Internet Technology Copyright Thanks
... You assume all responsibility for use and potential liability associated with any use of the material. Material contains copyrighted content, used in accordance with U.S. law. Copyright holders of content included in this material should contact [email protected] with any questions, correction ...
... You assume all responsibility for use and potential liability associated with any use of the material. Material contains copyrighted content, used in accordance with U.S. law. Copyright holders of content included in this material should contact [email protected] with any questions, correction ...
Overlay networks
... For the equivalent amount of multicast traffic, the sender needs much less processing power and bandwidth ...
... For the equivalent amount of multicast traffic, the sender needs much less processing power and bandwidth ...
CCNA2 3.1-07 Distance Vector Routing Protocols
... • Load balancing is a concept that allows a router to take advantage of multiple best paths to a given destination. • RIP is capable of load balancing over as many as six equalcost paths, with four paths being default. • RIP performs what is referred to as “round robin” load balancing. This means th ...
... • Load balancing is a concept that allows a router to take advantage of multiple best paths to a given destination. • RIP is capable of load balancing over as many as six equalcost paths, with four paths being default. • RIP performs what is referred to as “round robin” load balancing. This means th ...
How to Set Up Automatic Subnet Scan Using SolarWinds® IP Address Manager
... the ARP table of a neighbor router to determine which IP addresses are active. The Neighbor Scanning feature is disabled by default. When you un-check it, additional options appear where you can add the IP Address of the neighbor device and select a Scan Interval. ...
... the ARP table of a neighbor router to determine which IP addresses are active. The Neighbor Scanning feature is disabled by default. When you un-check it, additional options appear where you can add the IP Address of the neighbor device and select a Scan Interval. ...
Internet History and Architecture
... link layer sends datagram to 223.1.2.2 inside link-layer frame via interface 223.1.2.9 datagram arrives at 223.1.2.2 ...
... link layer sends datagram to 223.1.2.2 inside link-layer frame via interface 223.1.2.9 datagram arrives at 223.1.2.2 ...
Chapter 7
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
PPT Version
... • Two Sources – Performance Implications of Link Characteristics (PILC) – Layer-two triggers (L2triggers) Bar BoF at IETF 53 ...
... • Two Sources – Performance Implications of Link Characteristics (PILC) – Layer-two triggers (L2triggers) Bar BoF at IETF 53 ...
Implementing OpenLISP with LISP+ALT
... There have been several protocols suggested in the Routing Research Group that provide a locator id split; the Locator ID Separation Protocol [1] (LISP) is one of them. The locator ID Separation protocol is a mapping and encapsulation implementation of the locator id split. To realise a locator id s ...
... There have been several protocols suggested in the Routing Research Group that provide a locator id split; the Locator ID Separation Protocol [1] (LISP) is one of them. The locator ID Separation protocol is a mapping and encapsulation implementation of the locator id split. To realise a locator id s ...
Remote Access Techniques
... Network administrators can offer both modes of operation—remote node and remote control—to their users and let them decide which one is most appropriate to their needs and environments. For this there are hybrid remote access solutions that integrate remote control, remote node, and other communicat ...
... Network administrators can offer both modes of operation—remote node and remote control—to their users and let them decide which one is most appropriate to their needs and environments. For this there are hybrid remote access solutions that integrate remote control, remote node, and other communicat ...
VK2-3MPBIR3V9F User manual
... can be monitored on a real-time screen regardless of distances and locations. By using its dedicated program, many users are able to have an access to the Network Camera at once or a single user can monitor various network cameras at the same time. It also enables users to play, store and retrieve a ...
... can be monitored on a real-time screen regardless of distances and locations. By using its dedicated program, many users are able to have an access to the Network Camera at once or a single user can monitor various network cameras at the same time. It also enables users to play, store and retrieve a ...
Week_Eleven_ppt
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
Chapter_7_V6.0_HU
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
Hop-By-Hop Best Effort Link Layer Reliability in Named Data
... retransmission timers for loss detection and piggybacks acknowledgments on packets going the reverse direction. We evaluate BELRP performance through extensive simulations (Section IV), which show that BELRP can substantially improve application performance in high-loss network environments with ver ...
... retransmission timers for loss detection and piggybacks acknowledgments on packets going the reverse direction. We evaluate BELRP performance through extensive simulations (Section IV), which show that BELRP can substantially improve application performance in high-loss network environments with ver ...
ppt file
... It assigns private node addresses to IPC processes It internally maps app/service name to node address ...
... It assigns private node addresses to IPC processes It internally maps app/service name to node address ...
