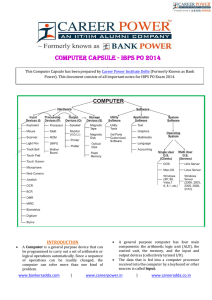
COMPUTER CAPSULE - IBPS PO 2014 . INTRODUCTION
... Read-only memory (ROM) is a storage medium used in computers and other electronic devices. Data stored in ROM can only be modified slowly or with difficulty, or not at all. ROM is non-volatile and the contents are retained even after the power is switched off. It only allows reading. The types of RO ...
... Read-only memory (ROM) is a storage medium used in computers and other electronic devices. Data stored in ROM can only be modified slowly or with difficulty, or not at all. ROM is non-volatile and the contents are retained even after the power is switched off. It only allows reading. The types of RO ...
KATARA Entry-Level Stackable Switch
... Typical Deployment At Edge Network • VRRP/VRRP-E on MCT cluster devices • Virtual IP as the default gateway on the ...
... Typical Deployment At Edge Network • VRRP/VRRP-E on MCT cluster devices • Virtual IP as the default gateway on the ...
Part I: Introduction
... Packet filtering relies on Network Layer and Transport Layer information contained in the headers of data packets to police traffic. This information includes source IP address and port number, destination IP address and port number, and protocol used (e.g., TCP, UDP, ICMP). This information is ...
... Packet filtering relies on Network Layer and Transport Layer information contained in the headers of data packets to police traffic. This information includes source IP address and port number, destination IP address and port number, and protocol used (e.g., TCP, UDP, ICMP). This information is ...
Network Management - Brock Computer Science
... Timeliness checking is done only if the authentication service is in use and the message is authentic, assuring the validity of the message header fields. ...
... Timeliness checking is done only if the authentication service is in use and the message is authentic, assuring the validity of the message header fields. ...
What is network management?
... Timeliness checking is done only if the authentication service is in use and the message is authentic, assuring the validity of the message header fields. ...
... Timeliness checking is done only if the authentication service is in use and the message is authentic, assuring the validity of the message header fields. ...
S7C9 - Multicasts
... • Supports dynamic membership of a multicast group • Supports all multicast groups regardless of location or number of members • Supports membership of single host in one or more groups • Upholds multiple data streams at application level for single group address • Supports single group address for ...
... • Supports dynamic membership of a multicast group • Supports all multicast groups regardless of location or number of members • Supports membership of single host in one or more groups • Upholds multiple data streams at application level for single group address • Supports single group address for ...
ppt - Carnegie Mellon School of Computer Science
... » Helps a lot: dropping useless cells reduces bandwidth and lowers the chance of later cell drops » Slight violation of layers » Discovered after early deployment experience with IP over ATM. ...
... » Helps a lot: dropping useless cells reduces bandwidth and lowers the chance of later cell drops » Slight violation of layers » Discovered after early deployment experience with IP over ATM. ...
layers
... • Network Interface layer – corresponds to OSI Data Link and Physical layers – concerned with protocols that access intermediate networks » each IP packet is encapsulated into an appropriate packet for whatever intermediate network requires » interfaces available for various specific network types - ...
... • Network Interface layer – corresponds to OSI Data Link and Physical layers – concerned with protocols that access intermediate networks » each IP packet is encapsulated into an appropriate packet for whatever intermediate network requires » interfaces available for various specific network types - ...
Computer Networks and the Internet
... multiplexing gains to be had, and by using circuits, each connection will get a constant amount of bandwidth that matches its CBR rate. On the other hand, circuit-switching has more overhead in terms of signaling needed to set up the call, so there is an argument that packet-switching is preferable ...
... multiplexing gains to be had, and by using circuits, each connection will get a constant amount of bandwidth that matches its CBR rate. On the other hand, circuit-switching has more overhead in terms of signaling needed to set up the call, so there is an argument that packet-switching is preferable ...
1 - KFUPM Faculty List
... when the WLAN is connected to the wireline networks, and all the real time traffic from the wireline networks are routed through the access point (the ``bridge'' between the WLAN and the wireline network) to the wireless part. When this happens, excess delay may be incurred at the heavily loaded AP ...
... when the WLAN is connected to the wireline networks, and all the real time traffic from the wireline networks are routed through the access point (the ``bridge'' between the WLAN and the wireline network) to the wireless part. When this happens, excess delay may be incurred at the heavily loaded AP ...
15-441: Networking Virtual Circuits, ATM, MPLS Peter Steenkiste Carnegie Mellon University
... Switching core is fairly simple, but Support for different traffic classes Signaling software is very complex Technology did not match people’s experience with IP – deploying ATM in LAN is complex (e.g. broadcast) – supporting connection-less service model on connection-based technology » With IP ov ...
... Switching core is fairly simple, but Support for different traffic classes Signaling software is very complex Technology did not match people’s experience with IP – deploying ATM in LAN is complex (e.g. broadcast) – supporting connection-less service model on connection-based technology » With IP ov ...
griffin-BGPConvTime
... BGP routing & reasons for long convergence time Some configurable options in BGP level routers Simulation network settings Analysis options vs. convergence time Summary ...
