Dynamic Host Configuration Protocol
... To deliver host-specific configuration parameters from a DHCP server to a host. Allocation of network addresses to hosts. ...
... To deliver host-specific configuration parameters from a DHCP server to a host. Allocation of network addresses to hosts. ...
Murphy loves CI: Unfolding and Improving Constructive Interference
... testbeds that (i) as the number of concurrent transmitters increases the packet reception ratio (PRR)1 increases; (ii) the only factor that affects CI is not meeting the temporal offset of ≤ 0.5 µs among concurrent transmissions. Wang et al. [9] studied the scalability of CI. They argue that PRR of ...
... testbeds that (i) as the number of concurrent transmitters increases the packet reception ratio (PRR)1 increases; (ii) the only factor that affects CI is not meeting the temporal offset of ≤ 0.5 µs among concurrent transmissions. Wang et al. [9] studied the scalability of CI. They argue that PRR of ...
Document
... Delivery and Routing of IP Packet 6.2 DIRECT VERSUS INDIRECT DELIVERY Direct Delivery • Direct delivery occurs when the source and destination of the packet are allocated on the same physical network or if the delivery is between the last router and the destination host. Figure 6-1 Direct delivery ...
... Delivery and Routing of IP Packet 6.2 DIRECT VERSUS INDIRECT DELIVERY Direct Delivery • Direct delivery occurs when the source and destination of the packet are allocated on the same physical network or if the delivery is between the last router and the destination host. Figure 6-1 Direct delivery ...
network of networks
... via its own internal-layer actions relying on services provided by layer below Zhang, Net. Admin, Spring 2012 ...
... via its own internal-layer actions relying on services provided by layer below Zhang, Net. Admin, Spring 2012 ...
Slides
... flow only • Receiver –oriented approach • Maintains soft –state. • Traffic control and policy control parameters are opaque to it. • Is dependent on present routing protocols • Provides transparent operation through routers that do not support it. Advanced Computer Networks ...
... flow only • Receiver –oriented approach • Maintains soft –state. • Traffic control and policy control parameters are opaque to it. • Is dependent on present routing protocols • Provides transparent operation through routers that do not support it. Advanced Computer Networks ...
Chapter 1: A First Look at Windows 2000 Professional
... Each protocol has strengths and weaknesses A suite, or stack, of protocols allows a number of protocols to work cooperatively Major protocol suites are TCP/IP, IPX/SPX, and NetBEUI Each suite contains many smaller protocols, each of which has its own network function ...
... Each protocol has strengths and weaknesses A suite, or stack, of protocols allows a number of protocols to work cooperatively Major protocol suites are TCP/IP, IPX/SPX, and NetBEUI Each suite contains many smaller protocols, each of which has its own network function ...
SNMP Network Management Concepts
... an interface for the network manager to monitor and control the network a database of information extracted from the MIBs of all the managed entities in the network the capability of translating the network manager’s requirements into the actual monitoring and control of remote elements in the netwo ...
... an interface for the network manager to monitor and control the network a database of information extracted from the MIBs of all the managed entities in the network the capability of translating the network manager’s requirements into the actual monitoring and control of remote elements in the netwo ...
1 Computer network technology
... In the network communication, different computer systems must have certain rules, so that information can be transmitted accurately. These rules are called network transmission protocol. Take the internet as an example. When the users visit different homepage using browsers, they may have to connect ...
... In the network communication, different computer systems must have certain rules, so that information can be transmitted accurately. These rules are called network transmission protocol. Take the internet as an example. When the users visit different homepage using browsers, they may have to connect ...
presentation
... Truncated Reverse Path Broadcasting (TRPB) RPB still delivers all packets to all nodes in the network. TRPB allows subnetworks (typically LANs) to only participate in a multicast if they contain at least one interested host. A simple protocol called IGMP (Internet Group Management Protocol) was def ...
... Truncated Reverse Path Broadcasting (TRPB) RPB still delivers all packets to all nodes in the network. TRPB allows subnetworks (typically LANs) to only participate in a multicast if they contain at least one interested host. A simple protocol called IGMP (Internet Group Management Protocol) was def ...
CCNA2 3.0-08 TCPIP Suite Error and Control Messages
... Internet Control Message Protocol (ICMP) is component of TCP/IP that addresses this basic limitation. NOTE: • ICMP does not overcome the unreliability issues in IP • reliability must be provided by upper layer protocols, if it is needed. ICMP is an error reporting protocol for IP. ...
... Internet Control Message Protocol (ICMP) is component of TCP/IP that addresses this basic limitation. NOTE: • ICMP does not overcome the unreliability issues in IP • reliability must be provided by upper layer protocols, if it is needed. ICMP is an error reporting protocol for IP. ...
Computers Are Your Future Chapter 7: Networks: Communicating and Sharing Resources Twelfth Edition
... • Internet Protocol (IP) • Provides a distinct identification to any computer connected to the Internet: the IP address or Internet address Copyright © 2012 Pearson Education, Inc. Publishing as Prentice Hall ...