User-level Internet Path Diagnosis
... To understand how effective tulip is at pinpointing faults, we compared it with a promising alternative approach: network tomography that infers the location of faults by comparing observations on overlapping paths taken from multiple vantage points. While to our knowledge there are no widely availa ...
... To understand how effective tulip is at pinpointing faults, we compared it with a promising alternative approach: network tomography that infers the location of faults by comparing observations on overlapping paths taken from multiple vantage points. While to our knowledge there are no widely availa ...
Notes
... N = set of routers = { u, v, w, x, y, z } E = set of links ={ (u,v), (u,x), (v,x), (v,w), (x,w), (x,y), (w,y), (w,z), (y,z) } Remark: Graph abstraction is useful in other network contexts Example: P2P, where N is set of peers and E is set of TCP connections ...
... N = set of routers = { u, v, w, x, y, z } E = set of links ={ (u,v), (u,x), (v,x), (v,w), (x,w), (x,y), (w,y), (w,z), (y,z) } Remark: Graph abstraction is useful in other network contexts Example: P2P, where N is set of peers and E is set of TCP connections ...
Next Generation Convergence Network Testbed and
... • Motivation – To provide QoS guarantees for MPEG video streaming services with mobility support ...
... • Motivation – To provide QoS guarantees for MPEG video streaming services with mobility support ...
Chapter 25
... Unreliable transport (uses UDP) Broadcast or multicast delivery Distance vector algorithm Can propagate a default route Implemented by Unix program routed Passive version for hosts ...
... Unreliable transport (uses UDP) Broadcast or multicast delivery Distance vector algorithm Can propagate a default route Implemented by Unix program routed Passive version for hosts ...
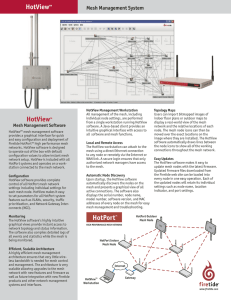
HotViewTM HotView™
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
Chapter 10 Systems Management
... sharing capabilities, and so on. Like the other two Registry components, System Policies consist of pairs of keys and values. Unlike the other two Registry components, System Policies are designed to override any settings that may exist in User Profiles or Hardware Profile. System Policies are not n ...
... sharing capabilities, and so on. Like the other two Registry components, System Policies consist of pairs of keys and values. Unlike the other two Registry components, System Policies are designed to override any settings that may exist in User Profiles or Hardware Profile. System Policies are not n ...
SpeedStream Router
... reverse engineer, disassemble or otherwise reduce the Software or any part thereof to a human perceivable form; modify, adapt, translate or create derivative works based upon the Software or any part thereof; or rent, lease, loan or otherwise operate for profit the Software. 3. Transfer. You may tra ...
... reverse engineer, disassemble or otherwise reduce the Software or any part thereof to a human perceivable form; modify, adapt, translate or create derivative works based upon the Software or any part thereof; or rent, lease, loan or otherwise operate for profit the Software. 3. Transfer. You may tra ...
Computer Networks and Internets
... Unreliable transport (uses UDP) Broadcast or multicast delivery Distance vector algorithm Can propagate a default route Implemented by Unix program routed Passive version for hosts ...
... Unreliable transport (uses UDP) Broadcast or multicast delivery Distance vector algorithm Can propagate a default route Implemented by Unix program routed Passive version for hosts ...
WLAN Site Surveys and Security Considerations
... Extension to existing Access Control system to make it more usable for large networks Access Control table does not reside in each Access Point but in a RADIUS server: – Server device that communicates with APs using RFC 2138 defined RADIUS protocol definition. (RADIUS = Remote Authentication Di ...
... Extension to existing Access Control system to make it more usable for large networks Access Control table does not reside in each Access Point but in a RADIUS server: – Server device that communicates with APs using RFC 2138 defined RADIUS protocol definition. (RADIUS = Remote Authentication Di ...
20050718-Abilene-Cotter
... • Committee of 8 individuals has been appointed to develop a merger strategy plan • Work to begin immediately ...
... • Committee of 8 individuals has been appointed to develop a merger strategy plan • Work to begin immediately ...
Applet - Personal.kent.edu
... Okay Fine, but how is digital service different from my analog service? Analog systems are less efficient than digital because analog systems need to convert digital data into the analog form phone lines use. Digital systems do not have to convert the information to analog and back, they simply arri ...
... Okay Fine, but how is digital service different from my analog service? Analog systems are less efficient than digital because analog systems need to convert digital data into the analog form phone lines use. Digital systems do not have to convert the information to analog and back, they simply arri ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.