Chapter 7: Relational Database Design
... view equivalent if the following three conditions are met: 1. For each data item Q, if transaction Ti reads the initial value of Q in schedule S, then transaction Ti must, in schedule S´, also read the initial value of Q. 2. For each data item Q, if transaction Ti executes read(Q) in schedule S, and ...
... view equivalent if the following three conditions are met: 1. For each data item Q, if transaction Ti reads the initial value of Q in schedule S, then transaction Ti must, in schedule S´, also read the initial value of Q. 2. For each data item Q, if transaction Ti executes read(Q) in schedule S, and ...
dmsunit5ppt - SNGCE DIGITAL LIBRARY
... main memory from disk,and then its value is copied into a program variable • To write a database object an in-memory copy of the object is first modified and then written to disk. (Data base objects are the units in which programs read or write information) ...
... main memory from disk,and then its value is copied into a program variable • To write a database object an in-memory copy of the object is first modified and then written to disk. (Data base objects are the units in which programs read or write information) ...
Fundamentals of Database Development (with Delphi)
... immediately. Single−tiered databases are limited in how much data the tables can hold and the number of users your application can support. When the database information includes complicated relationships between several tables, or when the number of clients grows, you may want to use a two−tiered o ...
... immediately. Single−tiered databases are limited in how much data the tables can hold and the number of users your application can support. When the database information includes complicated relationships between several tables, or when the number of clients grows, you may want to use a two−tiered o ...
l DBMS-II Lab Manual
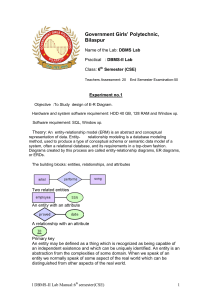
... method, used to produce a type of conceptual schema or semantic data model of a system, often a relational database, and its requirements in a top-down fashion. Diagrams created by this process are called entity-relationship diagrams, ER diagrams, or ERDs. The building blocks: entities, relationship ...
... method, used to produce a type of conceptual schema or semantic data model of a system, often a relational database, and its requirements in a top-down fashion. Diagrams created by this process are called entity-relationship diagrams, ER diagrams, or ERDs. The building blocks: entities, relationship ...
The Kexi Handbook - KDE Documentation
... Kexi is a database management application. It can be used for creating databases, inserting data, performing queries, and processing data. Forms can be created to provide a custom interface to your data. All database objects - tables, queries and forms - are stored in the database, making it easy to ...
... Kexi is a database management application. It can be used for creating databases, inserting data, performing queries, and processing data. Forms can be created to provide a custom interface to your data. All database objects - tables, queries and forms - are stored in the database, making it easy to ...
Database Theory - Binus Repository
... – Provide natural and easy-to-understand structuring of information – Support processing requirements and any performance objectives ...
... – Provide natural and easy-to-understand structuring of information – Support processing requirements and any performance objectives ...
1. What are the components of physical database structure of Oracle
... consistant with respect to the same point in time. 63. What is a deadlock ? Explain . Two processes wating to update the rows of a table which are locked by the other process then deadlock arises. In a database environment this will often happen because of not issuing proper row lock commands. Poor ...
... consistant with respect to the same point in time. 63. What is a deadlock ? Explain . Two processes wating to update the rows of a table which are locked by the other process then deadlock arises. In a database environment this will often happen because of not issuing proper row lock commands. Poor ...
DBMS Lab
... 3 VLM instance tuning-This improves database performance by caching more database buffers in memory. This reduces disk I/O. 4 User migration utility-Simplifies conversion of local and external database users to enterprise users. 5 Oracle shares server process-It is a server configuration which allow ...
... 3 VLM instance tuning-This improves database performance by caching more database buffers in memory. This reduces disk I/O. 4 User migration utility-Simplifies conversion of local and external database users to enterprise users. 5 Oracle shares server process-It is a server configuration which allow ...
Installation
... supported types of installation. In the end, there are several Section chapters. References are made to these Sections from the chapters which describe the supported types of installation. Please read the general chapters and the relevant part of this installation guide for your type of installation ...
... supported types of installation. In the end, there are several Section chapters. References are made to these Sections from the chapters which describe the supported types of installation. Please read the general chapters and the relevant part of this installation guide for your type of installation ...
Plug-ins MOUNT10 V7 Sailfish R2 User Manual
... MS SQL Server Instance: Last status provides information about the last connection to the SQL Server. Enter the Server address, port, SQL username and password that the SE Backup Client must use to connect to the SQL Server. Note: You need to manually enable TCP/IP ports in the SQL 2005 Management t ...
... MS SQL Server Instance: Last status provides information about the last connection to the SQL Server. Enter the Server address, port, SQL username and password that the SE Backup Client must use to connect to the SQL Server. Note: You need to manually enable TCP/IP ports in the SQL 2005 Management t ...
Access 2010 Test Questions 1. Which software program is used to
... 55. Which Access 2010 function key is a shortcut to Microsoft Office Access Help? A. B. C. D. ...
... 55. Which Access 2010 function key is a shortcut to Microsoft Office Access Help? A. B. C. D. ...
www.ipeirotis.com
... Above 80% for most threshold combinations tried
Degrades gracefully with hierarchy depth
...
... Above 80% for most
Backup_and_Recovery
... copy of a database object early Monday morning at 2:00 A.M. and then took an incremental image copy at the same time the following three mornings. The full image copy plus all three incremental image copies need to be applied to recover the tablespace. If the same column of the same row was updated ...
