IP Routing - courses.psu.edu
... – All communication occur on the one local net segment – Network source and destination infromation is not needed. – NetBEUI (NetBIOS Enhanced User Interface). ...
... – All communication occur on the one local net segment – Network source and destination infromation is not needed. – NetBEUI (NetBIOS Enhanced User Interface). ...
MPLS
... Each switch needs a table that contains the actions it is to perform when a given label arrives. The downstream end of a link needs to know what label values will be sent. This can be done by management action – directly equivalent to PVC’s in ATM. But this does not scale well. And there i ...
... Each switch needs a table that contains the actions it is to perform when a given label arrives. The downstream end of a link needs to know what label values will be sent. This can be done by management action – directly equivalent to PVC’s in ATM. But this does not scale well. And there i ...
Cisco Nexus 3048 Switch Product Overview
... Cisco NX-OS, which consist of the Cisco Nexus Family of products. Cisco DCNM is a Cisco management solution that increases overall data center infrastructure uptime and reliability, hence improving business continuity. Focused on the management requirements of the data center network, Cisco DCNM pro ...
... Cisco NX-OS, which consist of the Cisco Nexus Family of products. Cisco DCNM is a Cisco management solution that increases overall data center infrastructure uptime and reliability, hence improving business continuity. Focused on the management requirements of the data center network, Cisco DCNM pro ...
Slide 1
... • 1st-Generation VPN – IPsec – IP Address-Based Tunnels – All-or-Nothing Network Access for Employees ...
... • 1st-Generation VPN – IPsec – IP Address-Based Tunnels – All-or-Nothing Network Access for Employees ...
- IEEE Mentor
... be limited to less than 6 hops and frequently less than that. Setting up such simple tree structures is quick and efficient and so is their maintenance. For more complex deployments, the basic tree connectivity obtained from link level discovery messages can be used in combination with a spanning tr ...
... be limited to less than 6 hops and frequently less than that. Setting up such simple tree structures is quick and efficient and so is their maintenance. For more complex deployments, the basic tree connectivity obtained from link level discovery messages can be used in combination with a spanning tr ...
document
... • Consider NNTP (Network News Transport Protocol): – Does not follow the client-server model – Uses precollection ...
... • Consider NNTP (Network News Transport Protocol): – Does not follow the client-server model – Uses precollection ...
What are the advantages to organizations of using computer networks
... 77) The personal dictation software is classed as _________________ recognition system a) Continuous-speech b) Speaker-independent c) Isolated-word d) Both A and B e) None of the above 78) The personal dictation software is classed as an ___________________________ recognition system a) Speaker-enro ...
... 77) The personal dictation software is classed as _________________ recognition system a) Continuous-speech b) Speaker-independent c) Isolated-word d) Both A and B e) None of the above 78) The personal dictation software is classed as an ___________________________ recognition system a) Speaker-enro ...
15-441: Networking Virtual Circuits, ATM, MPLS Peter Steenkiste Carnegie Mellon University
... Technology did not match people’s experience with IP – deploying ATM in LAN is complex (e.g. broadcast) – supporting connection-less service model on connection-based technology » With IP over ATM, a lot of functionality is replicated ...
... Technology did not match people’s experience with IP – deploying ATM in LAN is complex (e.g. broadcast) – supporting connection-less service model on connection-based technology » With IP over ATM, a lot of functionality is replicated ...
Investigating Network Performance – A Case Study
... bandwidths as well as large collecting area e.g Lovell, GBT, Effelsberg, Camb. 32-m • Aperture synthesis needs signals from individual antennas to be correlated together at a central site • Need for interconnection data rates of many Gbit/sec ...
... bandwidths as well as large collecting area e.g Lovell, GBT, Effelsberg, Camb. 32-m • Aperture synthesis needs signals from individual antennas to be correlated together at a central site • Need for interconnection data rates of many Gbit/sec ...
Detecting Good Neighbor Nodes and Finding
... Typically, routing protocols are classified according to the route discovery philosophy, into either reactive or proactive. Reactive protocols are on-demand. Route-discovery mechanisms are initiated only when a packet is available for transmission, and no route is available. On the other hand, proac ...
... Typically, routing protocols are classified according to the route discovery philosophy, into either reactive or proactive. Reactive protocols are on-demand. Route-discovery mechanisms are initiated only when a packet is available for transmission, and no route is available. On the other hand, proac ...