... BGP routing & reasons for long convergence time Some configurable options in BGP level routers Simulation network settings Analysis options vs. convergence time Summary ...
course-file-web
... How network devices contact each other and, if they have different languages, how they communicate with each other Methods by which a device on a network knows when to transmit data and when not to Methods to ensure that network transmissions are received correctly and by the right recipient ...
... How network devices contact each other and, if they have different languages, how they communicate with each other Methods by which a device on a network knows when to transmit data and when not to Methods to ensure that network transmissions are received correctly and by the right recipient ...
Ethernet - Mt. Hood Community College
... when the medium is clear, host sends signal to say it is about to use the medium. It then sends. ...
... when the medium is clear, host sends signal to say it is about to use the medium. It then sends. ...
Chapter 15
... If R1 loses connectivity, it must quit advertising After a few rounds of routing updates, all routers agree that the network is unreachable Does not prevent all routing loops ...
... If R1 loses connectivity, it must quit advertising After a few rounds of routing updates, all routers agree that the network is unreachable Does not prevent all routing loops ...
THE OPTIMIZATION OF STEPPING STONE DETECTION: PACKET CAPTURING STEPS MOHD NIZAM OMAR
... so forth while network-based IDS uses network packets as its main input [3]. IRS (Intrusion Response System) can be defined as IDS that detects an attack and immediately responds to remove the intruder from the network [4]. IDS and IRS are related. Both of these systems can use packet capturing prog ...
... so forth while network-based IDS uses network packets as its main input [3]. IRS (Intrusion Response System) can be defined as IDS that detects an attack and immediately responds to remove the intruder from the network [4]. IDS and IRS are related. Both of these systems can use packet capturing prog ...
ppt file - University of New Mexico
... reply to a request or, more frequently, an unsolicited regular routing update. In the response packet, a responding system includes all or part of its routing table. Regular routing update messages include the entire routing table. ...
... reply to a request or, more frequently, an unsolicited regular routing update. In the response packet, a responding system includes all or part of its routing table. Regular routing update messages include the entire routing table. ...
chapter_5_v6.011
... receiver identifies and corrects bit error(s) without resorting to retransmission ...
... receiver identifies and corrects bit error(s) without resorting to retransmission ...
Ch_22 - UCF EECS
... Assuming that this address is unique, the host sends a router solicitation message and receives the router advertisement message that announces the combination of global unicast prefix and the subnet identifier as 3A21:1216:2165:A245:1232. The host then appends its interface identifier to this prefi ...
... Assuming that this address is unique, the host sends a router solicitation message and receives the router advertisement message that announces the combination of global unicast prefix and the subnet identifier as 3A21:1216:2165:A245:1232. The host then appends its interface identifier to this prefi ...
excellence ethernet ba e 11780579a
... of METTLER TOLEDO Excellence balances into a TCP/IP-based network. Please read these installation and operating instructions right through before you start working with the Ethernet interface option, so you know how to operate the Ethernet interface safely and correctly and can make use of all its c ...
... of METTLER TOLEDO Excellence balances into a TCP/IP-based network. Please read these installation and operating instructions right through before you start working with the Ethernet interface option, so you know how to operate the Ethernet interface safely and correctly and can make use of all its c ...
вбг ¤ вбг ¤ ¥ £ ¤ ¥ time, which represents the зй !" $# . Such one
... adopted by such proposed routing protocols. It is becoming increasingly clear that such routing protocols are inadequate for multimedia application, such as video conferencing, which often require guaranteed QoS. QoS routing requires not only finding a route from a source to a destination, but a rou ...
... adopted by such proposed routing protocols. It is becoming increasingly clear that such routing protocols are inadequate for multimedia application, such as video conferencing, which often require guaranteed QoS. QoS routing requires not only finding a route from a source to a destination, but a rou ...
DNS and ARP
... • A knows B's IP address, wants to learn physical address of B • A broadcasts ARP query packet, containing B's IP address – all machines on LAN receive ARP query • B receives ARP packet, replies to A with its (B's) physical layer address • A caches (saves) IP-to-physical address pairs ...
... • A knows B's IP address, wants to learn physical address of B • A broadcasts ARP query packet, containing B's IP address – all machines on LAN receive ARP query • B receives ARP packet, replies to A with its (B's) physical layer address • A caches (saves) IP-to-physical address pairs ...
DNS & ARP
... • A knows B's IP address, wants to learn physical address of B • A broadcasts ARP query packet, containing B's IP address – all machines on LAN receive ARP query • B receives ARP packet, replies to A with its (B's) physical layer address • A caches (saves) IP-to-physical address pairs ...
... • A knows B's IP address, wants to learn physical address of B • A broadcasts ARP query packet, containing B's IP address – all machines on LAN receive ARP query • B receives ARP packet, replies to A with its (B's) physical layer address • A caches (saves) IP-to-physical address pairs ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.