition
... – “Steal” bits from network portion of an IP address to “lend” those bits to the host – Permit multiple IP network addresses to be combined – Allow an entire group of hosts to be reached through a single router address ...
... – “Steal” bits from network portion of an IP address to “lend” those bits to the host – Permit multiple IP network addresses to be combined – Allow an entire group of hosts to be reached through a single router address ...
Document
... physical network, such as Ethernet, can have two different protocols at the network layer, such as IP and IPX (Novell), at the same time. Likewise, a packet at a network layer such as IP may pass through different physical networks, such as Ethernet and Token Ring. IP and MAC address need to be mapp ...
... physical network, such as Ethernet, can have two different protocols at the network layer, such as IP and IPX (Novell), at the same time. Likewise, a packet at a network layer such as IP may pass through different physical networks, such as Ethernet and Token Ring. IP and MAC address need to be mapp ...
Chapter 7
... uses its authoritative DNS server to route redirect requests 7: Multimedia Networking 7-45 ...
... uses its authoritative DNS server to route redirect requests 7: Multimedia Networking 7-45 ...
An Overview of the MEF
... be found in the ETSI technical specification TS 145.010 • The radio interface requirement for a GSM base station is frequency accuracy of ±50 ppb and ±100 ppb (pico BS) – The need for this requirement stems primarily from the need to support handover of mobiles between base stations – UMTS FDD Base ...
... be found in the ETSI technical specification TS 145.010 • The radio interface requirement for a GSM base station is frequency accuracy of ±50 ppb and ±100 ppb (pico BS) – The need for this requirement stems primarily from the need to support handover of mobiles between base stations – UMTS FDD Base ...
Slides
... link-state advertisements only in area each nodes has detailed area topology; only know direction (shortest path) to nets in other areas. area border routers: “summarize” distances to nets in own area, advertise to other Area Border routers. backbone routers: run OSPF routing limited to backbone ...
... link-state advertisements only in area each nodes has detailed area topology; only know direction (shortest path) to nets in other areas. area border routers: “summarize” distances to nets in own area, advertise to other Area Border routers. backbone routers: run OSPF routing limited to backbone ...
lecture8
... Add an extra layer: internetworking layer, also called Internet Protocol (IP) - Hosts implement one higher-level protocol - Networks interconnected by nodes that run the same protocol - Provide the interface between the new protocol and every network ...
... Add an extra layer: internetworking layer, also called Internet Protocol (IP) - Hosts implement one higher-level protocol - Networks interconnected by nodes that run the same protocol - Provide the interface between the new protocol and every network ...
Network Layer - Donald Bren School of Information and Computer
... DHCP: Dynamic Host Configuration Protocol goal: allow host to dynamically obtain its IP address from network ...
... DHCP: Dynamic Host Configuration Protocol goal: allow host to dynamically obtain its IP address from network ...
CCNA3 Chapter 2 Single Area OSPF
... • Send updates when a there has been a change in the network topology • Updates contain changes not whole routing table • Calculates shortest path to each route in the network Chapter 2 – Single Area OSPF ...
... • Send updates when a there has been a change in the network topology • Updates contain changes not whole routing table • Calculates shortest path to each route in the network Chapter 2 – Single Area OSPF ...
Avamar Data Store Gen4T
... eliminate node ports and switches as single points of failure. Two separate customer network switches are required, one connected to each of two physical interfaces of an ADS node. Outgoing replication and management networks can be configured for bonding through the additional ports on the utility ...
... eliminate node ports and switches as single points of failure. Two separate customer network switches are required, one connected to each of two physical interfaces of an ADS node. Outgoing replication and management networks can be configured for bonding through the additional ports on the utility ...
Wide Area Networks
... Ñ 3. LECS assign LEC to a ELAN and direct them to a LES Ñ 4. LEC setups up connection to LES and registers addresses Ñ 5. LES assigns a BUS to the LEC Ñ 6. LEC queries LES for a MAC address to ATM address translation Ñ 7. LECS responds directly or forwards query to another LEC Ñ 8. MAC broadcasts ar ...
... Ñ 3. LECS assign LEC to a ELAN and direct them to a LES Ñ 4. LEC setups up connection to LES and registers addresses Ñ 5. LES assigns a BUS to the LEC Ñ 6. LEC queries LES for a MAC address to ATM address translation Ñ 7. LECS responds directly or forwards query to another LEC Ñ 8. MAC broadcasts ar ...
Chapter 2 - SaigonTech
... – First determine how the network will be used, which often decides the topology you use – Decide the types of devices for interconnecting computers and sites – Finally, the type and usage level of network resources dictates how many servers you need and where to place servers ...
