iptables-1-updated
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
Multicast
... Spanning trees rooted at the sender When a receiver wants to join a group, may have to ...
... Spanning trees rooted at the sender When a receiver wants to join a group, may have to ...
Scap: Stream-Oriented Network Traffic Capture and
... several cases of applications that are simply not interested in some packets, such as the tails of large flows [9, 26, 27, 33]. Subzero packet copy identifies these packets and does not bring them in main memory at all: they are dropped by the network interface card (NIC) before reaching the main me ...
... several cases of applications that are simply not interested in some packets, such as the tails of large flows [9, 26, 27, 33]. Subzero packet copy identifies these packets and does not bring them in main memory at all: they are dropped by the network interface card (NIC) before reaching the main me ...
TCP/IP Illustrated - UTN
... (Numerous fine points are missing from this figure that will be discussed in the appropriate chapter. For example, both the DNS and RPC use TCP, which we don't show.) We take a bottom-up approach to the TCP/IP protocol suite. After providing a basic introduction to TCP/IP in Chapter 1, we will start ...
... (Numerous fine points are missing from this figure that will be discussed in the appropriate chapter. For example, both the DNS and RPC use TCP, which we don't show.) We take a bottom-up approach to the TCP/IP protocol suite. After providing a basic introduction to TCP/IP in Chapter 1, we will start ...
Unix System Administration
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
Communications Server for z/OS V1R2 TCP/IP
... IBM Corporation, International Technical Support Organization Dept. HZ8 Building 662 P.O. Box 12195 Research Triangle Park, NC 27709-2195 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring an ...
... IBM Corporation, International Technical Support Organization Dept. HZ8 Building 662 P.O. Box 12195 Research Triangle Park, NC 27709-2195 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring an ...
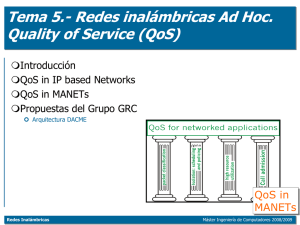
Redes Inalámbricas
... The MANET paradigm is based on user cooperation, but in most cases we can not force users to cooperate ...
... The MANET paradigm is based on user cooperation, but in most cases we can not force users to cooperate ...
Unix System Administration
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
Hack Attacks Revealed
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
Hack Attacks Revealed
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
Lab – Configuring Dynamic and Static NAT (Instructor Version)
... Inside global / local: ________________ 1034, answers will vary. Outside global / local: ________________ 23 d. Because static NAT was configured for PC-A, verify that pinging from ISP to PC-A at the static NAT public address (209.165.200.225) is successful. e. On the Gateway router, display the NAT ...
... Inside global / local: ________________ 1034, answers will vary. Outside global / local: ________________ 23 d. Because static NAT was configured for PC-A, verify that pinging from ISP to PC-A at the static NAT public address (209.165.200.225) is successful. e. On the Gateway router, display the NAT ...
Implementation of IPv6 ToS over ATM Network
... fields set to values between 8 and 15 (inclusive). The rationale behind the selection is that CBR service can carry all the data through the ATM network with minimal loss at a constant rate, which is the characteristic of most real-time voice and video signals. However, the use of CBR does not allow ...
... fields set to values between 8 and 15 (inclusive). The rationale behind the selection is that CBR service can carry all the data through the ATM network with minimal loss at a constant rate, which is the characteristic of most real-time voice and video signals. However, the use of CBR does not allow ...
here - BITS Embryo
... – Initiator executes “SendTargets” command after establishing the session • This is the only command supported for a Discovery session ...
... – Initiator executes “SendTargets” command after establishing the session • This is the only command supported for a Discovery session ...
Networking on z/OS
... defined as the hardware and software that enables computers to share files and resources and exchange data. Depending on the size of a business, a network can be as simple as two personal computers on a locally connected network or as complex as the Internet, a worldwide network of millions of compu ...
... defined as the hardware and software that enables computers to share files and resources and exchange data. Depending on the size of a business, a network can be as simple as two personal computers on a locally connected network or as complex as the Internet, a worldwide network of millions of compu ...
