Presentación de PowerPoint
... – Tenant creates his own network(s) and router(s) allowing complex network topologies for multi-tier applications. ...
... – Tenant creates his own network(s) and router(s) allowing complex network topologies for multi-tier applications. ...
Document
... Let Dx = [Dx(y): y є N ] be node x’s distance vector, which is the vector of cost estimates from x to all other nodes, y, in N. Each node x maintains the following routing info: cost to each directly attached neighbor v of x: c(x,v) the distance vector containing the estimate of the cost to all ...
... Let Dx = [Dx(y): y є N ] be node x’s distance vector, which is the vector of cost estimates from x to all other nodes, y, in N. Each node x maintains the following routing info: cost to each directly attached neighbor v of x: c(x,v) the distance vector containing the estimate of the cost to all ...
PPT
... • Problems are frequently not caused by the network: – Your hard disc, your application (GridFTP vrs HTTP) etc. – If it is the network, look in the last mile, e.g. the firewall • GridMon is the infrastructure for UK academic network performance monitoring • There’s lots happening. The UK has its fin ...
... • Problems are frequently not caused by the network: – Your hard disc, your application (GridFTP vrs HTTP) etc. – If it is the network, look in the last mile, e.g. the firewall • GridMon is the infrastructure for UK academic network performance monitoring • There’s lots happening. The UK has its fin ...
YN013853859
... Ethernet connection to places where wired devices may not be able to access. In simple terms, an access point receives wireless Ethernet data form wireless devices and places that information on a wired Ethernet cable. Wireless means transferring the signals without wires using radio waves, infra re ...
... Ethernet connection to places where wired devices may not be able to access. In simple terms, an access point receives wireless Ethernet data form wireless devices and places that information on a wired Ethernet cable. Wireless means transferring the signals without wires using radio waves, infra re ...
Network slides
... Retrieved from: http://global.mci.com/about/network/maps/?flash=1&theme=/, Sept 5/2003 See this site also for interesting network statistics (e.g. latencies) ...
... Retrieved from: http://global.mci.com/about/network/maps/?flash=1&theme=/, Sept 5/2003 See this site also for interesting network statistics (e.g. latencies) ...
Internet Routing Availability
... competence-challenged ISP in New York, is announcing our routes to the Internet. In English, that means that they are claiming that all our traffic should be passing through them, when of course it should not. Those portions of the net that are "closer" (in network topology terms) to Con Ed will sen ...
... competence-challenged ISP in New York, is announcing our routes to the Internet. In English, that means that they are claiming that all our traffic should be passing through them, when of course it should not. Those portions of the net that are "closer" (in network topology terms) to Con Ed will sen ...
DS35676681
... implementation, our main objective was to study the working of OLSR routing protocol and then to measure and analyse the performance of reactive routing protocols in mobile ad hoc network. Keeping this main objective in mind the following objectives are stated: Study the various routing protocols ...
... implementation, our main objective was to study the working of OLSR routing protocol and then to measure and analyse the performance of reactive routing protocols in mobile ad hoc network. Keeping this main objective in mind the following objectives are stated: Study the various routing protocols ...
ch01 - kuroski.net
... Order automatically entered into processing server Order-processing server generates bill Order-processing server sends data to processing area Inventory automatically adjusted for order Item sent out to customer ...
... Order automatically entered into processing server Order-processing server generates bill Order-processing server sends data to processing area Inventory automatically adjusted for order Item sent out to customer ...
Networking
... • Used by the public switched telephone network to send data over a physical end-to-end circuit • Provides a direct connection between devices o Packet switching • Used for computer communication • Divides and sends outgoing messages as packets, which are reassembled on receipt • More efficient and ...
... • Used by the public switched telephone network to send data over a physical end-to-end circuit • Provides a direct connection between devices o Packet switching • Used for computer communication • Divides and sends outgoing messages as packets, which are reassembled on receipt • More efficient and ...
Computers Are Your Future Twelfth Edition
... • Used by the public switched telephone network to send data over a physical end-to-end circuit • Provides a direct connection between devices o Packet switching • Used for computer communication • Divides and sends outgoing messages as packets, which are reassembled on receipt • More efficient and ...
... • Used by the public switched telephone network to send data over a physical end-to-end circuit • Provides a direct connection between devices o Packet switching • Used for computer communication • Divides and sends outgoing messages as packets, which are reassembled on receipt • More efficient and ...
Lecture 8: Routing I Distance-vector Algorithms
... Hosts sets up path out-of-band, requires connection setup Write (input id, output id, next hop) into each router on path Flexible (one path per flow) Send packet with path id Router looks up input, swaps for output, forwards on next hop Repeat until reach destination Table lookup for forwarding (fas ...
... Hosts sets up path out-of-band, requires connection setup Write (input id, output id, next hop) into each router on path Flexible (one path per flow) Send packet with path id Router looks up input, swaps for output, forwards on next hop Repeat until reach destination Table lookup for forwarding (fas ...
Ch. 8 TCP/IP Suite Error and Control Messages (ICMP)
... proper configuration of IP address and subnet mask. A default gateway must also be configured if datagrams are to travel outside of the local network. • A router also must have the TCP/IP protocol properly configured on its interfaces, and it must use an appropriate routing protocol. If these co ...