10Logan
... Flow Label : Request for special handling by routers within a network Payload Length : Length of the remainder of the packet following the IPv6 header Next Header : Type of header following the IPv6 header Hop Limit : Limitation for the impact of routing loops ...
... Flow Label : Request for special handling by routers within a network Payload Length : Length of the remainder of the packet following the IPv6 header Next Header : Type of header following the IPv6 header Hop Limit : Limitation for the impact of routing loops ...
lecture7-socket
... Dealing with blocking calls Many of the functions we saw block until a certain ...
... Dealing with blocking calls Many of the functions we saw block until a certain ...
Socket Programming
... Dealing with blocking calls Many of the functions we saw block until a certain ...
... Dealing with blocking calls Many of the functions we saw block until a certain ...
Document
... If dest IP address not own, router consults routing table to determine next-hop and associated network interface & forwards packet ...
... If dest IP address not own, router consults routing table to determine next-hop and associated network interface & forwards packet ...
Web Application Firewall (WAF)
... specific use cases for the customer Rules can be built that execute when one or more baseline rules or rate control rules match Output of application vulnerability products can be implemented as “virtual patches” Advanced piping to user validation actions can be achieved (prioritization) ...
... specific use cases for the customer Rules can be built that execute when one or more baseline rules or rate control rules match Output of application vulnerability products can be implemented as “virtual patches” Advanced piping to user validation actions can be achieved (prioritization) ...
Chapter9 (ICMP)
... Masking is needed for diskless stations at start-up time. When a diskless station comes up for the first time it may ask for its full IP address using RARP protocol after receiving its IP address, it may use the address mask request and reply to find out which part of the address defines the sub ...
... Masking is needed for diskless stations at start-up time. When a diskless station comes up for the first time it may ask for its full IP address using RARP protocol after receiving its IP address, it may use the address mask request and reply to find out which part of the address defines the sub ...
ppt - Carnegie Mellon School of Computer Science
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
Technical University Berlin Telecommunication Networks Group Optimization of Handover Performance
... the elimination of the time to detect handover. Moreover, link-layer trigger can be employed for other functionality, such as paging as well. An inactive mobile node can be triggered by link-layer information to re-register when it enters a new paging area. The mobile node does not need to monitor t ...
... the elimination of the time to detect handover. Moreover, link-layer trigger can be employed for other functionality, such as paging as well. An inactive mobile node can be triggered by link-layer information to re-register when it enters a new paging area. The mobile node does not need to monitor t ...
DICOM Digital Imaging COmmunications in Medicine
... • Allow a user to determine which optional components of the DICOM Standard are supported by a particular implementation, and what extensions or specializations an implementation adds. • By comparing the Conformance Statements from two implementations, a knowledgeable user should be able to determin ...
... • Allow a user to determine which optional components of the DICOM Standard are supported by a particular implementation, and what extensions or specializations an implementation adds. • By comparing the Conformance Statements from two implementations, a knowledgeable user should be able to determin ...
Chapter 7
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
DICOM Digital Imaging COmmunications in Medicine
... Allow a user to determine which optional components of the DICOM Standard are supported by a particular implementation, and what extensions or specializations an implementation adds. By comparing the Conformance Statements from two implementations, a knowledgeable user should be able to determin ...
... Allow a user to determine which optional components of the DICOM Standard are supported by a particular implementation, and what extensions or specializations an implementation adds. By comparing the Conformance Statements from two implementations, a knowledgeable user should be able to determin ...
Streaming - Regis University: Academic Web Server for Faculty
... • client-side adaptive playout delay: to compensate for delay • server side matches stream bandwidth to available client-to-server path bandwidth ...
... • client-side adaptive playout delay: to compensate for delay • server side matches stream bandwidth to available client-to-server path bandwidth ...
SweetBait: Zero-Hour Worm Detection and Containment Using Honeypots
... meta-information. Such data include the timestamp to indicate the time of generation, the source of the signature (e.g., the IP of the honeypot), and various flags to indicate whether it has been verified by an expert to be a valid or a false signature. The latter is essential information that perm ...
... meta-information. Such data include the timestamp to indicate the time of generation, the source of the signature (e.g., the IP of the honeypot), and various flags to indicate whether it has been verified by an expert to be a valid or a false signature. The latter is essential information that perm ...
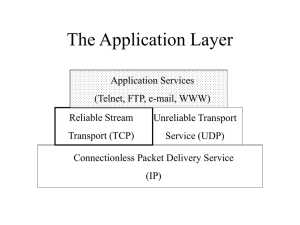
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).