Linux+ Guide to Linux Certification
... passwords are given out, who can enter premises, and what to do when asked questions by another employee that may reveal protected information • Educating all employees about policies and ensuring they are followed ...
... passwords are given out, who can enter premises, and what to do when asked questions by another employee that may reveal protected information • Educating all employees about policies and ensuring they are followed ...
Unmodified Device Driver Reuse and Improved System Dependability via Virtual Machines
... level. The client interfaces with the driver via a translation module added to the device driver’s OS. This module behaves as a server in a client-server model. It maps client requests into sequences of DD/OS primitives for accessing the device, and converts completed requests into appropriate respo ...
... level. The client interfaces with the driver via a translation module added to the device driver’s OS. This module behaves as a server in a client-server model. It maps client requests into sequences of DD/OS primitives for accessing the device, and converts completed requests into appropriate respo ...
HP WX5000 Access Controller Series
... Automatic radio power adjustment: automatic AP power adjustment features analyze user access status in real time, adapting power requirements based on environmental changes and providing high-quality user access signal coverage Automatic radio channel adjustment: intelligent channel switching and re ...
... Automatic radio power adjustment: automatic AP power adjustment features analyze user access status in real time, adapting power requirements based on environmental changes and providing high-quality user access signal coverage Automatic radio channel adjustment: intelligent channel switching and re ...
Link state Routing - 寬頻網路實驗室
... When topology of network changes or failure, the network knowledge base must also change. The knowledge needs to reflect an accurate, consistent view of the new topology. This view is called convergence. When all routers in an inter-network are operating with the same knowledge, the inter-networ ...
... When topology of network changes or failure, the network knowledge base must also change. The knowledge needs to reflect an accurate, consistent view of the new topology. This view is called convergence. When all routers in an inter-network are operating with the same knowledge, the inter-networ ...
Troubleshooting Your Network
... DHCP Problems Make sure the IP address of the client is on the same network as the ISR If both client and access point are not on the same network, use release and renew ...
... DHCP Problems Make sure the IP address of the client is on the same network as the ISR If both client and access point are not on the same network, use release and renew ...
6DISS: IPv6 Dissemination and Exploitation
... – Address allocation follows the hierarchical structure of the GSN – One /48 prefix is advertised by each of the 8 core nodes – Assign an extra /48 prefix for the backbone ...
... – Address allocation follows the hierarchical structure of the GSN – One /48 prefix is advertised by each of the 8 core nodes – Assign an extra /48 prefix for the backbone ...
A Scheme for a Guaranteed Minimum Throughput Service
... delay (increasing the transfer time) and may also cause ...
... delay (increasing the transfer time) and may also cause ...
K1297-G20 Protocol Tester
... and re-use as much infrastructure from existing networks as possible by using this IMA technology. Using this technology successfully requires a tool for non-intrusive monitoring, which examines all lines without utilizing additional test equipment. By combining innate protocol monitoring for the lu ...
... and re-use as much infrastructure from existing networks as possible by using this IMA technology. Using this technology successfully requires a tool for non-intrusive monitoring, which examines all lines without utilizing additional test equipment. By combining innate protocol monitoring for the lu ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... source to destination. In the above manner code has been written for four border nodes and intermediate nodes. This strategy of routing not only provides the minimal path but also reduces the packet loss ratio. To implement the above routing algorithm the parameters are configured into a NIRGAM simu ...
... source to destination. In the above manner code has been written for four border nodes and intermediate nodes. This strategy of routing not only provides the minimal path but also reduces the packet loss ratio. To implement the above routing algorithm the parameters are configured into a NIRGAM simu ...
Wireless Networks 11, 21–38, 2005
... 2. Basic operation of DSR We base the design of our secure on-demand ad hoc network routing protocol, Ariadne, on the basic operation of the Dynamic Source Routing protocol (DSR) [29–31], since DSR operates entirely on-demand and has been well studied through both simulation and real testbed impleme ...
... 2. Basic operation of DSR We base the design of our secure on-demand ad hoc network routing protocol, Ariadne, on the basic operation of the Dynamic Source Routing protocol (DSR) [29–31], since DSR operates entirely on-demand and has been well studied through both simulation and real testbed impleme ...
Comparing different handover schemes in IP based Micro
... In the next experiment, we study the impact of handoff performance on TCP Newreno throughput. The mobile host performs consecutive handoffs between B1 and B4 and vice versa. The average TCP throughput at the mobile host for all handoff schemes is shown in Figure 4. We observe that the performance of ...
... In the next experiment, we study the impact of handoff performance on TCP Newreno throughput. The mobile host performs consecutive handoffs between B1 and B4 and vice versa. The average TCP throughput at the mobile host for all handoff schemes is shown in Figure 4. We observe that the performance of ...
Internetworking Technology Overview
... flexibility. Each area is key in establishing an efficient and effective internetwork. The challenge when connecting various systems is to support communication between disparate technologies. Different sites, for example, may use different types of media, or they might operate at varying speeds. An ...
... flexibility. Each area is key in establishing an efficient and effective internetwork. The challenge when connecting various systems is to support communication between disparate technologies. Different sites, for example, may use different types of media, or they might operate at varying speeds. An ...
Document
... 4 subnets can be represented with 2 bits (22 = 4) For a class B address, which already uses 16 bits for the network portion, the address would use 18 bits for the subnet portion ...
