Encrypting Wireless Data with VPN Techniques
... • Disadvantages of VPN technology in wireless environment include: – High encryption/decryption overhead. – More moving parts and more likely to break. – Clients and servers can be difficult to configure, deploy and maintain. – Expensive in almost any size network. – Advanced routing is difficult – ...
... • Disadvantages of VPN technology in wireless environment include: – High encryption/decryption overhead. – More moving parts and more likely to break. – Clients and servers can be difficult to configure, deploy and maintain. – Expensive in almost any size network. – Advanced routing is difficult – ...
wireless broadband router base station-g
... 1.8 About the AirStation CD The AirStation does not require any software to be installed on your computer for configuration. The AirStation CD contains client drivers for Buffalo Wireless Adapters (i.e. Notebook Adapter and Desktop PCI Adapter) and the AirStation Client Manager which can be used to ...
... 1.8 About the AirStation CD The AirStation does not require any software to be installed on your computer for configuration. The AirStation CD contains client drivers for Buffalo Wireless Adapters (i.e. Notebook Adapter and Desktop PCI Adapter) and the AirStation Client Manager which can be used to ...
IJSR Paper Format
... Core protocols consisting 5 layer protocol stack viz. radio, baseband, link manager protocol, and logical link control and adaptation protocol, service discovery protocol. ...
... Core protocols consisting 5 layer protocol stack viz. radio, baseband, link manager protocol, and logical link control and adaptation protocol, service discovery protocol. ...
User`s Guide - Amped Wireless
... Wi-Fi Protected Setup – WPS (5.0GHz) .................................................. 23 Wireless Coverage Controls (5.0GHz) ..................................................... 24 Access Schedule (5.0GHz) ...................................................................... 25 2.4GHz WI-FI SETT ...
... Wi-Fi Protected Setup – WPS (5.0GHz) .................................................. 23 Wireless Coverage Controls (5.0GHz) ..................................................... 24 Access Schedule (5.0GHz) ...................................................................... 25 2.4GHz WI-FI SETT ...
Chapter 6 slides, Computer Networking, 3rd edition
... (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
... (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
VPN Routers - D-Link
... network automatically according to a schedule you define, allowing you to turn off your wireless network during off-peak hours, saving energy and keeping your network secure. The D-Link Green Ethernet feature can detect the length of the cables connected to the router and can adjust power usage acco ...
... network automatically according to a schedule you define, allowing you to turn off your wireless network during off-peak hours, saving energy and keeping your network secure. The D-Link Green Ethernet feature can detect the length of the cables connected to the router and can adjust power usage acco ...
Li-Fi-based IoT4bdg - Denny Darlis
... physical objects or "things" embedded with electronics, software, sensors, and network connectivity, which enables these objects to collect and exchange data.[1] ...
... physical objects or "things" embedded with electronics, software, sensors, and network connectivity, which enables these objects to collect and exchange data.[1] ...
Li-Fi-based IoT4bdg - Denny Darlis
... allows objects to be and remotely across existing network infrastructure, creating opportunities for more direct integration between the physical world and computerbased systems, and resulting in improved efficiency, accuracy and economic benefit. ...
... allows objects to be and remotely across existing network infrastructure, creating opportunities for more direct integration between the physical world and computerbased systems, and resulting in improved efficiency, accuracy and economic benefit. ...
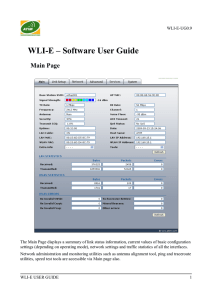
WLI-E – Software User Guide
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
Ethernet - Mt. Hood Community College
... MIMO-OFDM Splits high data rate stream into several low data rate streams, transmits simultaneously using multiple antennae. Possibly up to 248 Mbps with 2 streams Longer range, 70 metres ...
... MIMO-OFDM Splits high data rate stream into several low data rate streams, transmits simultaneously using multiple antennae. Possibly up to 248 Mbps with 2 streams Longer range, 70 metres ...
Installation and User Manual
... dangerous. They may result in a shock or fire hazard. Periodically examine the cord, and, if its appearance indicates damage or deteriorated insulation, have it replaced by your service technician. Protect Power Cords - Route power supply cords so that they are not likely to be walked on or pinched ...
... dangerous. They may result in a shock or fire hazard. Periodically examine the cord, and, if its appearance indicates damage or deteriorated insulation, have it replaced by your service technician. Protect Power Cords - Route power supply cords so that they are not likely to be walked on or pinched ...
D-Link AirPlus Xtreme G DWL-G810
... technology. OFDM works by splitting the radio signal into multiple smaller sub-signals that are then transmitted simultaneously at different frequencies to the receiver. OFDM reduces the amount of crosstalk (interference) in signal transmissions. The D-Link DWLG810 will automatically sense the best ...
