PDF - International Journal of Recent Scientific Research
... wireless telecommunications networks It overcomes most of the geographical, temporal, organizational Barriers to data transfer and Salary To provide multimedia serviceseverywhere and Wireless applications and mobile technologies. Evolve Towards integration of heterogeneous access networks such and w ...
... wireless telecommunications networks It overcomes most of the geographical, temporal, organizational Barriers to data transfer and Salary To provide multimedia serviceseverywhere and Wireless applications and mobile technologies. Evolve Towards integration of heterogeneous access networks such and w ...
Chapter 12 Routing
... • Pairs of routers (BGP peers) exchange routing info over semipermanent TCP conctns: BGP sessions • Note that BGP sessions do not correspond to physical links. • When AS2 advertises a prefix to AS1, AS2 is promising it will forward any datagrams destined to that prefix towards the prefix. — AS2 can ...
... • Pairs of routers (BGP peers) exchange routing info over semipermanent TCP conctns: BGP sessions • Note that BGP sessions do not correspond to physical links. • When AS2 advertises a prefix to AS1, AS2 is promising it will forward any datagrams destined to that prefix towards the prefix. — AS2 can ...
Wireless Ad Hoc and Sensor Networks
... It can resist a variety of attacks, including black hole attack replay attack message forging attack message tampering attack DNS impersonation attack ...
... It can resist a variety of attacks, including black hole attack replay attack message forging attack message tampering attack DNS impersonation attack ...
ICMP and TCP - La Salle University
... Address Mask Request/Reply We discussed diskless workstation which do not know their IP address when they boot and use RARP to determine it. There is an ICMP packet used if a host does not know its subnet mask. ...
... Address Mask Request/Reply We discussed diskless workstation which do not know their IP address when they boot and use RARP to determine it. There is an ICMP packet used if a host does not know its subnet mask. ...
Part III Network Layer
... b. The last address can be found by ORing the given addresses with the complement of the mask. ORing here is done bit by bit. The result of ORing 2 bits is 0 if both bits are 0s; the result is 1 otherwise. The complement of a number is found by changing each 1 to 0 and each 0 to 1. ...
... b. The last address can be found by ORing the given addresses with the complement of the mask. ORing here is done bit by bit. The result of ORing 2 bits is 0 if both bits are 0s; the result is 1 otherwise. The complement of a number is found by changing each 1 to 0 and each 0 to 1. ...
Network Monitoring
... Performance indicators absolute prerequisite for the management of telecom network : measuring the performance of the network, or performance monitoring difficulties to choose appropriate indicators because of following: ...
... Performance indicators absolute prerequisite for the management of telecom network : measuring the performance of the network, or performance monitoring difficulties to choose appropriate indicators because of following: ...
Chapter 4 Multi-PON architecture 4.1 State-of-the-art
... packet at the head of the FIFO queue that cannot be transmitted to avoid collisions or contentions on the PON may prevent a successful transmission of another packet following in the FIFO order. To avoid this undesirable situations, the optimized queueing stage is composed by several queues, one per ...
... packet at the head of the FIFO queue that cannot be transmitted to avoid collisions or contentions on the PON may prevent a successful transmission of another packet following in the FIFO order. To avoid this undesirable situations, the optimized queueing stage is composed by several queues, one per ...
Characteristics of Communication Systems
... Non cable methods such as satelite, microwave, wireless and bluetooth Graham Betts ...
... Non cable methods such as satelite, microwave, wireless and bluetooth Graham Betts ...
Skype overview
... – “Global Index” technology that keeps track of which users have used the network in the near past – Skype claims, that any user who has logged in to the network in the last 72 hours can be found ...
... – “Global Index” technology that keeps track of which users have used the network in the near past – Skype claims, that any user who has logged in to the network in the last 72 hours can be found ...
access control list
... access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any How will the above access lists affect traffic? A. FTP traffic from 192.169.1.22 will be denied. B. No traffic, except for FTP traffic will be allowed to exit E0. C. FTP traffic from 192.169 ...
