Towards Constant Bandwidth Overhead E.
... We present a trace-hash scheme and an adaptive tree-trace scheme to improve the performance of checking the integrity of arbitrarily-large untrusted data, when using only a small fixed-sized trusted state. Currently, hash trees are used to check the data. In many systems that use hash trees, program ...
... We present a trace-hash scheme and an adaptive tree-trace scheme to improve the performance of checking the integrity of arbitrarily-large untrusted data, when using only a small fixed-sized trusted state. Currently, hash trees are used to check the data. In many systems that use hash trees, program ...
Theory and Practice of Monotone Minimal Perfect Hashing 1
... each structure, which turn out to match very closely the number of bits required in the actual implementations; such estimates are valuable in two ways: they make it possible to tune optimally the parameters (something that would happen modulo a multiplicative constant using big-Oh estimates); and t ...
... each structure, which turn out to match very closely the number of bits required in the actual implementations; such estimates are valuable in two ways: they make it possible to tune optimally the parameters (something that would happen modulo a multiplicative constant using big-Oh estimates); and t ...
Dictionaries and Hash Tables
... In the worst case, searches, insertions and removals on a hash table take O(n) time The worst case occurs when all the keys inserted into the dictionary collide The load factor a = n/N affects the performance of a hash table Assuming that the hash values are like random numbers, it can be shown that ...
... In the worst case, searches, insertions and removals on a hash table take O(n) time The worst case occurs when all the keys inserted into the dictionary collide The load factor a = n/N affects the performance of a hash table Assuming that the hash values are like random numbers, it can be shown that ...
Abstraction and Refinement for Local Reasoning
... constant values and basic arithmetic operations. Similarly, we assume a syntax for boolean expressions B ∈ BExp that includes equality and inequality on value expressions, and standard boolean operators. Definition 2.1 (Programming Language Syntax). Given a set of basic commands Cmd, ranged over by ...
... constant values and basic arithmetic operations. Similarly, we assume a syntax for boolean expressions B ∈ BExp that includes equality and inequality on value expressions, and standard boolean operators. Definition 2.1 (Programming Language Syntax). Given a set of basic commands Cmd, ranged over by ...
Summarizing Large Query Logs in Ettu
... the database schema, and numerous other details that may not be available to Jane immediately when she sits down to analyze a log. As a result, this type of log analysis can quickly become a tedious, time-consuming process. In this paper, we introduce a framework that automatically creates compact, ...
... the database schema, and numerous other details that may not be available to Jane immediately when she sits down to analyze a log. As a result, this type of log analysis can quickly become a tedious, time-consuming process. In this paper, we introduce a framework that automatically creates compact, ...
Full text - Gavin E. Crooks
... Biopython framework for handling FASTA files, sequences for SCOP domains can be quickly returned. So, by calling getSeqRecord on a domain with an instance of the Astral class we can retrieve the relevant sequence. ASTRAL also provides FASTA files containing SCOP domains clustered at percent id of re ...
... Biopython framework for handling FASTA files, sequences for SCOP domains can be quickly returned. So, by calling getSeqRecord on a domain with an instance of the Astral class we can retrieve the relevant sequence. ASTRAL also provides FASTA files containing SCOP domains clustered at percent id of re ...
PeopleSoft Tree Manager
... License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allo ...
... License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allo ...
Chapter 4 Region Algebra Implementation
... Figure 4.8: Different R-trees for the same set of rectangles can have different querying performance. A query for rectangle Q can avoid visiting the C-D subtree in the R-tree on the left, but it must visit all nodes in the R-tree on the right. two nodes, which are then inserted into the grandparent. ...
... Figure 4.8: Different R-trees for the same set of rectangles can have different querying performance. A query for rectangle Q can avoid visiting the C-D subtree in the R-tree on the left, but it must visit all nodes in the R-tree on the right. two nodes, which are then inserted into the grandparent. ...
Algorithms and Compressed Data Structures for Information Retrieval
... by presenting new compressed data structures and algorithms that can be used in different application domains and achieve interesting space/time properties. We propose (i) a new variable-length encoding scheme for sequences of integers that enables fast direct access to the encoded sequence and outpe ...
... by presenting new compressed data structures and algorithms that can be used in different application domains and achieve interesting space/time properties. We propose (i) a new variable-length encoding scheme for sequences of integers that enables fast direct access to the encoded sequence and outpe ...
Approximate Temporal Aggregation
... the number of entries in the new node must be in the range [B⋅Psvu,B⋅Psvo] (Psvu and Psvo are tree parameters). A strong version overflow (underflow) occurs when the number of entries exceeds B⋅Psvo (becomes lower than B⋅Psvu). A strong version overflow is handled by a key split, which is a version- ...
... the number of entries in the new node must be in the range [B⋅Psvu,B⋅Psvo] (Psvu and Psvo are tree parameters). A strong version overflow (underflow) occurs when the number of entries exceeds B⋅Psvo (becomes lower than B⋅Psvu). A strong version overflow is handled by a key split, which is a version- ...
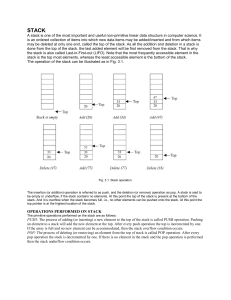
STACK:
... Suppose P is an arithmetic expression written in infix notation. This algorithm finds the equivalent postfix expression Q. Besides operands and operators, P (infix notation) may also contain left and right parentheses. We assume that the operators in P consists of only exponential ( ^ ), multiplicat ...
... Suppose P is an arithmetic expression written in infix notation. This algorithm finds the equivalent postfix expression Q. Besides operands and operators, P (infix notation) may also contain left and right parentheses. We assume that the operators in P consists of only exponential ( ^ ), multiplicat ...
The Quadtree and Related Hierarchical Data Structures
... The origin of the principle of recursive decomposition upon which, as we have said, all quadtrees are based is difficult to ascertain. Below, in order to give some indication of the uses of the quadtree, we briefly, and incompletely, trace some of its applications to geometric data. Most likely it w ...
... The origin of the principle of recursive decomposition upon which, as we have said, all quadtrees are based is difficult to ascertain. Below, in order to give some indication of the uses of the quadtree, we briefly, and incompletely, trace some of its applications to geometric data. Most likely it w ...
Binary search tree
In computer science, binary search trees (BST), sometimes called ordered or sorted binary trees, are a particular type of containers: data structures that store ""items"" (such as numbers, names and etc.) in memory. They allow fast lookup, addition and removal of items, and can be used to implement either dynamic sets of items, or lookup tables that allow finding an item by its key (e.g., finding the phone number of a person by name).Binary search trees keep their keys in sorted order, so that lookup and other operations can use the principle of binary search: when looking for a key in a tree (or a place to insert a new key), they traverse the tree from root to leaf, making comparisons to keys stored in the nodes of the tree and deciding, based on the comparison, to continue searching in the left or right subtrees. On average, this means that each comparison allows the operations to skip about half of the tree, so that each lookup, insertion or deletion takes time proportional to the logarithm of the number of items stored in the tree. This is much better than the linear time required to find items by key in an (unsorted) array, but slower than the corresponding operations on hash tables.They are a special case of the more general B-tree with order equal to two.