iWork ’08 Quick Tour
... Code 1 is used only by the destination host to show that not all of the fragments have arrived within a set time. Whenever a router receives a datagram with a time-to-live value of zero, it discards the datagram and sends a time-exceeded message to the original source. When the final destination doe ...
... Code 1 is used only by the destination host to show that not all of the fragments have arrived within a set time. Whenever a router receives a datagram with a time-to-live value of zero, it discards the datagram and sends a time-exceeded message to the original source. When the final destination doe ...
Routing IP Datagrams - Computing Science
... Routing IP Datagrams – by Roozbeh Farahbod, [email protected] ...
... Routing IP Datagrams – by Roozbeh Farahbod, [email protected] ...
Ambient Networks – An Architecture for Communication Networks Beyond 3G
... This lack of a common control layer for joining the services – in a wide sense of the word – of multiple networks represents a crucial challenge both technically and from a user perspective. Usage scenarios that should be realizable in the mid-term future include utilization of multiple devices, mul ...
... This lack of a common control layer for joining the services – in a wide sense of the word – of multiple networks represents a crucial challenge both technically and from a user perspective. Usage scenarios that should be realizable in the mid-term future include utilization of multiple devices, mul ...
ppt
... • Another way is to define elementary fragment size that can pass through every network. • When packet fragmented, all pieces equal to elementary fragment size, except last one (may be smaller). • Packet may contain several fragments. ...
... • Another way is to define elementary fragment size that can pass through every network. • When packet fragmented, all pieces equal to elementary fragment size, except last one (may be smaller). • Packet may contain several fragments. ...
TCP/IP Networking Basics
... Large amounts of bandwidth can be provided easily and relatively inexpensively in a local area network (LAN). However, providing high bandwidth between a local network and the Internet can be very expensive. Because of this expense, Internet access is usually provided by a slower-speed wide-area net ...
... Large amounts of bandwidth can be provided easily and relatively inexpensively in a local area network (LAN). However, providing high bandwidth between a local network and the Internet can be very expensive. Because of this expense, Internet access is usually provided by a slower-speed wide-area net ...
SoNIC - Network and Systems Lab
... • SoNIC’s memory requirements are dominated by the need to store the decision tree in the sensor node’s RAM, which requires 1.8 KB • SoNIC uses 1 KB to store corrupted packets in the FIFO buffer for later matching • Furthermore, another static buffer of 128 bytes is used to store valid packets – so ...
... • SoNIC’s memory requirements are dominated by the need to store the decision tree in the sensor node’s RAM, which requires 1.8 KB • SoNIC uses 1 KB to store corrupted packets in the FIFO buffer for later matching • Furthermore, another static buffer of 128 bytes is used to store valid packets – so ...
TKN
... undergoes a threshold indicating that a HO should take place. A threshold-based handover has the disadvantage that it can affect other terminals since a HO decision is made when the lowest transmission rate cannot be used for error-free transmissions anymore. Transmissions at lower rate lead to incr ...
... undergoes a threshold indicating that a HO should take place. A threshold-based handover has the disadvantage that it can affect other terminals since a HO decision is made when the lowest transmission rate cannot be used for error-free transmissions anymore. Transmissions at lower rate lead to incr ...
A Platform for Unobtrusive Measurements on PlanetLab Rob Sherwood Neil Spring Abstract
... Figure 1: Sidecar is a platform for unobtrusive measurements that provides an event-driven interface and connecInternet measurement is key to optimizing performance, tion tracking to higher-level tools, e.g., artrat, sideping. building overlay topologies, developing improved transport protocols, und ...
... Figure 1: Sidecar is a platform for unobtrusive measurements that provides an event-driven interface and connecInternet measurement is key to optimizing performance, tion tracking to higher-level tools, e.g., artrat, sideping. building overlay topologies, developing improved transport protocols, und ...
