EE579T-Class 8 - Electrical & Computer Engineering
... Dial-Up Servers • Can easily provide back door into LAN if dial-up used on a modem connection • Modem allows password enumeration and guessing, just as on the broadband side • Intruders can attack what they find – Can’t go further because Win9x can’t route network traffic ...
... Dial-Up Servers • Can easily provide back door into LAN if dial-up used on a modem connection • Modem allows password enumeration and guessing, just as on the broadband side • Intruders can attack what they find – Can’t go further because Win9x can’t route network traffic ...
CPS Operations Guide
... The passive or standby load balancer is the system which does not have active VIPs. ...
... The passive or standby load balancer is the system which does not have active VIPs. ...
Lookup Service - University of Connecticut
... JINI Lookup Service Maintains Registry for Available Services of Distributed Application Resources Provide Services that Register and Join with JINI Lookup Service Clients Discover and Utilize Services Based on Interface of Services Ask Lookup for RegisterForCourse(CSE900) Return Proxy for Execu ...
... JINI Lookup Service Maintains Registry for Available Services of Distributed Application Resources Provide Services that Register and Join with JINI Lookup Service Clients Discover and Utilize Services Based on Interface of Services Ask Lookup for RegisterForCourse(CSE900) Return Proxy for Execu ...
Efficient Way of iSCSI based Remote Storage Service for
... client I/O request by block management module of intermediate server. In case of read request, block management module searches requested block in iSCSI buffer to service the requested block with target module. If the requested block exists in iSCSI buffer, target module of intermediate server reply ...
... client I/O request by block management module of intermediate server. In case of read request, block management module searches requested block in iSCSI buffer to service the requested block with target module. If the requested block exists in iSCSI buffer, target module of intermediate server reply ...
DHCP Server and Client for FieldServer
... The FieldServer probes the Ethernet network for other DHCP Servers every 3 minutes and will disable the FieldServer’s own DHCP Server until a restart should one or more external DHCP Servers be found. This is done to prevent interference on the network. The probe is done on each Ethernet adapter and ...
... The FieldServer probes the Ethernet network for other DHCP Servers every 3 minutes and will disable the FieldServer’s own DHCP Server until a restart should one or more external DHCP Servers be found. This is done to prevent interference on the network. The probe is done on each Ethernet adapter and ...
This chapter covers the following topics: • Characteristics of roaming
... The mechanism to determine when to roam is not defined by the IEEE 802.11 specification and is, therefore, left to vendors to implement. Although this issue posed an interoperability challenge early on with the first 802.11 products, vendors work together today to ensure basic interoperability. The fac ...
... The mechanism to determine when to roam is not defined by the IEEE 802.11 specification and is, therefore, left to vendors to implement. Although this issue posed an interoperability challenge early on with the first 802.11 products, vendors work together today to ensure basic interoperability. The fac ...
... WPA-Enterprise configured, the new client will be requested to enter a username with a password. If the new client is authorized by the administration, and enters the correct username and password, then access is granted. In the case where an employee leaves the company, the network administrator is ...
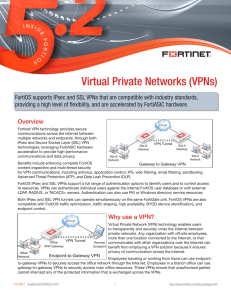
Virtual Private Networks (VPNs)
... access control, security profiles, and endpoint control. Some networks, such as those available in public spaces, may block IPsec protocols, thereby preventing IPsec endpoints from accessing their IPsec VPN gateways. An SSL VPN is the only workaround in this situation, since the HTTPS protocol used ...
... access control, security profiles, and endpoint control. Some networks, such as those available in public spaces, may block IPsec protocols, thereby preventing IPsec endpoints from accessing their IPsec VPN gateways. An SSL VPN is the only workaround in this situation, since the HTTPS protocol used ...
ch08
... Introducing DHCP • DHCP – Service that provides a way for client computer to request IP address assignment – Delivers necessary configuration information to clients – Traces its origins back to an earlier protocol named BOOTP – Servers can manage one or more ranges of IP addresses ...
... Introducing DHCP • DHCP – Service that provides a way for client computer to request IP address assignment – Delivers necessary configuration information to clients – Traces its origins back to an earlier protocol named BOOTP – Servers can manage one or more ranges of IP addresses ...
PDF
... Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of t ...
... Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of t ...
document
... • Consider NNTP (Network News Transport Protocol): – Does not follow the client-server model – Uses precollection ...
... • Consider NNTP (Network News Transport Protocol): – Does not follow the client-server model – Uses precollection ...
ppt
... • Use UDP multicast when retransmitting a message if several processes lack a copy – For example, if solicited twice – Also, if a retransmission is received from “far away” ...
... • Use UDP multicast when retransmitting a message if several processes lack a copy – For example, if solicited twice – Also, if a retransmission is received from “far away” ...
Test_King_CompTIA_N1..
... The workstation is not running the Microsoft Client for NetWare Networks. ...
... The workstation is not running the Microsoft Client for NetWare Networks. ...
