ActionRuler_TP_front_08Mar11 copy
... INTRACOM TELECOM is an international telecommunication systems vendor operating in Eastern Europe, the Middle East & Africa, Russia, the CIS and Asia-Pacific. Over 100 customers in more than 50 countries choose INTRACOM TELECOM for its state-of-the-art products and solutions. INTRACOM TELECOM has 2, ...
... INTRACOM TELECOM is an international telecommunication systems vendor operating in Eastern Europe, the Middle East & Africa, Russia, the CIS and Asia-Pacific. Over 100 customers in more than 50 countries choose INTRACOM TELECOM for its state-of-the-art products and solutions. INTRACOM TELECOM has 2, ...
Windows Server 2008
... to transport, and how devices connect to a network • Describe network transport and communications protocols, and determine which protocols are used in specific computer operating systems • Explain how to integrate different operating systems on the same network ...
... to transport, and how devices connect to a network • Describe network transport and communications protocols, and determine which protocols are used in specific computer operating systems • Explain how to integrate different operating systems on the same network ...
Using NViz tool for Environmental Sensor Networks Anh-Vu Dinh-Duc , Non-member
... various visualization tools have been created for certain projects so far, these tools can only be used in certain scenarios, due to their hard-coded packet formats and network’s properties. To speed up development process, a visualization tool which can adapt to any kind of WSN is essentially neces ...
... various visualization tools have been created for certain projects so far, these tools can only be used in certain scenarios, due to their hard-coded packet formats and network’s properties. To speed up development process, a visualization tool which can adapt to any kind of WSN is essentially neces ...
DVTS with dynamic FEC - Asia Pacific Advanced Network
... the motion in DV stream – Sometimes DV stream does not contains much mobility – Like power-point presentations, face to face conferencing – Dynamically adjust frame rate based on amount of motion ...
... the motion in DV stream – Sometimes DV stream does not contains much mobility – Like power-point presentations, face to face conferencing – Dynamically adjust frame rate based on amount of motion ...
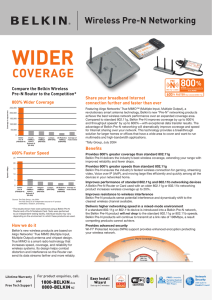
coverage
... achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up to 800% and throughput speeds* by up to 600%—with exceptional data transfer results. The advantage of Belkin Pre-N networking will dramatically improve cov ...
... achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up to 800% and throughput speeds* by up to 600%—with exceptional data transfer results. The advantage of Belkin Pre-N networking will dramatically improve cov ...
Setup Networking in Linux over VMware
... (9) Now the networking is ready to run. You can check your network setting by using “ifconfig” command: ...
... (9) Now the networking is ready to run. You can check your network setting by using “ifconfig” command: ...
Mobile IP: enable mobility for IP
... Mobility is enabled, even across heterogeneous media A mobile host is able to communicate with other hosts that do not implement Mobile IP There is no additional constraints on the assignment of IP addresses No requirement is placed on the layer-2 ...
... Mobility is enabled, even across heterogeneous media A mobile host is able to communicate with other hosts that do not implement Mobile IP There is no additional constraints on the assignment of IP addresses No requirement is placed on the layer-2 ...
Our Team is Proud to Deliver the Best Network Solutions
... Build a cost effective strategy to meet client requirement. Find the right balance between performance and cost. ...
... Build a cost effective strategy to meet client requirement. Find the right balance between performance and cost. ...
ppt
... involved in wide-area networks (WANs) and local area networks (LANs). 2. To develop an understanding of modern network architectures from a design and performance perspective. 3. To expose students to some of the current technologies. Networks: Introduction ...
... involved in wide-area networks (WANs) and local area networks (LANs). 2. To develop an understanding of modern network architectures from a design and performance perspective. 3. To expose students to some of the current technologies. Networks: Introduction ...
Strong Customer Success 20161212
... were impacting core business applications and we were not delivering on our promise of a great user experience. Our partners at Telstra suggested looking at Sinefa. We created a free trial account and within within 10 minutes of deploying a probe, we had indentified the underlying cause (device updat ...
... were impacting core business applications and we were not delivering on our promise of a great user experience. Our partners at Telstra suggested looking at Sinefa. We created a free trial account and within within 10 minutes of deploying a probe, we had indentified the underlying cause (device updat ...
ppt
... • Applications with IP-address content – Need AGL (Application Level Gateway) – Typically applications that rely on IP addresses in payload do not work across a private-public network boundary – Some NATs can translate IP addresses in payload • NAT device can be a target for attacks • NAT behaviour ...
