3rd Edition: Chapter 4 - Communications Systems Center
... 1500- 20 = 1480 (max. bytes of data in each fragment) 3. Divide "maximum data bytes" by 8: 1480/8 = 185 to get offset increment 4. Offset of each fragment "n" (n = 0, 1, 2, ...) = n x "offset increment": 0, 185, 370. ... 5. Length of each fragment (except last) = 20 + "max. data bytes" = 20 +1480 = ...
... 1500- 20 = 1480 (max. bytes of data in each fragment) 3. Divide "maximum data bytes" by 8: 1480/8 = 185 to get offset increment 4. Offset of each fragment "n" (n = 0, 1, 2, ...) = n x "offset increment": 0, 185, 370. ... 5. Length of each fragment (except last) = 20 + "max. data bytes" = 20 +1480 = ...
Document
... UDP only provides basic functions:port addr, checksum, length. It does not provide any sequencing or reordering functions, can not specify the damaged packet Ya Bao ...
... UDP only provides basic functions:port addr, checksum, length. It does not provide any sequencing or reordering functions, can not specify the damaged packet Ya Bao ...
Sockets
... • Int(int socket, int backlog) • Socket: handle of newly creates socket • Backlog: number of connection requests that can be queued by the system while waiting for server to execute accept call. ...
... • Int(int socket, int backlog) • Socket: handle of newly creates socket • Backlog: number of connection requests that can be queued by the system while waiting for server to execute accept call. ...
MDM1200E33D
... 1. The information given herein, including the specifications and dimensions, is subject to change without prior notice to improve product characteristics. Before ordering, purchasers are advised to contact Hitachi sales department for the latest version of this data sheets. 2. Please be sure to rea ...
... 1. The information given herein, including the specifications and dimensions, is subject to change without prior notice to improve product characteristics. Before ordering, purchasers are advised to contact Hitachi sales department for the latest version of this data sheets. 2. Please be sure to rea ...
Reliable Multicast Protocols for MANET
... • Source selects a node from the receiver list as a feedback receiver in a roundrobin fashion and notifies it together with the data packets • The feedback receiver is responsible for replying ACK or NACK to the source until it collects all data packets ...
... • Source selects a node from the receiver list as a feedback receiver in a roundrobin fashion and notifies it together with the data packets • The feedback receiver is responsible for replying ACK or NACK to the source until it collects all data packets ...
Reliable Multicast Protocols for MANET
... • Source selects a node from the receiver list as a feedback receiver in a roundrobin fashion and notifies it together with the data packets • The feedback receiver is responsible for replying ACK or NACK to the source until it collects all data packets ...
... • Source selects a node from the receiver list as a feedback receiver in a roundrobin fashion and notifies it together with the data packets • The feedback receiver is responsible for replying ACK or NACK to the source until it collects all data packets ...
Reliable Multicast Protocols for MANET
... • Source selects a node from the receiver list as a feedback receiver in a roundrobin fashion and notifies it together with the data packets • The feedback receiver is responsible for replying ACK or NACK to the source until it collects all data packets ...
... • Source selects a node from the receiver list as a feedback receiver in a roundrobin fashion and notifies it together with the data packets • The feedback receiver is responsible for replying ACK or NACK to the source until it collects all data packets ...
3rd Edition: Chapter 4 - Communications Systems Center (CSC)
... number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to ...
... number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to ...
Link Layer
... encapsulate datagram into frame, adding header, trailer ‘physical addresses’ used in frame headers to identify source, destination • different from IP address! Link access Media access control (MAC) protocol Coordinate the frame transmissions of many nodes if multiple nodes share a medium ...
... encapsulate datagram into frame, adding header, trailer ‘physical addresses’ used in frame headers to identify source, destination • different from IP address! Link access Media access control (MAC) protocol Coordinate the frame transmissions of many nodes if multiple nodes share a medium ...
Introduction to computer networkd #8
... TCP allows the regulation of the flow of segments, ensuring that one host doesn’t flood another host with too many segments, overflowing its receiving buffer. TCP uses a sliding windowing mechanism to assist with flow control. For example, if the window size is 1, a host can send only one segment an ...
... TCP allows the regulation of the flow of segments, ensuring that one host doesn’t flood another host with too many segments, overflowing its receiving buffer. TCP uses a sliding windowing mechanism to assist with flow control. For example, if the window size is 1, a host can send only one segment an ...
Data Sheet PT8A2512NE Simple Toaster Controller Features
... Power Dissipation……………………………………………………… 500mW ...
... Power Dissipation……………………………………………………… 500mW ...
- Lancaster University
... packets observed during this time section is 462 which is less than 0.46% of the total number of packets (101620). Further, the size of TCP packets is generally small. On the other hand, UDP datagrams clearly seem to be one of two types. One type is datagrams that are bigger than 600 bytes, most bei ...