2. HBR Overview - Computer Science, Columbia University
... RTP/UDP whereas non-real-time traffic has traditionally been carried over TCP. SIP-based terminal mobility provides a means of subnet and domain hand-off while a session is in progress. The SIP-based scheme provides a different approach to achieving terminal mobility by means of application layer si ...
... RTP/UDP whereas non-real-time traffic has traditionally been carried over TCP. SIP-based terminal mobility provides a means of subnet and domain hand-off while a session is in progress. The SIP-based scheme provides a different approach to achieving terminal mobility by means of application layer si ...
pdf
... simulation framework to evaluate the impact of interference for a pair of 802.11b nodes and a pair of Bluetooth nodes. Similar results have been obtained by Lansford et al. [22] for the case of coexisting 802.11b and Bluetooth devices on the same laptop. Their simulation models are based on a link b ...
... simulation framework to evaluate the impact of interference for a pair of 802.11b nodes and a pair of Bluetooth nodes. Similar results have been obtained by Lansford et al. [22] for the case of coexisting 802.11b and Bluetooth devices on the same laptop. Their simulation models are based on a link b ...
Institutionen för systemteknik Department of Electrical Engineering Implementation of a VBR MPEG-stream
... The sync byte indicates start of a TS-packet and is always the first byte in a header with the value 0x47. Following are a number of flags and the Packet Identifier (PID). When using CBR streams, empty packets are included as described earlier; such an empty packet has the PID set to 0x1FFF, which i ...
... The sync byte indicates start of a TS-packet and is always the first byte in a header with the value 0x47. Following are a number of flags and the Packet Identifier (PID). When using CBR streams, empty packets are included as described earlier; such an empty packet has the PID set to 0x1FFF, which i ...
Multimedia Streaming File
... then, fill rate = constant rate - packet loss short playout delay (2-5 seconds) to compensate for network delay jitter error recover: time permitting ...
... then, fill rate = constant rate - packet loss short playout delay (2-5 seconds) to compensate for network delay jitter error recover: time permitting ...
SpeedStream Router
... reverse engineer, disassemble or otherwise reduce the Software or any part thereof to a human perceivable form; modify, adapt, translate or create derivative works based upon the Software or any part thereof; or rent, lease, loan or otherwise operate for profit the Software. 3. Transfer. You may tra ...
... reverse engineer, disassemble or otherwise reduce the Software or any part thereof to a human perceivable form; modify, adapt, translate or create derivative works based upon the Software or any part thereof; or rent, lease, loan or otherwise operate for profit the Software. 3. Transfer. You may tra ...
Jigsaw: Solving the Puzzle of Enterprise 802.11 Analysis
... But most 11b traffic are bursty, no need to use protection all the time ...
... But most 11b traffic are bursty, no need to use protection all the time ...
VoIP
... for every group of n PDU’s , create redundant PDU by exclusive OR-ing n original PDU’s send n+1 PDU’s, increasing bandwidth by factor 1/n can reconstruct original n PDU’s if at most one lost chunk from n+1 PDU’s, with playout delay ...
... for every group of n PDU’s , create redundant PDU by exclusive OR-ing n original PDU’s send n+1 PDU’s, increasing bandwidth by factor 1/n can reconstruct original n PDU’s if at most one lost chunk from n+1 PDU’s, with playout delay ...
PPT - CS.Duke
... Distance Vector Multicast Routing Protocol • Using existing distance vector routing protocol • Establish multicast forwarding state – Flood to all destinations (reverse path flooding) • Key design challenge: loop-avoidance • Q: how many broadcast loop-avoidance mechanisms have we learned? – Prone t ...
... Distance Vector Multicast Routing Protocol • Using existing distance vector routing protocol • Establish multicast forwarding state – Flood to all destinations (reverse path flooding) • Key design challenge: loop-avoidance • Q: how many broadcast loop-avoidance mechanisms have we learned? – Prone t ...