... proper configuration of IP address and subnet mask. A default gateway must also be configured if datagrams are to travel outside of the local network. • A router also must have the TCP/IP protocol properly configured on its interfaces, and it must use an appropriate routing protocol. If these co ...
Universal Plug and Play Machine Models
... and when those advertisements will expire. Services interact with entities in the external (physical) world through the actuators and sensors of a device. A sample UPnP device is illustrated in Figure 1. General Restrictions: In general, the following restrictions apply. Control points and devices i ...
... and when those advertisements will expire. Services interact with entities in the external (physical) world through the actuators and sensors of a device. A sample UPnP device is illustrated in Figure 1. General Restrictions: In general, the following restrictions apply. Control points and devices i ...
Leased line WAN connections.
... connections use microwave transmissions as an over-the-air method of transmitting voice and data, just like WiMAX. They can be an effective means of extending networks into places that are hard to reach. Satellite WAN connections use microwave radio relay as the method of transmitting data through t ...
... connections use microwave transmissions as an over-the-air method of transmitting voice and data, just like WiMAX. They can be an effective means of extending networks into places that are hard to reach. Satellite WAN connections use microwave radio relay as the method of transmitting data through t ...
Hacking Part 1
... C:\> snmputil walk public
C:\> snmputil walk 10.10.0.2 public .1.3.6.1.4.1.77.1.2.25
Can provide usernames, OS version, share names/paths, running services,
etc.
Countermeasures:
Block TCP/UDP 161 at network perimeter
Use an excellent password
Disable SNMP if not require ...
... C:\> snmputil walk
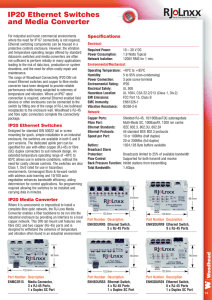
IP20 Ethernet Switches and Media Converter
... protective controls enclosure. However, the vibration and temperature operating ranges offered by standard datacoms switches and media converters are often not sufficient to perform reliably in many applications leading to the risk of data loss, production or system downtime, and the need for often ...
... protective controls enclosure. However, the vibration and temperature operating ranges offered by standard datacoms switches and media converters are often not sufficient to perform reliably in many applications leading to the risk of data loss, production or system downtime, and the need for often ...
GTS SAN Usage A UNIX SysAdmin`s View of How A SAN Works
... are allowed to see each other thru the ACL. LUNs are Masked from Servers not in the ACL ...
... are allowed to see each other thru the ACL. LUNs are Masked from Servers not in the ACL ...
Host-Specific Routing
... • Next-Hop Routing – table only holds the address of the next hop (instead info regarding the entire route) – routing table for each host • Network-Specific Routing – instead of an entry for each host (on the same network), only one entry for the network is defined • Host-Specific Routing – for a sp ...
... • Next-Hop Routing – table only holds the address of the next hop (instead info regarding the entire route) – routing table for each host • Network-Specific Routing – instead of an entry for each host (on the same network), only one entry for the network is defined • Host-Specific Routing – for a sp ...
Traffic Measurement and Analysis of Wide Area
... data centres are consolidated to a central location, the WAN links almost become an extension of LAN and as a network is only as fast as its slowest link, it becomes essential to optimize the performance of a WAN link. So, understanding the current WAN link utilization may help us figure out the opt ...
... data centres are consolidated to a central location, the WAN links almost become an extension of LAN and as a network is only as fast as its slowest link, it becomes essential to optimize the performance of a WAN link. So, understanding the current WAN link utilization may help us figure out the opt ...
Classful IP Addresses
... • Convention for default gateway (but not a reserved address): – Default gateway has host number set to ‘1’, e.g., 128.100.0.1 ...
... • Convention for default gateway (but not a reserved address): – Default gateway has host number set to ‘1’, e.g., 128.100.0.1 ...
Chapter 13
... NSFNET attached to ARPANET via 1 core router Core had explicit routes to all destinations in NSFNET NSFNET routers knew about local destinations Had default route to non-NSFNET traffic via core ...
... NSFNET attached to ARPANET via 1 core router Core had explicit routes to all destinations in NSFNET NSFNET routers knew about local destinations Had default route to non-NSFNET traffic via core ...
Computers Are Your Future Twelfth Edition
... • Used by the public switched telephone network to send data over a physical end-to-end circuit • Provides a direct connection between devices o Packet switching • Used for computer communication • Divides and sends outgoing messages as packets, which are reassembled on receipt • More efficient and ...
... • Used by the public switched telephone network to send data over a physical end-to-end circuit • Provides a direct connection between devices o Packet switching • Used for computer communication • Divides and sends outgoing messages as packets, which are reassembled on receipt • More efficient and ...
Mobile VPNs For Next Generation GPRS And UMTS Networks
... Lucent’s GGSN implementation is based on the industry-leading SpringTide 7000 IP Service Switch platform. By incorporating the strengths of the existing wireline platform with newly designed wireless capabilities, the Lucent GGSN will enable wireless operators to provide business-quality IP services ...
... Lucent’s GGSN implementation is based on the industry-leading SpringTide 7000 IP Service Switch platform. By incorporating the strengths of the existing wireline platform with newly designed wireless capabilities, the Lucent GGSN will enable wireless operators to provide business-quality IP services ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.