Link State Routing Algorithm
... Link State Routing Algorithm • Use a routing protocol to collect the whole network topology • Obtain destination reachability information as well as link weights/states •Compute shortest paths using Dijkstra’s algorithm from a node to all other nodes •Construct routing tables that show the destinati ...
... Link State Routing Algorithm • Use a routing protocol to collect the whole network topology • Obtain destination reachability information as well as link weights/states •Compute shortest paths using Dijkstra’s algorithm from a node to all other nodes •Construct routing tables that show the destinati ...
ppt - Computer Science, Columbia University
... Not all RFCs become Internet Standards ! (There are >5000 RFCs and less than 70 Internet standards) A typical (but not only) way of standardization is: ...
... Not all RFCs become Internet Standards ! (There are >5000 RFCs and less than 70 Internet standards) A typical (but not only) way of standardization is: ...
Wireless Mesh Networks - BWN-Lab
... were connected to all other nodes, but most modern meshes connect only a sub-set of nodes to each other. Still, this is quite different than traditional wireless networks, which require centralized access points to mediate the wireless connection. Even two 802.11b nodes that are side-by-side in ...
... were connected to all other nodes, but most modern meshes connect only a sub-set of nodes to each other. Still, this is quite different than traditional wireless networks, which require centralized access points to mediate the wireless connection. Even two 802.11b nodes that are side-by-side in ...
ppt - UW Courses Web Server
... using forwarding table in input port memory (“match plus action”) goal: complete input port processing at ‘line speed’ queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-23 ...
... using forwarding table in input port memory (“match plus action”) goal: complete input port processing at ‘line speed’ queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-23 ...
Compatible Systems Reference Guides
... Generally, there are no required changes from the shipping Ethernet configuration for IPX. The Ethernet interface will autoconfigure to use the two most common IPX frame types, and will adapt to conditions on the Ethernet. Suggested for IPX ...
... Generally, there are no required changes from the shipping Ethernet configuration for IPX. The Ethernet interface will autoconfigure to use the two most common IPX frame types, and will adapt to conditions on the Ethernet. Suggested for IPX ...
CDD-564AEN, CDD-564ALEN CDD-562ALEN
... Vipersat Management System Integration A Vipersat powered network integrates these advanced demodulators with a powerful network management tool, the Vipersat Management System (VMS). In addition to the traditional Monitoring and Control of the CDM-570A/L-IPEN modems and the CDD564A/LEN and CDD-562A ...
... Vipersat Management System Integration A Vipersat powered network integrates these advanced demodulators with a powerful network management tool, the Vipersat Management System (VMS). In addition to the traditional Monitoring and Control of the CDM-570A/L-IPEN modems and the CDD564A/LEN and CDD-562A ...
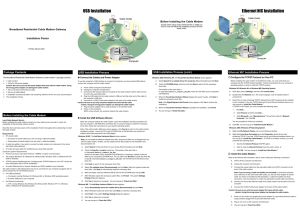
Ethernet NIC Installation USB Installation
... Caution: Be sure to use only the power adapter that came with the cable modem. Using the wrong power adapter can damage the cable modem. F. Plug the power adapter into a surge protector or an electrical outlet. G. Power on the computer. Within a few minutes, the computer detects the cable modem. ...
... Caution: Be sure to use only the power adapter that came with the cable modem. Using the wrong power adapter can damage the cable modem. F. Plug the power adapter into a surge protector or an electrical outlet. G. Power on the computer. Within a few minutes, the computer detects the cable modem. ...
Chapter_4
... using forwarding table in input port memory (“match plus action”) goal: complete input port processing at ‘line speed’ queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-23 ...
... using forwarding table in input port memory (“match plus action”) goal: complete input port processing at ‘line speed’ queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-23 ...
Network Layer
... using forwarding table in input port memory (“match plus action”) goal: complete input port processing at ‘line speed’ queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-23 ...
... using forwarding table in input port memory (“match plus action”) goal: complete input port processing at ‘line speed’ queuing: if datagrams arrive faster than forwarding rate into switch fabric Network Layer 4-23 ...