Document
... even controls it entirely. • It is made up of many smaller networks. • These smaller networks are often owned and managed by a person or organization. • The Internet, then, is really defined by how connections can be made between these networks. ...
... even controls it entirely. • It is made up of many smaller networks. • These smaller networks are often owned and managed by a person or organization. • The Internet, then, is really defined by how connections can be made between these networks. ...
Introduction to Networking Protocols and Architecture
... ASCII Text, Sound Establish/manage connection End-to-end communication: TCP Routing, Addressing: IP Two party communication: Ethernet How to transmit signal: Coding ...
... ASCII Text, Sound Establish/manage connection End-to-end communication: TCP Routing, Addressing: IP Two party communication: Ethernet How to transmit signal: Coding ...
TCP/IP
... Developed by DARPA (Defense Advanced Research Projects) TCP is a connection-oriented transport protocol that sends data as an unstructured stream of bytes. By using sequence numbers and acknowledgment messages, TCP can provide a sending node with delivery information about packets transmitted to ...
... Developed by DARPA (Defense Advanced Research Projects) TCP is a connection-oriented transport protocol that sends data as an unstructured stream of bytes. By using sequence numbers and acknowledgment messages, TCP can provide a sending node with delivery information about packets transmitted to ...
Our Catalog of Multi-Platform Data
... Time Clock Devices Biometric Barcode Magnetic Stripe Key-in Proximity (HID) ...
... Time Clock Devices Biometric Barcode Magnetic Stripe Key-in Proximity (HID) ...
Comparison and Contrast between the OSI and TCP/IP Model
... providing a reliable data transfer service, while the TCP/IP model treats reliability as an end-to-end problem. Each layer of the OSI model detects and handles errors, all data transmitted includes checksums. The transport layer of the OSI model checks source-to-destination reliability. In the T ...
... providing a reliable data transfer service, while the TCP/IP model treats reliability as an end-to-end problem. Each layer of the OSI model detects and handles errors, all data transmitted includes checksums. The transport layer of the OSI model checks source-to-destination reliability. In the T ...
Mapping of scalable RDMA protocols to ASIC/FPGA
... • Data indicate that most of the key cores will fit one FPGA device (Virtex-II) • Aggregate of all cores is spanning several FPGAs • Intra-device communication is a issue, need to be careful with PCB design. • We are currently trying to accommodate most of the cores in one FPGA. •Most of the cores w ...
... • Data indicate that most of the key cores will fit one FPGA device (Virtex-II) • Aggregate of all cores is spanning several FPGAs • Intra-device communication is a issue, need to be careful with PCB design. • We are currently trying to accommodate most of the cores in one FPGA. •Most of the cores w ...
Networking Basics Introducing Basic Network Concepts *In the
... • In addition to using the information contained in the headers, for the basic functions of data segmentation and reassembly, some protocols at the Transport layer provide: ...
... • In addition to using the information contained in the headers, for the basic functions of data segmentation and reassembly, some protocols at the Transport layer provide: ...
Network Architectures - Computing Sciences
... Header Checksum (16 bits) – Used to detect errors in IP header only – Since ‘Time to Die’ changes at each hop, checksum is also recomputed ...
... Header Checksum (16 bits) – Used to detect errors in IP header only – Since ‘Time to Die’ changes at each hop, checksum is also recomputed ...
Introduction to Multimedia Systems
... – UDP (User Datagram Protocol): A simple protocol for short delay and unreliable communication. – TCP (Transmission Control Protocol): A much more complex protocol that guarantees correct data transmission. • By acknowledgement from the receiver. • Retransmission if time is out or data is corrupted. ...
... – UDP (User Datagram Protocol): A simple protocol for short delay and unreliable communication. – TCP (Transmission Control Protocol): A much more complex protocol that guarantees correct data transmission. • By acknowledgement from the receiver. • Retransmission if time is out or data is corrupted. ...
