present
... A massive modernization program encompassing observation, connectivity, supercomputing and forecasting facilities under an over-arching digital framework has been undertaken on priority basis in India. Under modernization program RTH New Delhi system will be replaced by a new system conforming to G ...
... A massive modernization program encompassing observation, connectivity, supercomputing and forecasting facilities under an over-arching digital framework has been undertaken on priority basis in India. Under modernization program RTH New Delhi system will be replaced by a new system conforming to G ...
CIS222 - Data Communications and Enterprise Networking
... Bluetooth causes interference to IEEE802.11b LANs, as they use the same frequency range. Gigabit Ethernets do not suffer from collisions as they always operate in full duplex mode. Fibre Channel uses 48-bit IEEE MAC addresses. A low growth product with a high market share is called a Star. ...
... Bluetooth causes interference to IEEE802.11b LANs, as they use the same frequency range. Gigabit Ethernets do not suffer from collisions as they always operate in full duplex mode. Fibre Channel uses 48-bit IEEE MAC addresses. A low growth product with a high market share is called a Star. ...
Document
... necessary wires itself. Private companies cannot install circuits across long distance. The necessary wiring can be obtained from a telephone company. Telephone companies allow companies to lease a circuit between any two locations. ...
... necessary wires itself. Private companies cannot install circuits across long distance. The necessary wiring can be obtained from a telephone company. Telephone companies allow companies to lease a circuit between any two locations. ...
Communication software and protocols
... Converts data into a format that can be Eg Convertion of my commands to the understood by the receiver’s system format that is compatible to florence’s system. Session layer eg setting up the linkage between my computer to my mail server to florence’s mail server to her device. ...
... Converts data into a format that can be Eg Convertion of my commands to the understood by the receiver’s system format that is compatible to florence’s system. Session layer eg setting up the linkage between my computer to my mail server to florence’s mail server to her device. ...
Week 10
... IP packet fragmentation details all fragments of the same packet carry the same identifier all fragments except the last one have the “MF” bit set fragment offset points to the first byte of the fragment ...
... IP packet fragmentation details all fragments of the same packet carry the same identifier all fragments except the last one have the “MF” bit set fragment offset points to the first byte of the fragment ...
Network Physics
... • Use predicting, interpolating, and reconciling later to improve game play. • When using prediction, transmit not just position information, but also velocity and acceleration. • Latch or queue user input (for example, keystrokes) until the next time communications data is to be sent. If you use th ...
... • Use predicting, interpolating, and reconciling later to improve game play. • When using prediction, transmit not just position information, but also velocity and acceleration. • Latch or queue user input (for example, keystrokes) until the next time communications data is to be sent. If you use th ...
Key Terms
... • Routing Information Protocol • The oldest routing protocol that is still widely used • RIP does not work in very large network environments where data may have to travel through more than 16 routers to reach its destination • Compared to other routing protocols, RIP is slower and less secure. ...
... • Routing Information Protocol • The oldest routing protocol that is still widely used • RIP does not work in very large network environments where data may have to travel through more than 16 routers to reach its destination • Compared to other routing protocols, RIP is slower and less secure. ...
Network Technologies PPT
... data. However, the public telephone system can also be used for data communications. • Standard phone lines transmit data much more slowly than network media, but devices such as modems make phone lines practical for data transmission over long ...
... data. However, the public telephone system can also be used for data communications. • Standard phone lines transmit data much more slowly than network media, but devices such as modems make phone lines practical for data transmission over long ...
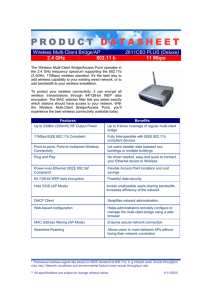
Wireless Multi-Client Bridge/AP 2611CB3 PLUS (Deluxe) 2.4 GHz
... the 2.4 GHz frequency spectrum supporting the 802.11b (2.4GHz, 11Mbps) wireless standard. It's the best way to add wireless capability to your existing wired network, or to add bandwidth to your wireless installation. To protect your wireless connectivity, it can encrypt all wireless transmissions t ...
... the 2.4 GHz frequency spectrum supporting the 802.11b (2.4GHz, 11Mbps) wireless standard. It's the best way to add wireless capability to your existing wired network, or to add bandwidth to your wireless installation. To protect your wireless connectivity, it can encrypt all wireless transmissions t ...
15. - 건국대학교
... audio/video playback, related to the variance of frame/packet delays (jitter) Sync skew: a measure of multimedia data synchronization. 건국대학교 인터넷미디어공학부 임창훈 ...
