BigPond ElitE™ WiRElESS
... 300kbps to 1Mbps in other coverage areas. Actual speeds vary due to factors such as distance from the cell, local conditions, user numbers, hardware software and other factors. Speeds vary due to factors such as distance from the cell, local conditions, number of users, download source, associated c ...
... 300kbps to 1Mbps in other coverage areas. Actual speeds vary due to factors such as distance from the cell, local conditions, user numbers, hardware software and other factors. Speeds vary due to factors such as distance from the cell, local conditions, number of users, download source, associated c ...
How Networking Works
... Local Area Network (LAN) is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. The defining characteristics of LANs, in contrast to wide-area networks (WANs), include their usually higher data-transfer rates and small ...
... Local Area Network (LAN) is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. The defining characteristics of LANs, in contrast to wide-area networks (WANs), include their usually higher data-transfer rates and small ...
13707579013302_CIS 202 TC,NW & WT-1
... • The three types of networks include: • Local area network (LAN) A computer network that uses cables or radio signals to link two or more computers within a geographically limited area, generally one building or a group of buildings. A networked office building, school, or home usually contains a s ...
... • The three types of networks include: • Local area network (LAN) A computer network that uses cables or radio signals to link two or more computers within a geographically limited area, generally one building or a group of buildings. A networked office building, school, or home usually contains a s ...
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727 PP 37-41 www.iosrjournals.org
... A malicious node may disrupt the normal operation of a network by dropping packets.This type of attack can be classified into two types: (a) Black hole attack and (b) Gray holeattack. b. Blackhole Attack In blackhole attack, a malicious node uses its routing protocol in order to advertise itselffor ...
... A malicious node may disrupt the normal operation of a network by dropping packets.This type of attack can be classified into two types: (a) Black hole attack and (b) Gray holeattack. b. Blackhole Attack In blackhole attack, a malicious node uses its routing protocol in order to advertise itselffor ...
Internet technologies
... Internet Protocol Version 4 (IPv4) Internet Protocol being a layer-3 protocol (OSI) takes data Segments from layer-4 (Transport) and divides it into what’s called packet. IP packet encapsulates data unit received from above layer and adds its own header information. ...
... Internet Protocol Version 4 (IPv4) Internet Protocol being a layer-3 protocol (OSI) takes data Segments from layer-4 (Transport) and divides it into what’s called packet. IP packet encapsulates data unit received from above layer and adds its own header information. ...
“The thin-client model is an alternative to the traditional approach of
... “The thin-client model is an alternative to the traditional approach of expensive workstations. Under a traditional (fat-client) model, applications run on the individual workstations...Under a thin-client model, the applications run on a network server and the local clients (workstations) are used ...
... “The thin-client model is an alternative to the traditional approach of expensive workstations. Under a traditional (fat-client) model, applications run on the individual workstations...Under a thin-client model, the applications run on a network server and the local clients (workstations) are used ...
5 10 Wired Network Basics - Web Design John Cabot University
... Enter an SSID for the network Activate WEP, WPA, or PSK and create an encryption key Set up the wireless workstations Connect an Internet access device ...
... Enter an SSID for the network Activate WEP, WPA, or PSK and create an encryption key Set up the wireless workstations Connect an Internet access device ...
Relationship between bandwidth and the transmission capacity of a
... Internetworking, Connectivity & Open System • Internetworking => The linking of separate networks, each of which retains its own identity, into an interconnected network. • Connectivity => The ability of computers and computer-based devices to communicate with one another and share information in a ...
... Internetworking, Connectivity & Open System • Internetworking => The linking of separate networks, each of which retains its own identity, into an interconnected network. • Connectivity => The ability of computers and computer-based devices to communicate with one another and share information in a ...
networking fundamentals
... use by everyone within an organization. An intranet might consist of an internal e-mail system, a message board and one or more Web site portals that contain company news, forms, and personnel information. Access to an intranet’s web site is restricted by a ...
... use by everyone within an organization. An intranet might consist of an internal e-mail system, a message board and one or more Web site portals that contain company news, forms, and personnel information. Access to an intranet’s web site is restricted by a ...
EdgeRouter Lite
... EdgeRouter models are even faster, capable of routing up to 2 million+ packets per second. Powered by a proprietary and intuitive graphical interface, EdgeOS™, EdgeRouters can easily be configured for routing, security, and management features required to efficiently run your network. For advanced n ...