... technology. OFDM works by splitting the radio signal into multiple smaller sub-signals that are then transmitted simultaneously at different frequencies to the receiver. OFDM reduces the amount of crosstalk (interference) in signal transmissions. The D-Link DWLG810 will automatically sense the best ...
M2M and IoT protocols
... language/ same protocol. TCP, IP, UDP etc. were some of the results of a quest around that search. However, M2M/ IoT world still lacks a widely accepted and standard protocol, apart from a few protocols that are being currently used. ...
... language/ same protocol. TCP, IP, UDP etc. were some of the results of a quest around that search. However, M2M/ IoT world still lacks a widely accepted and standard protocol, apart from a few protocols that are being currently used. ...
the slide presentation
... Automatic Control of Narrow Directionality Criteria for activation of Narrow Directionality: In quiet no directionality is used For lower levels of noise monaural directionality is activated As the noise level increases narrow directionality engages and its effects are increased accordingly u ...
... Automatic Control of Narrow Directionality Criteria for activation of Narrow Directionality: In quiet no directionality is used For lower levels of noise monaural directionality is activated As the noise level increases narrow directionality engages and its effects are increased accordingly u ...
wireless local area networks - BWN-Lab
... – group of stations using the same radio frequency Access Point – station integrated into the wireless LAN and the distribution system Portal – bridge to other (wired) networks Distribution System – interconnection network to form one logical network (ESS: Extended Service Set) based on several B ...
... – group of stations using the same radio frequency Access Point – station integrated into the wireless LAN and the distribution system Portal – bridge to other (wired) networks Distribution System – interconnection network to form one logical network (ESS: Extended Service Set) based on several B ...
Addendum A - NPTF Principles
... Cost Effective vs. Performance Coverage Supplemental vs. Replacement for Wired Insourced vs. Outsourced Service. ...
... Cost Effective vs. Performance Coverage Supplemental vs. Replacement for Wired Insourced vs. Outsourced Service. ...
AirLive AC.TOP Manual
... This product contains some codes from GPL. In compliance with GPL agreement, AirLive will publish the GPL codes on our website. Please go to www.airlive.com and go to the "Support → GPL" menu to download source code. ...
... This product contains some codes from GPL. In compliance with GPL agreement, AirLive will publish the GPL codes on our website. Please go to www.airlive.com and go to the "Support → GPL" menu to download source code. ...
A1604_Bluetooth_Technology_Powerpoint
... (Industrial, Scientific and Medical Devices) Operates in 2.45 GHz range of RF spectrum ...
... (Industrial, Scientific and Medical Devices) Operates in 2.45 GHz range of RF spectrum ...
TL-WN350G_350GD User Guide - TP-Link
... This equipment has been tested and found to comply with the limits for a class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate ...
... This equipment has been tested and found to comply with the limits for a class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate ...
How a Wireless NetWorks
... There is only one path through our internetwork. However, the same basic things need to happen here, as on the Internet: A message created by any user on one network, needs to be able to reach any user on the other network. The rest of this page is a detailed example that depicts this process. Let’s ...
... There is only one path through our internetwork. However, the same basic things need to happen here, as on the Internet: A message created by any user on one network, needs to be able to reach any user on the other network. The rest of this page is a detailed example that depicts this process. Let’s ...
BODi Multi-WAN BONDING
... The BODi product family uses a proprietary VPN Bonding Protocol to establish a peer to peer connection over multiple WAN interfaces. – VPN BONDING only works BODi to BODi – This can be configured with or without AES 256 Encryption. – The VPN BOND can have multiple end-points configured on both sides ...
... The BODi product family uses a proprietary VPN Bonding Protocol to establish a peer to peer connection over multiple WAN interfaces. – VPN BONDING only works BODi to BODi – This can be configured with or without AES 256 Encryption. – The VPN BOND can have multiple end-points configured on both sides ...
Groningen as a smart city
... bus being by far the most important of the two with more than 13 million passengers and 8 million kilometers per year. Mr Ströhlein said that in the last few years Bremerhaven has invested a lot in mobile portals and information terminals to improve information-provision in rural areas. They want to ...
... bus being by far the most important of the two with more than 13 million passengers and 8 million kilometers per year. Mr Ströhlein said that in the last few years Bremerhaven has invested a lot in mobile portals and information terminals to improve information-provision in rural areas. They want to ...
Wireless USB

Wireless USB is a short-range, high-bandwidth wireless radio communication protocol created by the Wireless USB Promoter Group. Wireless USB is sometimes abbreviated as ""WUSB"", although the USB Implementers Forum discouraged this practice and instead prefers to call the technology Certified Wireless USB to distinguish it from the competing UWB standard.Wireless USB was based on the (now defunct) WiMedia Alliance's ultra-wideband (UWB) common radio platform, which is capable of sending 480 Mbit/s at distances up to 3 metres (9.8 ft) and 110 Mbit/s at up to 10 metres (33 ft). It was designed to operate in the 3.1 to 10.6 GHz frequency range, although local regulatory policies may restrict the legal operating range for any given country.