... • Applications with IP-address content – Need AGL (Application Level Gateway) – Typically applications that rely on IP addresses in payload do not work across a private-public network boundary – Some NATs can translate IP addresses in payload • NAT device can be a target for attacks • NAT behaviour ...
Document
... Uses IP to send TCP segments Contains additional information that allows it to order packets and resend them if error occurs Has extra layer of abstraction, by using a communication port Communication port – a numerical value ( 0 – 65535) used to distinguish one application or service from another ...
... Uses IP to send TCP segments Contains additional information that allows it to order packets and resend them if error occurs Has extra layer of abstraction, by using a communication port Communication port – a numerical value ( 0 – 65535) used to distinguish one application or service from another ...
Firewalls
... – Purchasing a license agreement will include media required to install and configure the firewall – Most firewalls are available for Windows, Unix, and Linux – Can also purchase design of the firewall rulebase with configuration, maintenance and support • Worthwhile unless you really understand wha ...
... – Purchasing a license agreement will include media required to install and configure the firewall – Most firewalls are available for Windows, Unix, and Linux – Can also purchase design of the firewall rulebase with configuration, maintenance and support • Worthwhile unless you really understand wha ...
Chapter 2 Introduction
... restricted access policies based on time-of-day, Web site addresses and address keywords, and share high-speed cable/DSL Internet access for up to 253 computers. In addition to the Network Address Translation (NAT) feature, the built-in firewall protects you from hackers. With minimum setup, you can ...
... restricted access policies based on time-of-day, Web site addresses and address keywords, and share high-speed cable/DSL Internet access for up to 253 computers. In addition to the Network Address Translation (NAT) feature, the built-in firewall protects you from hackers. With minimum setup, you can ...
NAT
... world is concerned: range of addresses not needed from ISP: just one IP address for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices inside local net not explicitly addre ...
... world is concerned: range of addresses not needed from ISP: just one IP address for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices inside local net not explicitly addre ...
Introduction - WordPress.com
... the interframe time interval. The four intervals are depicted: • SIFS (Short InterFrame Spacing) is used to allow the parties in a single dialog the chance to go first including letting the receiver send a CTS and an ACK and the sender to transmit the next fragment. • PIFS (PCF InterFrame Spacing) i ...
... the interframe time interval. The four intervals are depicted: • SIFS (Short InterFrame Spacing) is used to allow the parties in a single dialog the chance to go first including letting the receiver send a CTS and an ACK and the sender to transmit the next fragment. • PIFS (PCF InterFrame Spacing) i ...
LinkWay ™
... LinkWayS2 -based terminals are controlled by a full-featured network control center (NCC) management station. The one-rack-unit NCC server connects to any standard LinkWayS2 modem and manages TDMA network timing, synchronization, terminal acquisition, network configuration, and bandwidth management. ...
... LinkWayS2 -based terminals are controlled by a full-featured network control center (NCC) management station. The one-rack-unit NCC server connects to any standard LinkWayS2 modem and manages TDMA network timing, synchronization, terminal acquisition, network configuration, and bandwidth management. ...
lecture02-swtching
... Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. Since packets are treated independently, it is possible to route around link and node failures. Since every packet must carry the full address of the destination, the overhead ...
... Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. Since packets are treated independently, it is possible to route around link and node failures. Since every packet must carry the full address of the destination, the overhead ...
Simulators for Sensor Networks - University of Virginia, Department
... – Originally built for wired networks, later extended for wireless. – Supposedly, does not work well for large ...
... – Originally built for wired networks, later extended for wireless. – Supposedly, does not work well for large ...
Broadband A to Z Glossary
... address. The NAT system is set up as a way of only using one public-facing IP address, giving any machines or devices connected to the Internet behind this a private address. This is accessible only to other devices on the same network. The opposite of this is a Routed IP solution (see Routed IP). ...
... address. The NAT system is set up as a way of only using one public-facing IP address, giving any machines or devices connected to the Internet behind this a private address. This is accessible only to other devices on the same network. The opposite of this is a Routed IP solution (see Routed IP). ...
VIP-800 - Valcom
... fans, power supplies, etc.) with the control and terminal strip accessible. One wood screw is included for mounting. ...
... fans, power supplies, etc.) with the control and terminal strip accessible. One wood screw is included for mounting. ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.