... EdgeRouter models are even faster, capable of routing up to 2 million+ packets per second. Powered by a proprietary and intuitive graphical interface, EdgeOS™, EdgeRouters can easily be configured for routing, security, and management features required to efficiently run your network. For advanced n ...
ch04-Networking
... Suppose that a user on a client computer in LAN A requests a Web page from the web server located in a different LAN Web browser (application layer software) passes URL to the TCP/IP software (Network Layer). TCP/IP then will search its network layer address table and find the IP address for t ...
... Suppose that a user on a client computer in LAN A requests a Web page from the web server located in a different LAN Web browser (application layer software) passes URL to the TCP/IP software (Network Layer). TCP/IP then will search its network layer address table and find the IP address for t ...
CV200 Ethernet to E1/T1 converter CSU/DSU (En)
... network access. The CV-200 includes a powerful Ethernet bridge. It will suit most network interconnection needs thanks to its Ethernet frame filtering, compression algorithm, VLAN and other protocol transparency features. The CV-200 encapsulates Ethernet frames over HDLC or PPP-BCP protocol ...
... network access. The CV-200 includes a powerful Ethernet bridge. It will suit most network interconnection needs thanks to its Ethernet frame filtering, compression algorithm, VLAN and other protocol transparency features. The CV-200 encapsulates Ethernet frames over HDLC or PPP-BCP protocol ...
What is a Network?
... Disadvantages: Trackers are unreliable and if it goes down, the file is lost. ...
... Disadvantages: Trackers are unreliable and if it goes down, the file is lost. ...
MCN 7200 Advanced Internetworking Protocols
... This course assumes the basic knowledge regarding the Internet and its protocols. It offers advanced level treatment of data transport and switching concepts; TCP/IP protocol stack with detailed analysis. It also looks at architectures of network components mainly routers and switches and their type ...
... This course assumes the basic knowledge regarding the Internet and its protocols. It offers advanced level treatment of data transport and switching concepts; TCP/IP protocol stack with detailed analysis. It also looks at architectures of network components mainly routers and switches and their type ...
Chapter 5 Local Area Network Concepts and Architecture
... • Utilities support end-user application program • Determine data to be send at originating end • Process data at receiving end ...
... • Utilities support end-user application program • Determine data to be send at originating end • Process data at receiving end ...
Chapter 7 PowerPoint Presentation
... No server running the DHCP Service on the network • IP address provided by Automatic Private IP Addressing • IP address is 169.254.0.0 through 169.254.255.255 ...
... No server running the DHCP Service on the network • IP address provided by Automatic Private IP Addressing • IP address is 169.254.0.0 through 169.254.255.255 ...
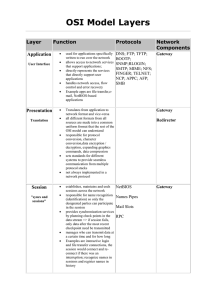
OSI Model Layers
... sets standards for different systems to provide seamless communication from multiple protocol stacks not always implemented in a network protocol establishes, maintains and ends sessions across the network responsible for name recognition (identification) so only the designated parties can participa ...
... sets standards for different systems to provide seamless communication from multiple protocol stacks not always implemented in a network protocol establishes, maintains and ends sessions across the network responsible for name recognition (identification) so only the designated parties can participa ...
Networking
... organisation and in each branch office, by connecting together in networks. A distributed system is a system in which a job is performed by a number of computers that are linked through a communication network.. ...
... organisation and in each branch office, by connecting together in networks. A distributed system is a system in which a job is performed by a number of computers that are linked through a communication network.. ...
Chapter 1
... RRAS can allow clients to connect remotely to the server as if they were on the network. VPN is an ...
... RRAS can allow clients to connect remotely to the server as if they were on the network. VPN is an ...
Query Processing for Sensor Networks
... Preservation of energy and bandwidth Ratio of sending 1 bit vs. executing one instruction 220 to 2900 depending on architecture ...
... Preservation of energy and bandwidth Ratio of sending 1 bit vs. executing one instruction 220 to 2900 depending on architecture ...
Transcript: Network Hardening Techniques Part 1
... Web browser and a Web server. HTTPS uses either TLS or SSL technology. IPsec is a network layer IP security protocol suite that can use multiple methods to mutually authentic both ends of the communication channel. It also will encrypt all data transmissions. Unlike most other protocols, it can prov ...
... Web browser and a Web server. HTTPS uses either TLS or SSL technology. IPsec is a network layer IP security protocol suite that can use multiple methods to mutually authentic both ends of the communication channel. It also will encrypt all data transmissions. Unlike most other protocols, it can prov ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.