... access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any How will the above access lists affect traffic? A. FTP traffic from 192.169.1.22 will be denied. B. No traffic, except for FTP traffic will be allowed to exit E0. C. FTP traffic from 192.169 ...
CS244a: An Introduction to Computer Networks
... • call setup/teardown for each call before data can flow – need special control protocol: “signaling” – every router on source-dest path maintains “state” (VCI translation table) for each passing call – VCI translation table at routers along the path of a call “weaving together” a “logical connectio ...
... • call setup/teardown for each call before data can flow – need special control protocol: “signaling” – every router on source-dest path maintains “state” (VCI translation table) for each passing call – VCI translation table at routers along the path of a call “weaving together” a “logical connectio ...
MIND-SCOLD research collaboration
... a feasible automated solution to fix some of the problems. ...
... a feasible automated solution to fix some of the problems. ...
doc file - Prof. Paul Mc Kevitt
... modulation (PCM) is a common method of storing and transmitting uncompressed digital audio. Since it is a generic format, it can be read by most audio applications similar to the way a plain text file can be read by word-processing applications. Pulse code modulation (PCM) is used by Audio CDs and d ...
... modulation (PCM) is a common method of storing and transmitting uncompressed digital audio. Since it is a generic format, it can be read by most audio applications similar to the way a plain text file can be read by word-processing applications. Pulse code modulation (PCM) is used by Audio CDs and d ...
Mobile Node
... Each packet is then wrapped with IP header information. Status information is included and the packets are assembled into a list for processing. Finally, the NAT rules are added to the table. The benchmark then begins processing and rewriting the IP addresses and port numbers of packets based on the ...
... Each packet is then wrapped with IP header information. Status information is included and the packets are assembled into a list for processing. Finally, the NAT rules are added to the table. The benchmark then begins processing and rewriting the IP addresses and port numbers of packets based on the ...
Workware Wireless FAQ - AV/IT Installer
... The Workware Wireless Firmware is licensed software that is installed on the workware wireless module which is connected with a video cable to the display that you want to transform into a shared display. The Workware Wireless App is an application that runs on the devices you want to use to connect ...
... The Workware Wireless Firmware is licensed software that is installed on the workware wireless module which is connected with a video cable to the display that you want to transform into a shared display. The Workware Wireless App is an application that runs on the devices you want to use to connect ...
Adaptive Fairness through intra-ONU Scheduling for Ethernet
... of different ONUs transmitting simultaneously. Current MAC supports Time Division Multiplexing (TDM) [7], where each ONU is allocated a fixed or dynamic time slot to transmit data to the OLT and each ONU buffers packets received from different subscribers until they are transmitted in the assigned w ...
... of different ONUs transmitting simultaneously. Current MAC supports Time Division Multiplexing (TDM) [7], where each ONU is allocated a fixed or dynamic time slot to transmit data to the OLT and each ONU buffers packets received from different subscribers until they are transmitted in the assigned w ...
Document
... your Desktop from anywhere on your local network or over the Internet. The basic function of it is transmitting remote video on IP network. The high Quality video image can be transmitted with 30fps speed on the LAN/WAN by using MJPEG hardware compression technology. This is based on the TCP/IP stan ...
... your Desktop from anywhere on your local network or over the Internet. The basic function of it is transmitting remote video on IP network. The high Quality video image can be transmitted with 30fps speed on the LAN/WAN by using MJPEG hardware compression technology. This is based on the TCP/IP stan ...
IEEE802.11 Wireless LAN Standard
... for access to the same shared wireless medium. A BSS may be isolated or connected to a backbone distribution system (DS) through an access point (AP). The access point functions as a bridge. The BSS generally corresponds to what is referred to as a cell in the literature. The DS can be a switch, a w ...