... packets observed during this time section is 462 which is less than 0.46% of the total number of packets (101620). Further, the size of TCP packets is generally small. On the other hand, UDP datagrams clearly seem to be one of two types. One type is datagrams that are bigger than 600 bytes, most bei ...
Note
... (2) Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LANs today are also linked to a wide area network (WAN) or the Internet. (3) The LAN market has seen several technologies such as Ethernet, token ring, token ...
... (2) Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LANs today are also linked to a wide area network (WAN) or the Internet. (3) The LAN market has seen several technologies such as Ethernet, token ring, token ...
packet switching - SpaceAgeTimes.com
... it is needed, and share the available capacity between many users. With a circuit-switched connection, the data bits put on the circuit are automatically delivered to the far end because the circuit is already established. If the circuit is to be shared, there must be some mechanism to label the bit ...
... it is needed, and share the available capacity between many users. With a circuit-switched connection, the data bits put on the circuit are automatically delivered to the far end because the circuit is already established. If the circuit is to be shared, there must be some mechanism to label the bit ...
Space Internetworking Architecture 20080716
... In the terrestrial Internet, data reliability is provided by the end systems, primarily using the TCP protocol. If data is lost or corrupted in the network, TCP will detect this and retransmit the data. To ‘hold the gains that have been achieved’, DTN supports a custody transfer mechanism for data r ...
... In the terrestrial Internet, data reliability is provided by the end systems, primarily using the TCP protocol. If data is lost or corrupted in the network, TCP will detect this and retransmit the data. To ‘hold the gains that have been achieved’, DTN supports a custody transfer mechanism for data r ...
PPT
... • Flows versus routes. • tags explicitly cover groups of routes • tag bindings set up as part of route establishment • flows in IP switching are driven by traffic and detected by “filters” • Supports both fine grain application flows and coarser grain flow groups ...
... • Flows versus routes. • tags explicitly cover groups of routes • tag bindings set up as part of route establishment • flows in IP switching are driven by traffic and detected by “filters” • Supports both fine grain application flows and coarser grain flow groups ...
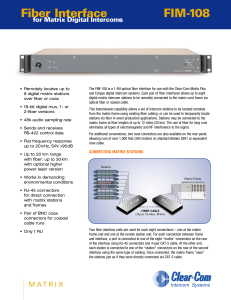
Clear-Com FIM-108 Datasheet - AV-iQ
... signal flow. When cable availability is limited, the optional FIM-108S uses wave-dimension multiplexing on a single fiber for bidirectional transmission. ...
... signal flow. When cable availability is limited, the optional FIM-108S uses wave-dimension multiplexing on a single fiber for bidirectional transmission. ...
Chapter5-LANs - ECE Users Pages
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” (Media Access Control) addresses used in frame headers to identify source, dest • different from IP address! ...
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” (Media Access Control) addresses used in frame headers to identify source, dest • different from IP address! ...
A Modular Network Layer for Sensornets
... addressing, to maximize module replaceability. Other functions of an FE include local delivery when the RE determines that the local node is the destination, hooks for interception of packets for purposes of innetwork aggregation, network level retransmission, and multicast. Finally, the FE may opt ...
... addressing, to maximize module replaceability. Other functions of an FE include local delivery when the RE determines that the local node is the destination, hooks for interception of packets for purposes of innetwork aggregation, network level retransmission, and multicast. Finally, the FE may opt ...
Voice-TFCC
... – Network bandwidth limitation in bytes/sec rather than in packets/sec for VoIP traffic • Design goal: – Achieve the same bandwidth in bytes/sec as a TCP flow using 1500 – byte data packets • Penalize VoIP applications that send small payload packets which increasing header overhead – Reduce the sen ...
... – Network bandwidth limitation in bytes/sec rather than in packets/sec for VoIP traffic • Design goal: – Achieve the same bandwidth in bytes/sec as a TCP flow using 1500 – byte data packets • Penalize VoIP applications that send small payload packets which increasing header overhead – Reduce the sen ...
RC Terminator Networks 700 Series
... about 1.77 ns per foot. Applying the above relationship, a transmission line will require termination if it is longer than 7 inches. High performance systems will commonly need Bourns termination networks for CPU address, data, and control lines. In addition, clock inputs, write and read strobe line ...
... about 1.77 ns per foot. Applying the above relationship, a transmission line will require termination if it is longer than 7 inches. High performance systems will commonly need Bourns termination networks for CPU address, data, and control lines. In addition, clock inputs, write and read strobe line ...
Broadband Access technologies
... of 256 carriers, create a statistical distribution of composite signal amplitude over the transmission line. Thus, there will be times when the phases of multiple tones will align in a manner that causes the peak amplitudes of the individual tones to add to each other so that the composite waveform ...
... of 256 carriers, create a statistical distribution of composite signal amplitude over the transmission line. Thus, there will be times when the phases of multiple tones will align in a manner that causes the peak amplitudes of the individual tones to add to each other so that the composite waveform ...