... copy of a database object early Monday morning at 2:00 A.M. and then took an incremental image copy at the same time the following three mornings. The full image copy plus all three incremental image copies need to be applied to recover the tablespace. If the same column of the same row was updated ...
Valid Time Database Implementation Using Oracle11g Workspace
... facts which are currently true and satisfy the search conditions. In principle, current queries (and other current operations) on temporal database system should be compatible with conventional databases. Current queries are therefore almost identical to normal SQL queries except the references to v ...
... facts which are currently true and satisfy the search conditions. In principle, current queries (and other current operations) on temporal database system should be compatible with conventional databases. Current queries are therefore almost identical to normal SQL queries except the references to v ...
Zvi`s changes, if any, are marked in green, they are not copyrighted
... are used. • E.g. Strings would normally be considered indivisible • Suppose that students are given course numbers which are strings of the form CS0012 or EE1127 • If the first two characters are extracted to find the department, the domain of course numbers is not atomic. • Doing so is a bad idea: ...
... are used. • E.g. Strings would normally be considered indivisible • Suppose that students are given course numbers which are strings of the form CS0012 or EE1127 • If the first two characters are extracted to find the department, the domain of course numbers is not atomic. • Doing so is a bad idea: ...
Oracle12c New Features including Release 2 New Features
... This presentation and/or courseware make reference to Oracle Corp and Quest Software product features that you may or may not be licensed to use at your site (products such as TOAD itself, Advanced Workload Repository, SQL Tuning Advisor, etc). Please consult your contracts and purchase agreements b ...
... This presentation and/or courseware make reference to Oracle Corp and Quest Software product features that you may or may not be licensed to use at your site (products such as TOAD itself, Advanced Workload Repository, SQL Tuning Advisor, etc). Please consult your contracts and purchase agreements b ...
Oracle, SAP and MS SQL on Vblock System 540
... used. The reason we chose to implement the test this way was to have an environment that produced a mixture of compute, network, and storage demands from different application vendors (SAP, Oracle, and Microsoft) and from different application uses (OLTP and OLAP). Knowing that working with mixed wo ...
... used. The reason we chose to implement the test this way was to have an environment that produced a mixture of compute, network, and storage demands from different application vendors (SAP, Oracle, and Microsoft) and from different application uses (OLTP and OLAP). Knowing that working with mixed wo ...
Oracle and Sybase, Concepts and Contrasts
... optimizer is the component of an RDBMS that determines the best way to execute each query. For example for a Server created with 8K page size, one can have 8K, 16K, 32K and 64K buffer pools. Two cache replacement strategies are used by ASE. These are called Least Recently Used (LRU) replacement str ...
... optimizer is the component of an RDBMS that determines the best way to execute each query. For example for a Server created with 8K page size, one can have 8K, 16K, 32K and 64K buffer pools. Two cache replacement strategies are used by ASE. These are called Least Recently Used (LRU) replacement str ...
Document
... As a running example, we exhibit in Figure 1 a snowflake schema for a data warehouse for keeping track of students’ attendance in a college. The fact table of this schema is ATTENDANCE, and its dimension tables are DATE, ROOM, LECTURER, STUDENT and COURSE; HOLIDAY is a subdimension of DATE, and DEPA ...
... As a running example, we exhibit in Figure 1 a snowflake schema for a data warehouse for keeping track of students’ attendance in a college. The fact table of this schema is ATTENDANCE, and its dimension tables are DATE, ROOM, LECTURER, STUDENT and COURSE; HOLIDAY is a subdimension of DATE, and DEPA ...
Using ADO from Delphi
... and delete some records but not physically. ........................................................... 102 How do I retrieve a system information, for example, list of tables, fields (columns), indexes from the database? .............................................................................. ...
... and delete some records but not physically. ........................................................... 102 How do I retrieve a system information, for example, list of tables, fields (columns), indexes from the database? .............................................................................. ...
A Comparative Study on the Performance of the Top
... storing, retrieving, and querying digital data. For instance, dynamic websites, accounting information systems, payroll systems, stock management systems all rely on internal databases as a container to store and manage their data [1]. Many software development firms are today developing and produci ...
... storing, retrieving, and querying digital data. For instance, dynamic websites, accounting information systems, payroll systems, stock management systems all rely on internal databases as a container to store and manage their data [1]. Many software development firms are today developing and produci ...
Database-as-a-Service (DBaaS) Reference Architecture with
... • On-‐demand, self-‐service database provisioning. End-‐users can create or tear down database services based on their needs. • Provides for outsourcing the administration and monitoring of databases an ...
... • On-‐demand, self-‐service database provisioning. End-‐users can create or tear down database services based on their needs. • Provides for outsourcing the administration and monitoring of databases an ...
Transactional Consistency and Automatic Management
... the effects of other transactions that committed prior to that timestamp. For read/write transactions, TxCache supports this guarantee by running them directly on the database, bypassing the cache entirely. Read-only transactions use objects in the cache, and TxCache ensures that nevertheless they v ...
... the effects of other transactions that committed prior to that timestamp. For read/write transactions, TxCache supports this guarantee by running them directly on the database, bypassing the cache entirely. Read-only transactions use objects in the cache, and TxCache ensures that nevertheless they v ...