The Breadcrumb Router: Bundle Trajectory Tracking and Tomasz Kalbarczyk Brenton Walker
... these approaches into a geographically informed version of source routing. Previous approaches to geographic routing predominantly use a greedy approach in which locally optimal decisions are used to move a bundle incrementally closer to its destination. Our approach to geo-source routing differs in ...
... these approaches into a geographically informed version of source routing. Previous approaches to geographic routing predominantly use a greedy approach in which locally optimal decisions are used to move a bundle incrementally closer to its destination. Our approach to geo-source routing differs in ...
QFX10002 Fixed Ethernet Switches Product Description Data Sheet
... architectures, enabling data center operators to build cloud networks their way. • Layer 3 Fabric: For customers looking to build scale-out data centers, a Layer 3 spine and leaf Clos fabric is ideal due to its nonblocking and predictable performance and scale characteristics. For example, a two-ti ...
... architectures, enabling data center operators to build cloud networks their way. • Layer 3 Fabric: For customers looking to build scale-out data centers, a Layer 3 spine and leaf Clos fabric is ideal due to its nonblocking and predictable performance and scale characteristics. For example, a two-ti ...
firewalls - Faculty Personal Homepage
... Outbound connections terminate on the firewall. A set of policy rules defines how traffic from one network is transported to any other. If no rule exists, firewalls deny or drop the data packets. Policy rules are enforced through the use of proxies. Each protocol on a firewall must have its own prox ...
... Outbound connections terminate on the firewall. A set of policy rules defines how traffic from one network is transported to any other. If no rule exists, firewalls deny or drop the data packets. Policy rules are enforced through the use of proxies. Each protocol on a firewall must have its own prox ...
Distance vector routing updates
... Assume for the remainder of this example that Router C's preferred path to Network 1 is by way of Router B, and the distance from Router C to Network 1 is 3. When Network 1 fails, Router E sends an update to Router A. When Router A sends out its update, Routers B and D stop routing to Network 1. ...
... Assume for the remainder of this example that Router C's preferred path to Network 1 is by way of Router B, and the distance from Router C to Network 1 is 3. When Network 1 fails, Router E sends an update to Router A. When Router A sends out its update, Routers B and D stop routing to Network 1. ...
Towards the FAIR Timing System using White Rabbits
... upper bound latency from timing master to nodes no handshake: use UDP or raw Ethernet (no TCP) switches implement cut-through for high-priority messages ...
... upper bound latency from timing master to nodes no handshake: use UDP or raw Ethernet (no TCP) switches implement cut-through for high-priority messages ...
Slide 1
... • Tracert.exe, a variant of Ping, displays the path that packets take to their destination. • From a command prompt, type tracert target (where target is the IP address or the name [DNS or NetBIOS] of the target computer). • Use Tracert.exe to isolate the location of a network communications problem ...
... • Tracert.exe, a variant of Ping, displays the path that packets take to their destination. • From a command prompt, type tracert target (where target is the IP address or the name [DNS or NetBIOS] of the target computer). • Use Tracert.exe to isolate the location of a network communications problem ...
Group Comm
... Both the senders and receivers of CoAP group messages may be attached to different network links or be part of different LLNs, possibly with routers or switches in between group members In addition, different routing protocols may operate on the LLN and backbone networks. Preferably a solution also ...
... Both the senders and receivers of CoAP group messages may be attached to different network links or be part of different LLNs, possibly with routers or switches in between group members In addition, different routing protocols may operate on the LLN and backbone networks. Preferably a solution also ...
In recent years, a cost effective Wireless Mesh Networks ( WMNs
... address assigning. In association, nodes gradually joint the network starting in the root node of the tree. While in address assigning, nodes indicate the number of addresses they need built when the tree is complete, and finally all nodes have an ARTT. b) Operation: In operation phase, nodes start ...
... address assigning. In association, nodes gradually joint the network starting in the root node of the tree. While in address assigning, nodes indicate the number of addresses they need built when the tree is complete, and finally all nodes have an ARTT. b) Operation: In operation phase, nodes start ...
Split-TCP for Mobile Ad Hoc Networks
... Often, fixing one part of TCP breaks another part Competing interests exist in the standards laid out by OSI ...
... Often, fixing one part of TCP breaks another part Competing interests exist in the standards laid out by OSI ...
Multicast Routing Algos
... • All mobile platforms(nodes) are capable of motion • All the nodes have routing functionality. There is no need for centralized infrastructure for communication. • Each node is equipped with wireless transmitters / receivers • The node may be directly connected to a fixed network on a foreign subne ...
