Chapter_10_Final
... defines three address classes for assignment to networks, which support different numbers of networks and hosts. • Because of its wastefulness, classful addressing was gradually made obsolete by a series of subnetting methods, including variable-length subnet masking (VLSM) and eventually Classless ...
... defines three address classes for assignment to networks, which support different numbers of networks and hosts. • Because of its wastefulness, classful addressing was gradually made obsolete by a series of subnetting methods, including variable-length subnet masking (VLSM) and eventually Classless ...
PPT
... – looks for errors, flow control, reliable data transmission, etc – extracts packet, passes to receiving node ...
... – looks for errors, flow control, reliable data transmission, etc – extracts packet, passes to receiving node ...
Interference-Aware Node Disjoint Multi-Path Dynamic Source
... conventions, to name a few has made MANETs popular. Many on-demand [1, 2, 3] and proactive [4, 5] multi-path routing protocols such as AOMDV [6], SR-MPOLSR [7], MP-OLSR [8] were purposed. These protocols did not address the problem of interference from source to destination. Hence interference plays ...
... conventions, to name a few has made MANETs popular. Many on-demand [1, 2, 3] and proactive [4, 5] multi-path routing protocols such as AOMDV [6], SR-MPOLSR [7], MP-OLSR [8] were purposed. These protocols did not address the problem of interference from source to destination. Hence interference plays ...
CENT 305 Information Security
... Small Office/Home Office-Grade (SOHO) Firewall Appliances ◦ Protection for always-on high speed Internet connections ◦ Support stateful inspection, MAC filtering, port forwarding and NAT ◦ May provide intrusion detection capability ...
... Small Office/Home Office-Grade (SOHO) Firewall Appliances ◦ Protection for always-on high speed Internet connections ◦ Support stateful inspection, MAC filtering, port forwarding and NAT ◦ May provide intrusion detection capability ...
router
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
7 Programming client-server communication UDP
... Compared to TCP, UDP has the following disadvantages: Lack of handshaking signals. Before sending a segment, UDP does not use handshaking signals between sending and receiving the transport layer. The sender therefore has no way of knowing whether the datagram reaches the end system. As a result, UD ...
... Compared to TCP, UDP has the following disadvantages: Lack of handshaking signals. Before sending a segment, UDP does not use handshaking signals between sending and receiving the transport layer. The sender therefore has no way of knowing whether the datagram reaches the end system. As a result, UD ...
Integrating Cisco Press Resources into the Academy Classroom
... Models • Networking models define a related set of standards and protocols • When used together, these protocols and standards allow the creation of a working network • The two most commonly used models are the Open Systems Interconnection (OSI) model and the Transmission Control Protocol/Internet P ...
... Models • Networking models define a related set of standards and protocols • When used together, these protocols and standards allow the creation of a working network • The two most commonly used models are the Open Systems Interconnection (OSI) model and the Transmission Control Protocol/Internet P ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... computing in general and to Mobile Adhoc Networks in particular than to any other scientific invention and technological development in recent times in as much as mobile computing is getting vastly expanded since its devices smaller, cheaper and more potent in their functioning are available. The my ...
... computing in general and to Mobile Adhoc Networks in particular than to any other scientific invention and technological development in recent times in as much as mobile computing is getting vastly expanded since its devices smaller, cheaper and more potent in their functioning are available. The my ...
CH3-MPLS-Multiprotocol
... The exponential growth of the Internet over the past several years has placed a tremendous strain on the service provider networks. Not only has there been an increase in the number of users but there has been a multifold increase in connection speeds, backbone traffic and newer applications. Initia ...
... The exponential growth of the Internet over the past several years has placed a tremendous strain on the service provider networks. Not only has there been an increase in the number of users but there has been a multifold increase in connection speeds, backbone traffic and newer applications. Initia ...
ANA - ICSY
... Identify fundamental autonomic networking principles. Design and build an autonomic network architecture. ...
... Identify fundamental autonomic networking principles. Design and build an autonomic network architecture. ...
Chapter09
... Core(config-router)#network 192.168.10.0 Core(config-router)#network 10.0.0.0 Core(config-router)#no auto-summary Core(config-router)#interface ethernet 0 Core(config-if)#ip summary-address eigrp 10 ...