... audio/video playback, related to the variance of frame/packet delays (jitter) Sync skew: a measure of multimedia data synchronization. 건국대학교 인터넷미디어공학부 임창훈 ...
Grid agent data-flow execution
... in a clean, generic and portable way, and to also have access to a many data sources and data types which may not have been available to the native implementation on its own. Inter-agent communication is currently handled through RMI/CORBA, allowing for fast communications and data transfer. Adminis ...
... in a clean, generic and portable way, and to also have access to a many data sources and data types which may not have been available to the native implementation on its own. Inter-agent communication is currently handled through RMI/CORBA, allowing for fast communications and data transfer. Adminis ...
CMPT 880: Internet Architectures and Protocols
... • more users or faster transfer (a single user can use entire bw) • Well suited for bursty traffic (typical in data networks) ...
... • more users or faster transfer (a single user can use entire bw) • Well suited for bursty traffic (typical in data networks) ...
Tutorial - University of Hawaii
... • The IP address has a network part and a host part • A router must know where to forward packets destined for other networks • To do so, it runs a routing protocol: RIP, OSPF, BGP, etc • Manual configuration is also possible • Most hosts have a default route(r) ...
... • The IP address has a network part and a host part • A router must know where to forward packets destined for other networks • To do so, it runs a routing protocol: RIP, OSPF, BGP, etc • Manual configuration is also possible • Most hosts have a default route(r) ...
Mobile Media API - MobileEducationkit
... generation, audio and video playback. MMAPI requires limited resources, very less memory and processing capabilities. Its is not protocol or format specific, it supports most of the multimedia capable audio & video formats such as MP3 & WAV. It provides extensible & flexible framework, so new ...
... generation, audio and video playback. MMAPI requires limited resources, very less memory and processing capabilities. Its is not protocol or format specific, it supports most of the multimedia capable audio & video formats such as MP3 & WAV. It provides extensible & flexible framework, so new ...
Climate + Networks? - Understanding Climate Change: A Data
... network, n.: Any netlike or complex system or collection of interrelated things, as topographical features, lines of transportation, or telecommunications routes (esp. telephone lines). ...
... network, n.: Any netlike or complex system or collection of interrelated things, as topographical features, lines of transportation, or telecommunications routes (esp. telephone lines). ...
Poster
... Michael DeFrancis – Computer Engineering Shaheer Khan – Electrical Engineering Andrew Nosal – Electrical Engineering Demetrios Koukouves – Mechanical Engineering ...
... Michael DeFrancis – Computer Engineering Shaheer Khan – Electrical Engineering Andrew Nosal – Electrical Engineering Demetrios Koukouves – Mechanical Engineering ...
Prezentacja programu PowerPoint
... Monitoring the battery voltage The first and most basic functionality of the STARK system is to monitor the car battery voltage. Unfortunately, the few existing microcontrollers are based on 12V logic, while the most popular solutions work in 5V logic, commonly used in many ATMega controllers or 3 ...
... Monitoring the battery voltage The first and most basic functionality of the STARK system is to monitor the car battery voltage. Unfortunately, the few existing microcontrollers are based on 12V logic, while the most popular solutions work in 5V logic, commonly used in many ATMega controllers or 3 ...
CMPT 880: Internet Architectures and Protocols
... • more users or faster transfer (a single user can use entire bw) • Well suited for bursty traffic (typical in data networks) ...
... • more users or faster transfer (a single user can use entire bw) • Well suited for bursty traffic (typical in data networks) ...
Computer Systems and Networks
... point-to-point links in a ring As data circulates past a receiver, the receiver checks its address, and copies those intended for it into a local buffer Data circulates until it returns to source, which removes it from network Better performance at high levels of usage ...
... point-to-point links in a ring As data circulates past a receiver, the receiver checks its address, and copies those intended for it into a local buffer Data circulates until it returns to source, which removes it from network Better performance at high levels of usage ...
Part I: Introduction
... 18 /* shortest path from V to some Y has changed */ 19 /* V has sent a new value for its min DV(Y,w) */ ...
... 18 /* shortest path from V to some Y has changed */ 19 /* V has sent a new value for its min DV(Y,w) */ ...
cs2302 computer networks
... It ensures that the whole message arrives in order and intact. It ensures the error control and flow control at source to destination level. The responsibilities are, 1. Service point Addressing A single computer can often run several programs at the same time. The transport layer gets the e ...
... It ensures that the whole message arrives in order and intact. It ensures the error control and flow control at source to destination level. The responsibilities are, 1. Service point Addressing A single computer can often run several programs at the same time. The transport layer gets the e ...