PowerPoint 簡報
... package from networking, converter to Email, Hotmail, Web-mail, FTP, IM MSN/ICQ/AOL/Yahoo/QQ, Telnet and Website Browsing such protocol. ...
... package from networking, converter to Email, Hotmail, Web-mail, FTP, IM MSN/ICQ/AOL/Yahoo/QQ, Telnet and Website Browsing such protocol. ...
UDP
... IP datagram format IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to ...
... IP datagram format IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to ...
Transmission Control Protocol (TCP)
... TCP/IP Protocol Suite (2) Point-to-Point Protocol (PPP): a link layer protocol used in the Internet Address Resolution Protocol (ARP): IP address Ethernet address Reverse Address Resolution Protocol (RARP): Ethernet address IP address Bootstrap Protocol (BOOTP): function is similar to RARP, but ...
... TCP/IP Protocol Suite (2) Point-to-Point Protocol (PPP): a link layer protocol used in the Internet Address Resolution Protocol (ARP): IP address Ethernet address Reverse Address Resolution Protocol (RARP): Ethernet address IP address Bootstrap Protocol (BOOTP): function is similar to RARP, but ...
Practice questions for exam
... 52. What are the four layers of the TCP/IP Model? 53. List four multiple access methods/technologies. 54. Besides bandwidth and latency, what other parameter is needed to give a good characterization of the quality of service offered by a network used for (i) digitized voice traffic? (ii) video traf ...
... 52. What are the four layers of the TCP/IP Model? 53. List four multiple access methods/technologies. 54. Besides bandwidth and latency, what other parameter is needed to give a good characterization of the quality of service offered by a network used for (i) digitized voice traffic? (ii) video traf ...
Network Layer - CIS @ Temple University
... fragments got through, assembles them into a datagram and delivers it to the destination transport layer. ...
... fragments got through, assembles them into a datagram and delivers it to the destination transport layer. ...
Week 1 - cda college
... • Physical: Transmit raw bits over the medium. • Data Link: Implements the abstraction of an error free medium (handle losses, duplication, errors, flow control). • Network: Routing and Addressing. IP • Transport: Break up data into chunks, send them down the protocol stack, receive chunks, put the ...
... • Physical: Transmit raw bits over the medium. • Data Link: Implements the abstraction of an error free medium (handle losses, duplication, errors, flow control). • Network: Routing and Addressing. IP • Transport: Break up data into chunks, send them down the protocol stack, receive chunks, put the ...
Lecture 6
... Layers of a Network • Networking is complex • Networking is divided into several layers • Each layer represents a different level of abstraction between the physical hardware and the information to be transmitted • Layering: the grouping of the communication functions into related and manageable se ...
... Layers of a Network • Networking is complex • Networking is divided into several layers • Each layer represents a different level of abstraction between the physical hardware and the information to be transmitted • Layering: the grouping of the communication functions into related and manageable se ...
Data Link Layer
... The MAC Layer enables multiple devices to share the media MAC sub-layer maintains physical device addresses for communicating with other devices (commonly referred to as MAC addresses) Most LANs have more than one computer, and the MAC sub-layer determines who may speak and when ...
... The MAC Layer enables multiple devices to share the media MAC sub-layer maintains physical device addresses for communicating with other devices (commonly referred to as MAC addresses) Most LANs have more than one computer, and the MAC sub-layer determines who may speak and when ...
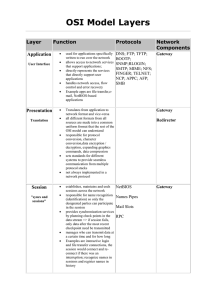
OSI Model Layers
... manages the flow control of data between parties across the network divides streams of data into chunks or packets; the transport layer of the receiving computer reassembles the message from packets "train" is a good analogy => the data is divided into identical units provides error-checking to guar ...
... manages the flow control of data between parties across the network divides streams of data into chunks or packets; the transport layer of the receiving computer reassembles the message from packets "train" is a good analogy => the data is divided into identical units provides error-checking to guar ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).