Presentation 2
... • Hub based network • Reduces the signaling load without reducing the reliability • Election process to select an assign Superpeers • Superpeers: high degree (degree>>20, depending on network size) • Leafnodes: connected to one or more Superpeers (degree<7) ...
... • Hub based network • Reduces the signaling load without reducing the reliability • Election process to select an assign Superpeers • Superpeers: high degree (degree>>20, depending on network size) • Leafnodes: connected to one or more Superpeers (degree<7) ...
UCam247 Operational Manual
... The camera provides the ability to view the cameras monitored through your mobile phone as a live video stream, it supports the telecommunications standard of 3GPP streaming format. All 3G enabled mobile devices and most 2G phones that support the streaming standard of 3GPP are compatible. ...
... The camera provides the ability to view the cameras monitored through your mobile phone as a live video stream, it supports the telecommunications standard of 3GPP streaming format. All 3G enabled mobile devices and most 2G phones that support the streaming standard of 3GPP are compatible. ...
Oracle RAC From Dream To Production
... This solution allows you to build scalable and high available database system only with common Intel PCs connected into Ethernet network. In this solution, a standard shared disk subsystem is replaced by a native Linux technology - Network Block Device (NBD) that maps remote files to local block ...
... This solution allows you to build scalable and high available database system only with common Intel PCs connected into Ethernet network. In this solution, a standard shared disk subsystem is replaced by a native Linux technology - Network Block Device (NBD) that maps remote files to local block ...
Installation Guide for Avaya Scopia® Desktop Server
... materials available to You. “Software” means computer programs in object code, provided by Avaya or an Avaya Channel Partner, whether as stand-alone products, pre-installed on hardware products, and any upgrades, updates, patches, bug fixes, or modified versions thereto. “Designated Processor” means ...
... materials available to You. “Software” means computer programs in object code, provided by Avaya or an Avaya Channel Partner, whether as stand-alone products, pre-installed on hardware products, and any upgrades, updates, patches, bug fixes, or modified versions thereto. “Designated Processor” means ...
SoftRouter Plus User Guide
... Here we describe each Chapter and its contents. Chapter 2 describes the SoftRouter PlusÕs scenarios and configuration options. While Chapter 3 describes how the SoftRouter Plus works with Open Transport. Chapters 4 and 5 provide reference material on the SoftRouter PlusÕs operating and configuration ...
... Here we describe each Chapter and its contents. Chapter 2 describes the SoftRouter PlusÕs scenarios and configuration options. While Chapter 3 describes how the SoftRouter Plus works with Open Transport. Chapters 4 and 5 provide reference material on the SoftRouter PlusÕs operating and configuration ...
Pulse Secure Client Error Messages
... Long-desc = Wireless suppression has been enabled by administrator. The 802.1x wireless networks are suppressed when a valid wired network is detected. ; JUNS catalogUtil requires catalog message files to be saved with UTF-8 encoding, which put 3 bytes {0xEF, 0xBB, 0xBF} at the file beginning called ...
... Long-desc = Wireless suppression has been enabled by administrator. The 802.1x wireless networks are suppressed when a valid wired network is detected. ; JUNS catalogUtil requires catalog message files to be saved with UTF-8 encoding, which put 3 bytes {0xEF, 0xBB, 0xBF} at the file beginning called ...
Mobile - CSE, IIT Bombay
... • How many times to retransmit at the link level before giving up? • What triggers link level retransmissions? • How much time is required for a link layer retransmission? • Should the link layer deliver packets as they arrive, or deliver them in-order? ...
... • How many times to retransmit at the link level before giving up? • What triggers link level retransmissions? • How much time is required for a link layer retransmission? • Should the link layer deliver packets as they arrive, or deliver them in-order? ...
Keywords - multi-touch, RFID, interactive, front-side
... Fig. 3 Multi-touch table outside and inside view. 3.1.1 Camera-based multi-touch techniques Camera based multi-touch devices share the same concept of processing and filtering captured images on patterns. The pipeline begins when the user views the scene on the panel and decides to interact. To inte ...
... Fig. 3 Multi-touch table outside and inside view. 3.1.1 Camera-based multi-touch techniques Camera based multi-touch devices share the same concept of processing and filtering captured images on patterns. The pipeline begins when the user views the scene on the panel and decides to interact. To inte ...
Framework
... You work as the security administrator at King.com. King.com has been receiving a high volume of attacks on the king.com web site. You want to collect information on the attackers so that legal action can be taken. Which of the following can you use to accomplish this? a) ...
... You work as the security administrator at King.com. King.com has been receiving a high volume of attacks on the king.com web site. You want to collect information on the attackers so that legal action can be taken. Which of the following can you use to accomplish this? a) ...
STAAR Online Testing Platform Technology Guide
... directly through the Internet. Students access their tests using the STAAR Online Testing Platform. All workstations where tests are administered must have reliable Internet connectivity. Diagnostic testing may determine that the district’s network has unreliable Internet connectivity, low bandwidth ...
... directly through the Internet. Students access their tests using the STAAR Online Testing Platform. All workstations where tests are administered must have reliable Internet connectivity. Diagnostic testing may determine that the district’s network has unreliable Internet connectivity, low bandwidth ...