SQL standard published_POST
... JSON Objects consist of tags and data. For some applications, they provide a great deal of flexibility. SQL:2016 provides support to: ...
... JSON Objects consist of tags and data. For some applications, they provide a great deal of flexibility. SQL:2016 provides support to: ...
Slides from Lecture 15 - Courses - University of California, Berkeley
... • Transactions are started with SET TRANSACTION, followed by the SQL statements • Any changes made by the SQL are made permanent by COMMIT • Part or all of a transaction can be undone using ROLLBACK IS 257 – Spring 2005 ...
... • Transactions are started with SET TRANSACTION, followed by the SQL statements • Any changes made by the SQL are made permanent by COMMIT • Part or all of a transaction can be undone using ROLLBACK IS 257 – Spring 2005 ...
Course Review
... an object (say a building) uniquely identifies a building and also nominates where it is. Super Key : This is normally a key with too many attributes in it. Some of the columns could be removed and a key would still exist. A good example is a key which contains ‘old value/new value’ such as ‘old tel ...
... an object (say a building) uniquely identifies a building and also nominates where it is. Super Key : This is normally a key with too many attributes in it. Some of the columns could be removed and a key would still exist. A good example is a key which contains ‘old value/new value’ such as ‘old tel ...
Powerpoint - SQL Saturday
... Split up HW NUMA nodes when we detect > 8 physical processors per NUMA node On by default in 2016 (Change with ALTER SERVER CONFIGURATION) Code in engine that benefits from NUMA partitioning gets a boost ...
... Split up HW NUMA nodes when we detect > 8 physical processors per NUMA node On by default in 2016 (Change with ALTER SERVER CONFIGURATION) Code in engine that benefits from NUMA partitioning gets a boost ...
Physical Database Design
... Organizational context for using database systems Organizations have created the position of database administrator (DBA) and database administration departments Information technology (IT) and information resource management (IRM) departments ...
... Organizational context for using database systems Organizations have created the position of database administrator (DBA) and database administration departments Information technology (IT) and information resource management (IRM) departments ...
CSc-340 04a
... Conditional statements (if-then-else) SQL:1999 also supports a case statement similar to C case statement Example procedure: registers student after ensuring classroom capacity is ...
... Conditional statements (if-then-else) SQL:1999 also supports a case statement similar to C case statement Example procedure: registers student after ensuring classroom capacity is ...
SQL Server Security Securing and Auditing DATABASE ACCESS
... SERVERADMIN – Manage server configurations and start/stop services. PROCESSADMIN – Kill processes running on the instance. SETUPADMIN – Add/remove linked servers. BULKADMIN – Able to run BULK INSERT and execute bulk operations. DISKADMIN – Manage server disk files. DBCREATOR – Create, alter, drop, a ...
... SERVERADMIN – Manage server configurations and start/stop services. PROCESSADMIN – Kill processes running on the instance. SETUPADMIN – Add/remove linked servers. BULKADMIN – Able to run BULK INSERT and execute bulk operations. DISKADMIN – Manage server disk files. DBCREATOR – Create, alter, drop, a ...
Introduction to Database Management Systems for Clinical Research
... fictional cohort study to determine whether neonatal jaundice affects neuropsychological scores at five years of age. We assume that the reader has some experience with collecting and storing clinical research data using spreadsheet or statistical analysis software. Therefore, the reader should be f ...
... fictional cohort study to determine whether neonatal jaundice affects neuropsychological scores at five years of age. We assume that the reader has some experience with collecting and storing clinical research data using spreadsheet or statistical analysis software. Therefore, the reader should be f ...
Transact-SQL Reference (Database Engine) | Microsoft Docs
... To create a table, you must provide a name for the table, and the names and data types of each column in the table. It is also a good practice to indicate whether null values are allowed in each column. To create a table, you must have the CREATE TABLE permission, and the ALTER SCHEMA permission on ...
... To create a table, you must provide a name for the table, and the names and data types of each column in the table. It is also a good practice to indicate whether null values are allowed in each column. To create a table, you must have the CREATE TABLE permission, and the ALTER SCHEMA permission on ...
- Courses - University of California, Berkeley
... • Generally, end-users of database data probably do not want to learn SQL in order to access the information in the database • Instead, they would prefer to use a familiar PC or Web interface that uses the graphical conventions and behaviors that they are familiar with • Today we will look at PC –st ...
... • Generally, end-users of database data probably do not want to learn SQL in order to access the information in the database • Instead, they would prefer to use a familiar PC or Web interface that uses the graphical conventions and behaviors that they are familiar with • Today we will look at PC –st ...
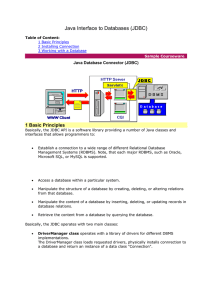
Java Interface to Databases (JDBC)
... The protocol part starts always with "jdbc:" folowed by the name of the RDBMS (in our case "mysql") and terminated with "://" symbols. Thus, the protocol part in our example is "jdbc:mysql://". The host part identifies a server where the DBMS is running. In our case (Servlets & DBMS on the same comp ...
... The protocol part starts always with "jdbc:" folowed by the name of the RDBMS (in our case "mysql") and terminated with "://" symbols. Thus, the protocol part in our example is "jdbc:mysql://". The host part identifies a server where the DBMS is running. In our case (Servlets & DBMS on the same comp ...