... – First determine how the network will be used, which often decides the topology you use – Decide the types of devices for interconnecting computers and sites – Finally, the type and usage level of network resources dictates how many servers you need and where to place servers ...
Introduction to IP Routing
... metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
... metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
Introduction to IP Routing
... metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
... metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
what’s a computer network: “nuts and bolts” view
... Attaining high speed over long distances can be very expensive. Thus, each LAN has a maximum distance it can cover. ...
... Attaining high speed over long distances can be very expensive. Thus, each LAN has a maximum distance it can cover. ...
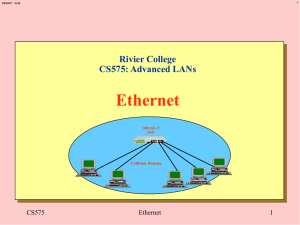
Ethernet Overview
... A bridge performs its functions in the OSI model Data Link layer The device is designed for use between LANs that use identical protocols for the physical and medium access layer (e.g., all conforming to IEEE 802.3 or all conforming to IEEE 802.5) Because the devices all use the same protocols, the ...
... A bridge performs its functions in the OSI model Data Link layer The device is designed for use between LANs that use identical protocols for the physical and medium access layer (e.g., all conforming to IEEE 802.3 or all conforming to IEEE 802.5) Because the devices all use the same protocols, the ...
Packet Marking Schemes
... In the Neighbor Stranger Discrimination (NSD) approach, NSD routers perform signing and filtering functions besides routing. It divides the whole network into neighbors and strangers. If the packets from a network reach the NSD router directly without passing through other NSD routers, this network ...
... In the Neighbor Stranger Discrimination (NSD) approach, NSD routers perform signing and filtering functions besides routing. It divides the whole network into neighbors and strangers. If the packets from a network reach the NSD router directly without passing through other NSD routers, this network ...
lecture24
... So far when considering routing we have considered a “group of routers” and seen how to develop routes between them, and forward packets along those routes. Both distance vector and link state routing have limitations when scaling to very large networks. The amount of information exchanged becomes p ...
... So far when considering routing we have considered a “group of routers” and seen how to develop routes between them, and forward packets along those routes. Both distance vector and link state routing have limitations when scaling to very large networks. The amount of information exchanged becomes p ...
yun-MPLS - KEMT FEI TUKE
... MPLS Components and Protocols MPLS Operation MPLS Protocol Stack Architecture Advantages and Disadvantages ...
... MPLS Components and Protocols MPLS Operation MPLS Protocol Stack Architecture Advantages and Disadvantages ...
CECS470
... • Bootstrap protocol BOOTP: Uses UDP packets which can be forwarded to routers No need for a BOOTP server on each LAN. EECC694 - Shaaban #25 Final Review Spring2000 5-11-2000 ...
... • Bootstrap protocol BOOTP: Uses UDP packets which can be forwarded to routers No need for a BOOTP server on each LAN. EECC694 - Shaaban #25 Final Review Spring2000 5-11-2000 ...
Delay- and Disruption-Tolerant Networks (DTNs)
... The Internet has been a great success at interconnecting communication devices across the Earth. It has done this by using a homogeneous set of communication protocols, called the TCP/IP protocol suite. All devices on the hundreds of thousands of networks that make up the Internet use these protocol ...
... The Internet has been a great success at interconnecting communication devices across the Earth. It has done this by using a homogeneous set of communication protocols, called the TCP/IP protocol suite. All devices on the hundreds of thousands of networks that make up the Internet use these protocol ...
ACL Intro - Chabot College
... – Uses source, destination, protocol, port – Requires more CPU cycles. – Place as close to source as possible. (This stops undesired traffic early.) CISCO NETWORKING ACADEMY ...
... – Uses source, destination, protocol, port – Requires more CPU cycles. – Place as close to source as possible. (This stops undesired traffic early.) CISCO NETWORKING ACADEMY ...
DNS Load Balancing and Failover Mechanism at
... Coyote Point Systems Equalizer and Cisco Catalyst SLB switches, to name just a few, all offer industry standard approaches to these problems. Their solutions are optimized for standard protocol services such as HTTP, FTP or SSH but it remains difficult to extend them for other kinds of application. ...
... Coyote Point Systems Equalizer and Cisco Catalyst SLB switches, to name just a few, all offer industry standard approaches to these problems. Their solutions are optimized for standard protocol services such as HTTP, FTP or SSH but it remains difficult to extend them for other kinds of application. ...