... • Internet Protocol (IP) • Provides a distinct identification to any computer connected to the Internet: the IP address or Internet address Copyright © 2012 Pearson Education, Inc. Publishing as Prentice Hall ...
WN7 92-93-2 Random Access and Wireless LAN
... the available spectrum into two parts is both cumbersome and inefficient. The effect of the busy tone is achieved by preceding the actual data transfer by a handshake between the transmitter and the receiver. This handshake is used to convey an imminent reception to the hidden nodes. Before transmit ...
... the available spectrum into two parts is both cumbersome and inefficient. The effect of the busy tone is achieved by preceding the actual data transfer by a handshake between the transmitter and the receiver. This handshake is used to convey an imminent reception to the hidden nodes. Before transmit ...
WAN Backbones
... ATM Service Categories ATM provides 4 service categories: CBR (Constant Bit Rate): A constant bandwidth is reserved and guaranteed by the network UBR (Unspecified Bit Rate): Data is transmitted when bandwidth is available, and not when bandwidth is not available ABR (Available Bit Rate): The networ ...
... ATM Service Categories ATM provides 4 service categories: CBR (Constant Bit Rate): A constant bandwidth is reserved and guaranteed by the network UBR (Unspecified Bit Rate): Data is transmitted when bandwidth is available, and not when bandwidth is not available ABR (Available Bit Rate): The networ ...
CWSA_Session1_Nita-Rotaru - The Center for Wireless Systems
... Attacker disseminates request quickly throughout the network suppressing any later legitimate request ...
... Attacker disseminates request quickly throughout the network suppressing any later legitimate request ...
File: IIB ACCEPTABLE USE POLICY for Internet/Online
... We in the Oak Hills Local School District are pleased to be able to offer our students and staff access to computer technology, including access to the Internet, certain online services, and the Oak Hills schools computer network. Access to the networks allows students and staff to conduct research ...
... We in the Oak Hills Local School District are pleased to be able to offer our students and staff access to computer technology, including access to the Internet, certain online services, and the Oak Hills schools computer network. Access to the networks allows students and staff to conduct research ...
Separation of the Control Plane and Forwarding Plane in
... processors. However, routers based on this technology are, in fact, traditional computers connected by a Backplane or local area network. This aspect enables users to place themselves within the framework of a computer cluster for the interconnection between CEs and FEs. By adopting this assumption, ...
... processors. However, routers based on this technology are, in fact, traditional computers connected by a Backplane or local area network. This aspect enables users to place themselves within the framework of a computer cluster for the interconnection between CEs and FEs. By adopting this assumption, ...
Chapter 6 slides, Computer Networking, 3rd edition
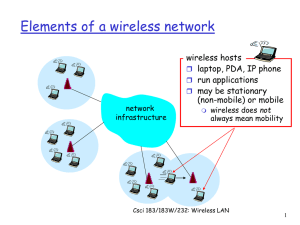
... (Mobile Ad hoc Networks) working group Csci 183/183W/232: Wireless LAN ...
... (Mobile Ad hoc Networks) working group Csci 183/183W/232: Wireless LAN ...
ch02
... The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made ...
... The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made ...
Chapter 3: Planning Network Data Flow
... • Pathping can be used to view the routers used to move a packet from the local host to a remote host • However, the Pathping utility sends 100 packets to each router in the path to provide a more accurate measure of response times ...
... • Pathping can be used to view the routers used to move a packet from the local host to a remote host • However, the Pathping utility sends 100 packets to each router in the path to provide a more accurate measure of response times ...
Chapter 6 slides, Computer Networking, 3rd edition
... Mobility and higherlayer protocols Summary ...
... Mobility and higherlayer protocols Summary ...
Week_Ten_Network_ppt
... Frame Relay Frame relay is a telecommunication service designed for cost-efficient data transmission for intermittent traffic between local area networks (LANs) and between end-points in a wide area network (WAN). Frame relay puts data in a variable-size unit called a frame and leaves any necessary ...
... Frame Relay Frame relay is a telecommunication service designed for cost-efficient data transmission for intermittent traffic between local area networks (LANs) and between end-points in a wide area network (WAN). Frame relay puts data in a variable-size unit called a frame and leaves any necessary ...
Actiontec GT724R DSL Modem with 4 Port Ethernet Router Product
... as possible to deploy and use, the graphical user interface was redesigned from the ground up. Now it’s a snap to check the status of the network or the broadband connection’s IP address. Nearly all other configuration options are one or two clicks away, and the home page can be customized with spec ...
... as possible to deploy and use, the graphical user interface was redesigned from the ground up. Now it’s a snap to check the status of the network or the broadband connection’s IP address. Nearly all other configuration options are one or two clicks away, and the home page can be customized with spec ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.