Chapter 5 - Integrity And Security
... The permissions or rights that allow user to use some of or all of resources on the server are called Privileges Granting of Privileges - Objects that are created by a user are owned and controlled by that user. If a user want to access any of the objects belonging to another user, the owner of th ...
... The permissions or rights that allow user to use some of or all of resources on the server are called Privileges Granting of Privileges - Objects that are created by a user are owned and controlled by that user. If a user want to access any of the objects belonging to another user, the owner of th ...
Oracle backup and recovery strategy - hep-proj
... and all associated data to the dump file Import then re-creates these items from the dump file The definition statements for derived types are exported, same applies to OIDs ...
... and all associated data to the dump file Import then re-creates these items from the dump file The definition statements for derived types are exported, same applies to OIDs ...
Objects Naming Standards
... The following guidelines have to be enforced while naming a Userdefined Data Type– 1. The first part of the UDT name should be Udt_ 2. The second part of the UDT name should have the general prefix that is being used for the module or process to which the UDT belongs. For example, a UDT that belongs ...
... The following guidelines have to be enforced while naming a Userdefined Data Type– 1. The first part of the UDT name should be Udt_ 2. The second part of the UDT name should have the general prefix that is being used for the module or process to which the UDT belongs. For example, a UDT that belongs ...
Lecture 2
... programming interface) which is used by all SQL Server components. It includes services responsible for memory management, scheduling, deadlock detection, exception handling, etc. ...
... programming interface) which is used by all SQL Server components. It includes services responsible for memory management, scheduling, deadlock detection, exception handling, etc. ...
Build a database III: Build relationships for a new Access database
... record in that second table can also relate to many in the first. For example, say your company has several types of computers and several technicians, with each technician certified to work on some, but not all, of the computers. Each technician can be related to more than one computer, and in turn ...
... record in that second table can also relate to many in the first. For example, say your company has several types of computers and several technicians, with each technician certified to work on some, but not all, of the computers. Each technician can be related to more than one computer, and in turn ...
literature survey - Computer Science
... cluster interconnect), that work collaboratively as a single system. Clusters allow applications to scale beyond the limits imposed by single node systems when processing loads exceed the capacity of large individual servers. However only Oracle 9i provides real support for clustered configurations, ...
... cluster interconnect), that work collaboratively as a single system. Clusters allow applications to scale beyond the limits imposed by single node systems when processing loads exceed the capacity of large individual servers. However only Oracle 9i provides real support for clustered configurations, ...
18: Database System Architectures
... optimization, concurrency control and recovery. Front-end: consists of tools such as forms, report-writers, and graphical user interface facilities. The interface between the front-end and the back-end is through ...
... optimization, concurrency control and recovery. Front-end: consists of tools such as forms, report-writers, and graphical user interface facilities. The interface between the front-end and the back-end is through ...
Sharing and Reproducing Database Applications
... (time periods and spatial extents) which she used to obtain the data from Opendata.gov. However, this service is open to the public and, thus, its database has been modified in the mean time. Hence, Alice’s queries will not return the same result when run by Bob (assuming the service does not provid ...
... (time periods and spatial extents) which she used to obtain the data from Opendata.gov. However, this service is open to the public and, thus, its database has been modified in the mean time. Hence, Alice’s queries will not return the same result when run by Bob (assuming the service does not provid ...
Data Warehousing with MySQL
... Partitioning and Storage Engine Restrictions on MERGE tables • You can use only identical MyISAM tables for a MERGE table. • MERGE tables use more file descriptors. If 10 clients are using a MERGE table that maps to 10 tables, the server uses (10*10) + 10 file descriptors. • Key reads are slower. W ...
... Partitioning and Storage Engine Restrictions on MERGE tables • You can use only identical MyISAM tables for a MERGE table. • MERGE tables use more file descriptors. If 10 clients are using a MERGE table that maps to 10 tables, the server uses (10*10) + 10 file descriptors. • Key reads are slower. W ...
Sharing and Reproducing Database Applications
... (time periods and spatial extents) which she used to obtain the data from Opendata.gov. However, this service is open to the public and, thus, its database has been modified in the mean time. Hence, Alice’s queries will not return the same result when run by Bob (assuming the service does not provid ...
... (time periods and spatial extents) which she used to obtain the data from Opendata.gov. However, this service is open to the public and, thus, its database has been modified in the mean time. Hence, Alice’s queries will not return the same result when run by Bob (assuming the service does not provid ...
Administering Microsoft SQL Server 2012 Databases
... Your network contains two servers named Server1and Server2. Server1 and Server2 run SQL Server 2012 and have access to SAN named SAN1. SAN1 stores all SQL data and log files used by Server1 and Server2. Server1 contains a database named DB1. DB1 is a heavily used database. Users report that when ru ...
... Your network contains two servers named Server1and Server2. Server1 and Server2 run SQL Server 2012 and have access to SAN named SAN1. SAN1 stores all SQL data and log files used by Server1 and Server2. Server1 contains a database named DB1. DB1 is a heavily used database. Users report that when ru ...
worksheet for Chapter 19 - library database
... Select the Queries tab from the Database window and double-click the Wizard option. From tblBorrower move across all of the fields except DateOfBirth to the Selected Fields box. Note: Later you will need to sort by surname. Access sorts according to the sequence in the query. It is therefore imp ...
... Select the Queries tab from the Database window and double-click the Wizard option. From tblBorrower move across all of the fields except DateOfBirth to the Selected Fields box. Note: Later you will need to sort by surname. Access sorts according to the sequence in the query. It is therefore imp ...