Replication - Home - Australian SQL Server User Group
... Security context issues with accessing snapshot and updates FTP or accessing a share – security issue in both ...
... Security context issues with accessing snapshot and updates FTP or accessing a share – security issue in both ...
Chapter 3 Effects of IT on Strategy and Competition
... • Some users might be able to retrieve and update data in the database. Other users might be able to retrieve any data from the database but not make any changes to it. Still other users might be able to access only a portion of the database. ...
... • Some users might be able to retrieve and update data in the database. Other users might be able to retrieve any data from the database but not make any changes to it. Still other users might be able to access only a portion of the database. ...
Fundamentals of Database Systems
... I SQL is the industry standard for defining and querying data I SQL is founded on the relational model of data I SQL allows us to specify relational database schemata I SQL allows us to specify integrity constraints to restrict the data to those considered meaningful to the application at hand ,→ dom ...
... I SQL is the industry standard for defining and querying data I SQL is founded on the relational model of data I SQL allows us to specify relational database schemata I SQL allows us to specify integrity constraints to restrict the data to those considered meaningful to the application at hand ,→ dom ...
JDBC/Oracle tutorial
... What causes the "No suitable driver" error? "No suitable driver" is an error that usually occurs during a call to the DriverManager.getConnection method. The cause can be failing to load the appropriate JDBC drivers before calling the getConnection method, or it can be specifying an invalid JDBC URL ...
... What causes the "No suitable driver" error? "No suitable driver" is an error that usually occurs during a call to the DriverManager.getConnection method. The cause can be failing to load the appropriate JDBC drivers before calling the getConnection method, or it can be specifying an invalid JDBC URL ...
Simple version control
... All newly added not-null columns should have default to prevent errors when adding to table with data. If no default value is possible – add column as nullable, fill it with appropriate data and then alter to not null. ...
... All newly added not-null columns should have default to prevent errors when adding to table with data. If no default value is possible – add column as nullable, fill it with appropriate data and then alter to not null. ...
Database Procedural Programming PL/SQL and Embedded SQL
... An entire package is loaded into memory when a procedure within the package is called for the first time in one operation, as opposed to the separate loads required for standalone procedures. When calls to related packaged procedures occur, no disk I/O is necessary to execute the compiled code alr ...
... An entire package is loaded into memory when a procedure within the package is called for the first time in one operation, as opposed to the separate loads required for standalone procedures. When calls to related packaged procedures occur, no disk I/O is necessary to execute the compiled code alr ...
Advanced SQL
... the SQL create table statement: The primary key clause lists attributes that comprise the primary key. The unique key clause lists attributes that comprise a candidate key. The foreign key clause lists the attributes that comprise the foreign key and the name of the relation referenced by the ...
... the SQL create table statement: The primary key clause lists attributes that comprise the primary key. The unique key clause lists attributes that comprise a candidate key. The foreign key clause lists the attributes that comprise the foreign key and the name of the relation referenced by the ...
Access Utilities - D. H. D`Urso and Associates
... Student “hands-on” - by the end of the class the student will have worked through all the Access Utilities and secured a database Exercises are cumulative – later examples build on objects created earlier ...
... Student “hands-on” - by the end of the class the student will have worked through all the Access Utilities and secured a database Exercises are cumulative – later examples build on objects created earlier ...
SQL Server Security for the Access Developer
... go through views, user-defined functions, or stored procedures that you create for data access. For example, if you deny all permissions on the Customers table, and you grant EXECUTE permissions on a set of stored procedures that reference the Customers table, a user will be forced to work with cust ...
... go through views, user-defined functions, or stored procedures that you create for data access. For example, if you deny all permissions on the Customers table, and you grant EXECUTE permissions on a set of stored procedures that reference the Customers table, a user will be forced to work with cust ...
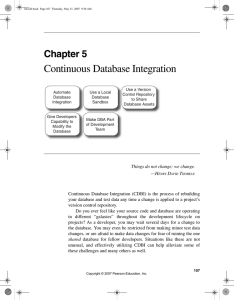
Continuous Database Integration
... It’s more of the same on a typical day for the DBA. Not only is this a poor use of the DBA’s talents, it causes a significant bottleneck, especially in the continuous approach promoted by CI. If you asked any DBA what they’d rather do on a day-to-day basis, they would probably tell you that they’d r ...
... It’s more of the same on a typical day for the DBA. Not only is this a poor use of the DBA’s talents, it causes a significant bottleneck, especially in the continuous approach promoted by CI. If you asked any DBA what they’d rather do on a day-to-day basis, they would probably tell you that they’d r ...
transaction - Pearson Education
... Two-phased Locking • Two-phased locking Transactions are allowed to obtain locks as necessary (growing phase). Once the first lock is released (shrinking phase), no other lock can be obtained. • A special case of two-phased locking. Locks are obtained throughout the transaction. No lock is ...
... Two-phased Locking • Two-phased locking Transactions are allowed to obtain locks as necessary (growing phase). Once the first lock is released (shrinking phase), no other lock can be obtained. • A special case of two-phased locking. Locks are obtained throughout the transaction. No lock is ...
