Red Team Instrumentation
... “Designed to protect software applications from reverse engineering, tamper, theft, and unauthorized execution” • Features – Application source code is NOT needed, protects standard executables, shared libraries, and full systems – Operates at the kernel-level; preventing attacks from even privilege ...
... “Designed to protect software applications from reverse engineering, tamper, theft, and unauthorized execution” • Features – Application source code is NOT needed, protects standard executables, shared libraries, and full systems – Operates at the kernel-level; preventing attacks from even privilege ...
Chapter 19: Security
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
Information Assurance (IA) Framework
... domains, where access security levels identify domains. There are three security levels: TOP SECRET, SECRET, and UNCLASSIFIED. While there can be, and usually are, many caveats in each of these domains, and some additional levels of Discretionary Access Control (DAC) are required, for example betwee ...
... domains, where access security levels identify domains. There are three security levels: TOP SECRET, SECRET, and UNCLASSIFIED. While there can be, and usually are, many caveats in each of these domains, and some additional levels of Discretionary Access Control (DAC) are required, for example betwee ...
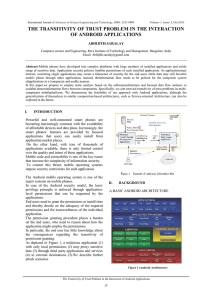
the transitivity of trust problem in the interaction of android
... Abstract-Mobile phones have developed into complex platforms with large numbers of installed applications and awide range of sensitive data. Application security policies limitthe permissions of each installed application. As applicationsmay interact, restricting single applications may create a fal ...
... Abstract-Mobile phones have developed into complex platforms with large numbers of installed applications and awide range of sensitive data. Application security policies limitthe permissions of each installed application. As applicationsmay interact, restricting single applications may create a fal ...