... Core(config-router)#network 192.168.10.0 Core(config-router)#network 10.0.0.0 Core(config-router)#no auto-summary Core(config-router)#interface ethernet 0 Core(config-if)#ip summary-address eigrp 10 ...
Implementation of Simulation to Enhance Wireless Ad
... the task of scheduling a relay node is extremely challenging. There have been methods to implement cooperative communication by handling network state information and channel state information. But it is evident from this discussion that these methods are complex and need a lot of additional signali ...
... the task of scheduling a relay node is extremely challenging. There have been methods to implement cooperative communication by handling network state information and channel state information. But it is evident from this discussion that these methods are complex and need a lot of additional signali ...
The 5 MEF Attributes of Carrier Ethernet & Inter
... including TDM. • Enables converged voice, video & data networks. ...
... including TDM. • Enables converged voice, video & data networks. ...
paper
... (MAC) problem is contention-based protocols in which multiple transmitters simultaneously attempt to access the wireless medium and operate under rules that provide enough opportunities for all nodes to transmit. Examples of such protocols in packet radio networks are ALOHA [3], MACAW [4], and CSMA/ ...
... (MAC) problem is contention-based protocols in which multiple transmitters simultaneously attempt to access the wireless medium and operate under rules that provide enough opportunities for all nodes to transmit. Examples of such protocols in packet radio networks are ALOHA [3], MACAW [4], and CSMA/ ...
module_42 - Faculty Personal Homepage
... Alice sends invite message to her proxy server contains address sip:[email protected] Proxy responsible for routing SIP messages to callee ...
... Alice sends invite message to her proxy server contains address sip:[email protected] Proxy responsible for routing SIP messages to callee ...
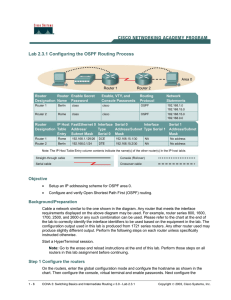
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
OpenFlow: Enabling Research in Production Networks
... Separate intelligence from datapath Operators, users, 3rd party developers, researchers, … ...
... Separate intelligence from datapath Operators, users, 3rd party developers, researchers, … ...
An Introduction to TCP/IP
... is called a routing table. The destination address in the packet header determines the routing table entry that is used to forward the packet. It could be forwarded to a computer attached to the switch that is examining the packet or it could be to another switch in the WAN. ...
... is called a routing table. The destination address in the packet header determines the routing table entry that is used to forward the packet. It could be forwarded to a computer attached to the switch that is examining the packet or it could be to another switch in the WAN. ...
Sockets Programming - Gadjah Mada University
... (PF_INET for TCP/IP). • type specifies the type of service (SOCK_STREAM, SOCK_DGRAM). • protocol specifies the specific protocol (usually 0, which means the default). Netprog: Sockets API ...
... (PF_INET for TCP/IP). • type specifies the type of service (SOCK_STREAM, SOCK_DGRAM). • protocol specifies the specific protocol (usually 0, which means the default). Netprog: Sockets API ...
A DoS-limiting Network Architecture
... Check if their local time > original time stamp + T Check if N bytes have already been used for this connection To tackle this problem, limit the data flow rate (N) as well as the period of validity (T) by returning these values to the sender. Router State is used to count the bytes sent so far. ...
... Check if their local time > original time stamp + T Check if N bytes have already been used for this connection To tackle this problem, limit the data flow rate (N) as well as the period of validity (T) by returning these values to the sender. Router State is used to count the bytes sent so far. ...
Basic Switching and Switch Configuration
... – Increase security by preventing packets between hosts on one side of the router from propagating to the other side of the router CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
... – Increase security by preventing packets between hosts on one side of the router from propagating to the other side of the router CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
CISCO Modes of Operations
... Media type slot#/port# "Media type" shows the type of media that the port is an interface for, e.g. Ethernet, Token Ring, FDDI, serial, etc. Slot numbers are only applicable for routers that provide slots into which we can install modules. These modules contain several different ports for a given me ...
... Media type slot#/port# "Media type" shows the type of media that the port is an interface for, e.g. Ethernet, Token Ring, FDDI, serial, etc. Slot numbers are only applicable for routers that provide slots into which we can install modules. These modules contain several different ports for a given me ...
Chapter_5_V6.01
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...