Structured Query Language
... 8. Add a new order item for the last order you created (DML command 7). The product purchased is a SanDisk Cruzer 128MB. The quantity purchased is 3. Primary Key Value Assigned to New Record = ___________ 9. Add a new order item for the last order you created (DML command 7). The product purchased i ...
... 8. Add a new order item for the last order you created (DML command 7). The product purchased is a SanDisk Cruzer 128MB. The quantity purchased is 3. Primary Key Value Assigned to New Record = ___________ 9. Add a new order item for the last order you created (DML command 7). The product purchased i ...
Representing Weak Entity Sets
... columns for the primary keys of the two participating entity sets, and any descriptive attributes of the relationship set. E.g.: table for relationship set borrower ...
... columns for the primary keys of the two participating entity sets, and any descriptive attributes of the relationship set. E.g.: table for relationship set borrower ...
Information System Design Laboratory Laboratory Manual Third Year - Information Technology
... How an event driven application works. Event is an action recognized by a form or control. Event-driven applications execute Basic code in response to an event. Each form & control in VB has a predefined set of events. If one of these events occurs & there is code in the associated event procedure, ...
... How an event driven application works. Event is an action recognized by a form or control. Event-driven applications execute Basic code in response to an event. Each form & control in VB has a predefined set of events. If one of these events occurs & there is code in the associated event procedure, ...
Mapping between Alloy specifications and database implementations
... A signature declaration may also comprise a set of fields, that model relationships between signatures. For example, name associates objects with their names. In this field declaration, one is a multiplicity constraint stating that each object has exactly one name. The remaining fields state that a ...
... A signature declaration may also comprise a set of fields, that model relationships between signatures. For example, name associates objects with their names. In this field declaration, one is a multiplicity constraint stating that each object has exactly one name. The remaining fields state that a ...
Query-aware Test Generation Using a Relational Constraint Solver
... executing these queries might not return meaningful results. Recent approaches introduced query-aware database generation [2], [3]. These approaches use the information from the queries to constrain the data generator to generate databases that provide interesting results upon query executions. Quer ...
... executing these queries might not return meaningful results. Recent approaches introduced query-aware database generation [2], [3]. These approaches use the information from the queries to constrain the data generator to generate databases that provide interesting results upon query executions. Quer ...
6. Compatibility Assessment for Migration to DB2 pureScale
... 7.3.2. Run the custom extraction script on your source DB2 database You can execute the custom extraction script by using the DB2 Command Line Processor from a machine that has access to the source DB2 database server. Manually running the script is outside of the scope of this guide. 7.3.3. Import ...
... 7.3.2. Run the custom extraction script on your source DB2 database You can execute the custom extraction script by using the DB2 Command Line Processor from a machine that has access to the source DB2 database server. Manually running the script is outside of the scope of this guide. 7.3.3. Import ...
Spatial Query Languages
... The Country entity has six attributes. The Name of the country and the continent (Cont) it belongs to are character strings of maximum length thirty-five. The population (Pop) and the gross domestic product (GDP) are integer types. The GDP is the total value of goods and services produced in a count ...
... The Country entity has six attributes. The Name of the country and the continent (Cont) it belongs to are character strings of maximum length thirty-five. The population (Pop) and the gross domestic product (GDP) are integer types. The GDP is the total value of goods and services produced in a count ...
Essential Database Maintenance Essential Database Maintenance
... Rough estimate of current tables – be sure to calculate: ...
... Rough estimate of current tables – be sure to calculate: ...
Relation
... Research in 1970 in paper titled “Relational Model of Data for Large Shared Data Banks” one of great papers in computer science The Relational Model of Data is Based on the Concept of Relations A Relation is a Mathematical Concept Based on the Concept of Sets The strength of the relational approac ...
... Research in 1970 in paper titled “Relational Model of Data for Large Shared Data Banks” one of great papers in computer science The Relational Model of Data is Based on the Concept of Relations A Relation is a Mathematical Concept Based on the Concept of Sets The strength of the relational approac ...
INFO2120/2820 Database Systems I: Transactions
... Techniques” (Gray/Reuter, 1993) first Ph.D. from CS at UC Berkeley (1969) worked for IBM (at System R) Tandem-Computers, DEC, …, Microsoft Research ...
... Techniques” (Gray/Reuter, 1993) first Ph.D. from CS at UC Berkeley (1969) worked for IBM (at System R) Tandem-Computers, DEC, …, Microsoft Research ...
Development of a SAS/DB2 Business Application
... out the details. Working with tables is fully transparent. If the SASI ACCESS interface to DB2 was fully transparent, the application should still be working after moving it to DB2. This was not the case however. During the development of the application we had already investigated the problems and ...
... out the details. Working with tables is fully transparent. If the SASI ACCESS interface to DB2 was fully transparent, the application should still be working after moving it to DB2. This was not the case however. During the development of the application we had already investigated the problems and ...