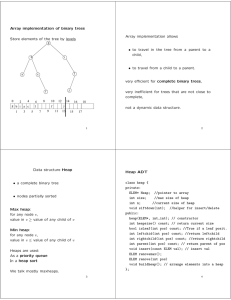
Lecture_12___Heaps_A.. - School of Computer Science
... heapsort is somewhat complex. In practice, heapsort consistently tends to use nearly Nlog N comparisons. ...
... heapsort is somewhat complex. In practice, heapsort consistently tends to use nearly Nlog N comparisons. ...
List
... Summary of the previous lecture • Definition of data, data structure and algorithm • Abstract data types: • Integer (int), • Real (float, double) • Boolen (bool) • Character (char) • Array • Class (class) • Arrays • Features (elements, indexes, numbering) • Adding, deleting, searching ...
... Summary of the previous lecture • Definition of data, data structure and algorithm • Abstract data types: • Integer (int), • Real (float, double) • Boolen (bool) • Character (char) • Array • Class (class) • Arrays • Features (elements, indexes, numbering) • Adding, deleting, searching ...
Data Structures and Object Oriented Programming in C++
... • They should be declared in the public section. • They are invoked automatically when the objects are created. • They do not have return types, not even void and cannot return values. • Constructors cannot be virtual. Like other C++ functions, they can have default arguments 25. Describe the import ...
... • They should be declared in the public section. • They are invoked automatically when the objects are created. • They do not have return types, not even void and cannot return values. • Constructors cannot be virtual. Like other C++ functions, they can have default arguments 25. Describe the import ...
Figure 12-10
... • List traversal is the operation where all elements in the list are processed sequentially, one by one. • Walker point to the element must be processed at a time. • Processing could be retrieval, sorting … etc. • List traversal requires looping algorithm rather than search, loop terminate when all ...
... • List traversal is the operation where all elements in the list are processed sequentially, one by one. • Walker point to the element must be processed at a time. • Processing could be retrieval, sorting … etc. • List traversal requires looping algorithm rather than search, loop terminate when all ...
ch13hashing
... • Hashing as an implementation of the ADT table – For many applications, hashing provides the most efficient implementation – Hashing is not efficient for • Traversal in sorted order • Finding the item with the smallest or largest value in its search key • Range query ...
... • Hashing as an implementation of the ADT table – For many applications, hashing provides the most efficient implementation – Hashing is not efficient for • Traversal in sorted order • Finding the item with the smallest or largest value in its search key • Range query ...
Search Algorithms
... = HTSize – 1. Item with this key inserted in linked list (which may be empty) pointed to by HT[t]. • For nonidentical keys X1 and X2, if h(X1) = h(X2), items with keys X1 and X2 inserted in same linked list • To delete an item R, from hash table, search hash table to find where in linked list R exis ...
... = HTSize – 1. Item with this key inserted in linked list (which may be empty) pointed to by HT[t]. • For nonidentical keys X1 and X2, if h(X1) = h(X2), items with keys X1 and X2 inserted in same linked list • To delete an item R, from hash table, search hash table to find where in linked list R exis ...
57:017, Computers in Engineering Dynamic Data Structures
... a) A node whose data field is greater than the new value has been encountered (currentPtr points at this node) or b) The entire list has been traversed without finding a node whose data portion is greater than the new value. (In this case the new node goes at the end of the list, or becomes the only ...
... a) A node whose data field is greater than the new value has been encountered (currentPtr points at this node) or b) The entire list has been traversed without finding a node whose data portion is greater than the new value. (In this case the new node goes at the end of the list, or becomes the only ...
Skip Lists: A Probabilistic Alternative to Balanced Trees - CMU 15-721
... 1c) requires that no more than n/4 + 2 nodes be examined. If every (2i)th node has a pointer 2i nodes ahead (Figure 1d), the number of nodes that must be examined can be reduced to log2 n while only doubling the number of pointers. This data structure could be used for fast searching, but insert ...
... 1c) requires that no more than n/4 + 2 nodes be examined. If every (2i)th node has a pointer 2i nodes ahead (Figure 1d), the number of nodes that must be examined can be reduced to log2 n while only doubling the number of pointers. This data structure could be used for fast searching, but insert ...
Singly Linked Lists ()
... © 2011 John Wiley & Sons, Data Structures and Algorithms Using Python, by Rance D. Necaise. ...
... © 2011 John Wiley & Sons, Data Structures and Algorithms Using Python, by Rance D. Necaise. ...
File Structures - School of Computing Science
... The work on data bases has been very much concerned with a concept called data independence. The aim of this work is to enable programs to be written independently of the logical structure of the data they would interact with. The independence takes the following form, should the file structure over ...
... The work on data bases has been very much concerned with a concept called data independence. The aim of this work is to enable programs to be written independently of the logical structure of the data they would interact with. The independence takes the following form, should the file structure over ...
Data structure
... newNode = malloc(sizeof(node)); newNode->data = data; 2- Link Next Set the .next pointer of the new node to point to the current first node of the list. newNode->next = head; 3- Link Head Change the head pointer to point to the new node, so it is now the first node in the list. head = newNode; Itera ...
... newNode = malloc(sizeof(node)); newNode->data = data; 2- Link Next Set the .next pointer of the new node to point to the current first node of the list. newNode->next = head; 3- Link Head Change the head pointer to point to the new node, so it is now the first node in the list. head = newNode; Itera ...
Scaling Similarity Joins over Tree-Structured Data
... node in a general rooted ordered labeled tree, a node edit operation (e.g., the deletion of a node) may involve an arbitrary number of changes to the parent-child relationships between nodes. On the other hand, in a binary tree, the number of nodes affected by a node edit operation is strictly const ...
... node in a general rooted ordered labeled tree, a node edit operation (e.g., the deletion of a node) may involve an arbitrary number of changes to the parent-child relationships between nodes. On the other hand, in a binary tree, the number of nodes affected by a node edit operation is strictly const ...
pages - Web Science
... Updates on ISAM Index Structure • ISAM index structure is inherently static. – Deletion is not a big problem: • Simply remove the record from the corresponding data page. • If the removal makes an overflow data page empty, remove that overflow data page. • If the removal makes a primary data page e ...
... Updates on ISAM Index Structure • ISAM index structure is inherently static. – Deletion is not a big problem: • Simply remove the record from the corresponding data page. • If the removal makes an overflow data page empty, remove that overflow data page. • If the removal makes a primary data page e ...
Binary search tree
In computer science, binary search trees (BST), sometimes called ordered or sorted binary trees, are a particular type of containers: data structures that store ""items"" (such as numbers, names and etc.) in memory. They allow fast lookup, addition and removal of items, and can be used to implement either dynamic sets of items, or lookup tables that allow finding an item by its key (e.g., finding the phone number of a person by name).Binary search trees keep their keys in sorted order, so that lookup and other operations can use the principle of binary search: when looking for a key in a tree (or a place to insert a new key), they traverse the tree from root to leaf, making comparisons to keys stored in the nodes of the tree and deciding, based on the comparison, to continue searching in the left or right subtrees. On average, this means that each comparison allows the operations to skip about half of the tree, so that each lookup, insertion or deletion takes time proportional to the logarithm of the number of items stored in the tree. This is much better than the linear time required to find items by key in an (unsorted) array, but slower than the corresponding operations on hash tables.They are a special case of the more general B-tree with order equal to two.