... for access to the same shared wireless medium. A BSS may be isolated or connected to a backbone distribution system (DS) through an access point (AP). The access point functions as a bridge. The BSS generally corresponds to what is referred to as a cell in the literature. The DS can be a switch, a w ...
Name servers
... The simplest topology is a permanent link between two endpoints. Switched point-topoint topologies are the basic model of conventional telephony. The value of a permanent point-to-point network is unimpeded communications between the two endpoints. The value of an on-demand point-to-point connection ...
... The simplest topology is a permanent link between two endpoints. Switched point-topoint topologies are the basic model of conventional telephony. The value of a permanent point-to-point network is unimpeded communications between the two endpoints. The value of an on-demand point-to-point connection ...
WS - The ICT Help Center
... • Or, is an area on the hard disc of a computer where web pages and page elements (graphics etc) are stored when a page is downloaded from the Internet. If a page is revisited and the page, or elements of the page, are still held in cache then the computer will use the cache version to save time rat ...
... • Or, is an area on the hard disc of a computer where web pages and page elements (graphics etc) are stored when a page is downloaded from the Internet. If a page is revisited and the page, or elements of the page, are still held in cache then the computer will use the cache version to save time rat ...
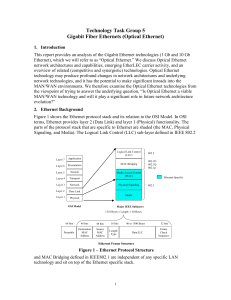
Gigabit Fiber Ethernets (Optical Ethernet)
... cuts. Various load-sharing techniques are used with priorities for different Class of Service (CoS) being indicated by the 3-bit user priority field in the VLAN tag. If insufficient capacity is provided to handle all of the traffic under failure conditions, the CoS indication can be used to allocate ...
... cuts. Various load-sharing techniques are used with priorities for different Class of Service (CoS) being indicated by the 3-bit user priority field in the VLAN tag. If insufficient capacity is provided to handle all of the traffic under failure conditions, the CoS indication can be used to allocate ...
Certification Exam Objectives: N10-005
... successful candidate will be able to configure, maintain, and troubleshoot network devices using appropriate network tools and understand the features and purpose of network technologies. Candidates will be able to make basic solution recommendations, analyze network traffic, and be familiar with co ...
... successful candidate will be able to configure, maintain, and troubleshoot network devices using appropriate network tools and understand the features and purpose of network technologies. Candidates will be able to make basic solution recommendations, analyze network traffic, and be familiar with co ...
Kerio WinRoute Firewall 6
... machine. Run the DHCP server and connect the machine to the network. An IP address from the formerly defined scope (see above) will be assigned to the printing machine. In the list of leased addresses, mark this IP address and click on Reserve.... This opens a dialog for IP address reservation with ...
... machine. Run the DHCP server and connect the machine to the network. An IP address from the formerly defined scope (see above) will be assigned to the printing machine. In the list of leased addresses, mark this IP address and click on Reserve.... This opens a dialog for IP address reservation with ...
Routing Protocols - Cisco Networking Academy
... destination because they use different metrics Ex: RIP chooses the path with the fewest number of hops, whereas EIGRP chooses the path based on the highest bandwidth and least delay. Metrics used in IP routing protocols include: Hop count - Number of routers a packet must traverse. Bandwidth - ...
... destination because they use different metrics Ex: RIP chooses the path with the fewest number of hops, whereas EIGRP chooses the path based on the highest bandwidth and least delay. Metrics used in IP routing protocols include: Hop count - Number of routers a packet must traverse. Bandwidth - ...
LevelOne
... This Wi-Fi detector also allows the user to go online wirelessly and is designed to comply with IEEE 802.11g Wireless LAN standard. It is suitable for any laptop or desktop computer. ...
... This Wi-Fi detector also allows the user to go online wirelessly and is designed to comply with IEEE 802.11g Wireless LAN standard. It is suitable for any laptop or desktop computer. ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.