... • All mobile platforms(nodes) are capable of motion • All the nodes have routing functionality. There is no need for centralized infrastructure for communication. • Each node is equipped with wireless transmitters / receivers • The node may be directly connected to a fixed network on a foreign subne ...
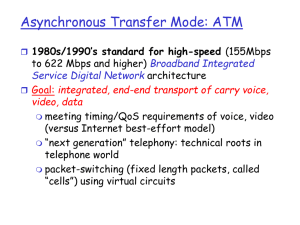
ATM
... Why?: small payload -> short cell-creation delay for digitized voice halfway between 32 and 64 (compromise!) ...
... Why?: small payload -> short cell-creation delay for digitized voice halfway between 32 and 64 (compromise!) ...
Document
... Example 3 Router R1 in Figure 6.8 receives a packet with destination address 167.24.160.5. Show how the packet is forwarded. Solution The destination address in binary is 10100111 00011000 10100000 00000101. A copy of the address is shifted 28 bits to the right. The result is 00000000 00000000 0000 ...
... Example 3 Router R1 in Figure 6.8 receives a packet with destination address 167.24.160.5. Show how the packet is forwarded. Solution The destination address in binary is 10100111 00011000 10100000 00000101. A copy of the address is shifted 28 bits to the right. The result is 00000000 00000000 0000 ...
APEXIA ADSL SETUP
... 8. After your computer has restarted, CLOSE ALL PROGRAMS. 9. In the Windows task bar, click on the Start button, highlight Settings and click on Control Panel. 10. Double-click the Network icon. 11. Click on the network component labeled TCP/IP for your NIC and then click on the Properties button. I ...
... 8. After your computer has restarted, CLOSE ALL PROGRAMS. 9. In the Windows task bar, click on the Start button, highlight Settings and click on Control Panel. 10. Double-click the Network icon. 11. Click on the network component labeled TCP/IP for your NIC and then click on the Properties button. I ...
Technical Guideline for the implementation of lawful measures for
... The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, like destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, durat ...
... The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, like destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, durat ...
Berkeley NOW - Computer Science Division
... • Vast majority of computing will be small, embedded, devices connected to the physical world – actually the case today, but – not connected to us, the web, or each other ...
... • Vast majority of computing will be small, embedded, devices connected to the physical world – actually the case today, but – not connected to us, the web, or each other ...
CCNA2 Module 6
... An analogy of distance vector could be the signs found at a highway intersection. A sign points towards a destination and indicates the distance to the destination. Further down the highway, another sign points toward the destination, but now the distance is shorter. As long as the distance is short ...
... An analogy of distance vector could be the signs found at a highway intersection. A sign points towards a destination and indicates the distance to the destination. Further down the highway, another sign points toward the destination, but now the distance is shorter. As long as the distance is short ...
"A Mesh based Robust Topology Discovery Algorithm for Hybrid Wireless Networks"
... 2.1. Communication System Wireless transmissions have much higher bit error rates than wireline transmissions. Current transport protocols, in particular, TCP/IP, are designed for wireline networks. They do not perform well if the frequency of dropped packets is too high. Hence, wireless technologie ...
... 2.1. Communication System Wireless transmissions have much higher bit error rates than wireline transmissions. Current transport protocols, in particular, TCP/IP, are designed for wireline networks. They do not perform well if the frequency of dropped packets is too high. Hence, wireless technologie ...
Lecture-9 on 10/22/2009 - Computer Science and Engineering
... Why is TCP fair? Two competing sessions: • Additive increase gives slope of 1, as throughout increases • multiplicative decrease decreases throughput proportionally R ...
... Why is TCP fair? Two competing sessions: • Additive increase gives slope of 1, as throughout increases • multiplicative decrease decreases throughput proportionally R ...
Cisco 1600 Series Router Architecture - weblearn.hs
... the free buffer is linked to the receive ring and the packet now belongs to the interface's private buffers pool. 3.2: A free buffer is not available in the interface's private pool, so the receive ring is replenished by falling back to the global pool that matches the interface's MTU. The fallback ...
... the free buffer is linked to the receive ring and the packet now belongs to the interface's private buffers pool. 3.2: A free buffer is not available in the interface's private pool, so the receive ring is replenished by falling back to the global pool that matches the interface's MTU. The fallback ...
PPT Format
... • This would indicate that the next group member who receives this message should become the group member. • If the next hop is a group member, it becomes the leader. • If not, it unicasts it to one of its next-hop neighbors. • Finally a group leader is selected. • Note now, that there are two leade ...
... • This would indicate that the next group member who receives this message should become the group member. • If the next hop is a group member, it becomes the leader. • If not, it unicasts it to one of its next-hop neighbors. • Finally a group leader is selected. • Note now, that there are two leade ...