... 4 subnets can be represented with 2 bits (22 = 4) For a class B address, which already uses 16 bits for the network portion, the address would use 18 bits for the subnet portion ...
Harden Communications
... authentication, integrity, and encryption. Computer authentication is essential in order to ensure that data is actually coming from and going to appropriate computers. If a communication can spoof its origination, or if a destination can be spoofed, then there is no way to know if the information i ...
... authentication, integrity, and encryption. Computer authentication is essential in order to ensure that data is actually coming from and going to appropriate computers. If a communication can spoof its origination, or if a destination can be spoofed, then there is no way to know if the information i ...
Lecture04
... If the SYN is lost… The 3-6 seconds of delay is very long The impatient user may click “reload” User triggers an “abort” of the “connect” Browser “connects” on a new socket Essentially, forces a fast send of a new SYN! ...
... If the SYN is lost… The 3-6 seconds of delay is very long The impatient user may click “reload” User triggers an “abort” of the “connect” Browser “connects” on a new socket Essentially, forces a fast send of a new SYN! ...
Chapter 7
... • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
Data Communication and Network Standards
... In case of computer networks this exchange is done between two devices over a transmission medium. This process involves a communication system which is made up of hardware and software. The hardware part involves the sender and receiver devices and the intermediate devices through which the data pa ...
... In case of computer networks this exchange is done between two devices over a transmission medium. This process involves a communication system which is made up of hardware and software. The hardware part involves the sender and receiver devices and the intermediate devices through which the data pa ...
Spanning Tree Protocol Inter-VLAN Routing
... BPDU guard provides a secure response to invalid configurations, because the administrator must manually re-enable the err-disabled interface after fixing the invalid configuration. It is also possible to set up a time-out interval after which the switch automatically tries to reenable the interface ...
... BPDU guard provides a secure response to invalid configurations, because the administrator must manually re-enable the err-disabled interface after fixing the invalid configuration. It is also possible to set up a time-out interval after which the switch automatically tries to reenable the interface ...
DES-3810 Series Sales Guide - D-Link
... Packet Filtering that makes the network exposed to un-predictable virus or worm attack from mobile users in intranet. When CPU is under attack, switch becomes inaccessible and administrators are not possible to cut troubled traffic off remotely which makes the damage bigger and worse. ...
... Packet Filtering that makes the network exposed to un-predictable virus or worm attack from mobile users in intranet. When CPU is under attack, switch becomes inaccessible and administrators are not possible to cut troubled traffic off remotely which makes the damage bigger and worse. ...
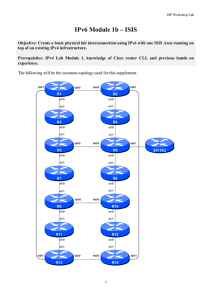
Module 01 - IPv6 ISIS and iBGP
... The system changes a little for IPv6. While the RIRs still allocate address space to their membership according to their membership needs, the justification to receive an IPv6 allocation is somewhat lighter than it is for IPv4. A bigger advantage starts with the customer assignments made by the ISP ...
... The system changes a little for IPv6. While the RIRs still allocate address space to their membership according to their membership needs, the justification to receive an IPv6 allocation is somewhat lighter than it is for IPv4. A bigger advantage starts with the customer assignments made by the ISP ...
VoIP Performance in SIP-Based Vertical Handovers Between WLAN
... networks can be roughly classified into loosely coupled and tightly coupled [7]. In the tightly coupled solution, the WLAN is connected to the cellular core network as any other radio access network (RAN,) such as GERAN or UTRAN. In the loosely coupled approach, WLAN and cellular networks are comple ...
... networks can be roughly classified into loosely coupled and tightly coupled [7]. In the tightly coupled solution, the WLAN is connected to the cellular core network as any other radio access network (RAN,) such as GERAN or UTRAN. In the loosely coupled approach, WLAN and cellular networks are comple ...
iCAMView - SuperDroid Robots
... surveillance. It can be accessed from anywhere in the world via a standard browser by entering the IP, account and password. Each system can simultaneously support any two combinations of USB PC cameras be it regular, infrared or pan-tilt. With its built-in web-server, iCAMView can stream video imag ...
... surveillance. It can be accessed from anywhere in the world via a standard browser by entering the IP, account and password. Each system can simultaneously support any two combinations of USB PC cameras be it regular, infrared or pan-tilt. With its built-in web-server, iCAMView can stream video imag ...
Network Monitoring
... Has many option for capturing raw data, but it does not provide any analysis capability for the captured data. ...
... Has many option for capturing raw data, but it does not provide any analysis capability for the captured data. ...
Emulation of RDRN on an ATM-Testbed and a Comparative
... IP over ATM specification says that the MTU cannot be larger than 9180 bytes; hence the CLIP can pass a packet of the above size to the “glue_layer”. Hence, when the DLC layer would attach its own header and trailer, it would cause an overflow on the ENI card. In the above case the segmentation ...
... IP over ATM specification says that the MTU cannot be larger than 9180 bytes; hence the CLIP can pass a packet of the above size to the “glue_layer”. Hence, when the DLC layer would attach its own header and trailer, it would cause an overflow on the ENI card. In the above case the segmentation ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.