8 bits
... compatible with those specified for the IPv4 protocol field For each router that forwards the packet, the hop limit is decremented by 1. When the hop limit field reaches zero, the packet is discarded. This replaces the TTL field in the IPv4 header that was originally intended to be used as a time ba ...
... compatible with those specified for the IPv4 protocol field For each router that forwards the packet, the hop limit is decremented by 1. When the hop limit field reaches zero, the packet is discarded. This replaces the TTL field in the IPv4 header that was originally intended to be used as a time ba ...
WLAN - GVSU School of Computing an Information Systems
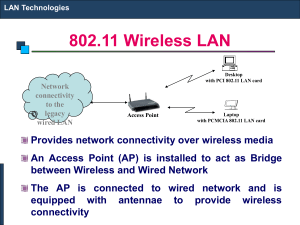
... – Each client sends its data to an access point – The access points acts as a bridge and forwards the packets to other clients or to the wired ...
... – Each client sends its data to an access point – The access points acts as a bridge and forwards the packets to other clients or to the wired ...
project1\lastmile.doc
... demultiplexing and switching functions mean that all the signals optical link. from all the users' diverse computing and communications equipment must be converted into a common format. This signal format conversion is accomplished by a device called a network termination unit. Although data can be ...
... demultiplexing and switching functions mean that all the signals optical link. from all the users' diverse computing and communications equipment must be converted into a common format. This signal format conversion is accomplished by a device called a network termination unit. Although data can be ...
Chapter 6 slides, Computer Networking, 3rd edition
... (MSs) are supported by a single base station (BS) Forward link (downlink): BS → multiples MSs (one to many broadcasting) Reverse link (uplink): MSs →BS (many to one multiple access) ...
... (MSs) are supported by a single base station (BS) Forward link (downlink): BS → multiples MSs (one to many broadcasting) Reverse link (uplink): MSs →BS (many to one multiple access) ...
Sample Solution for Exercise Communication Networks I
... b) For data transmission a three-tier signal is used to transmit the values 0, 1, and 2. Per second 2000 signal alternations can be realized. I) How high is the bit rate? II) How high is the baud rate? Solution: I) bit rate: number of bits per time interval: ld (number of signal tiers) ...
... b) For data transmission a three-tier signal is used to transmit the values 0, 1, and 2. Per second 2000 signal alternations can be realized. I) How high is the bit rate? II) How high is the baud rate? Solution: I) bit rate: number of bits per time interval: ld (number of signal tiers) ...
computer network - model test paper
... 3. Adding or removing computers will also affect the whole network since every computer is connected with previous and next computer. 4. Sending a message from one computer to another takes time according to the number of nodes between the two computers. Communication delay is directly proportional ...
... 3. Adding or removing computers will also affect the whole network since every computer is connected with previous and next computer. 4. Sending a message from one computer to another takes time according to the number of nodes between the two computers. Communication delay is directly proportional ...
ppt - The Fengs
... protocols • When and why should this be used? Rarely done over twisted-pair or fiber optic links ●Usually done over lossy links for performance improvement (versus correctness) ...
... protocols • When and why should this be used? Rarely done over twisted-pair or fiber optic links ●Usually done over lossy links for performance improvement (versus correctness) ...
A6_Oct_07_08 - Raadio- ja sidetehnika instituut
... • It is an inter layer network process • NwE process in each layer network – advertises the nodes and their ports within the layer network – monitors the layer network and determines if/when a new (topological) link should be added or an existing link should be modified or released, based on the net ...
... • It is an inter layer network process • NwE process in each layer network – advertises the nodes and their ports within the layer network – monitors the layer network and determines if/when a new (topological) link should be added or an existing link should be modified or released, based on the net ...
Chapter 6 – Connectivity Devices
... • Multiport device that connects dissimilar LANs that use different transmission speeds and a variety of protocols • Operate at the Network Layer (Layer 3) • Slower than switches or bridges because routers use information from Layer 3 such as protocols and logical addresses • Routers are protocol de ...
... • Multiport device that connects dissimilar LANs that use different transmission speeds and a variety of protocols • Operate at the Network Layer (Layer 3) • Slower than switches or bridges because routers use information from Layer 3 such as protocols and logical addresses • Routers are protocol de ...
Introduction
... • Typically the listed issues are handled by 2 protocols – A Physical Layer (PL), which deals with bit Encoding/Decoding • Physical Layer at A deals with the following problem: – Given a sequence of bits (bits making up a packet), how do you encode the bits onto the link as signals (electromagnetic, ...
... • Typically the listed issues are handled by 2 protocols – A Physical Layer (PL), which deals with bit Encoding/Decoding • Physical Layer at A deals with the following problem: – Given a sequence of bits (bits making up a packet), how do you encode the bits onto the link as signals (electromagnetic, ...
Networks_10
... packet sent by the sender CTS: Clear to send – packet sent by the intended recipient that alerts all other nodes to be ‘quiet’ ...
... packet sent by the sender CTS: Clear to send – packet sent by the intended recipient that alerts all other nodes to be ‘quiet’ ...
Introduction - Department of Computer Engineering
... • Typically the listed issues are handled by 2 protocols – A Physical Layer (PL), which deals with bit Encoding/Decoding • Physical Layer at A deals with the following problem: – Given a sequence of bits (bits making up a packet), how do you encode the bits onto the link as signals (electromagnetic, ...
... • Typically the listed issues are handled by 2 protocols – A Physical Layer (PL), which deals with bit Encoding/Decoding • Physical Layer at A deals with the following problem: – Given a sequence of bits (bits making up a packet), how do you encode the bits onto the link as signals (electromagnetic, ...
NET for stjosephs
... receiver in an unbroken path. Once connection is established and a dedicated path exists between both ends Advantages: No blocking No channel access delay Disadvantages : Inefficient use of channels (when connection device are not using) and More expensive ...
... receiver in an unbroken path. Once connection is established and a dedicated path exists between both ends Advantages: No blocking No channel access delay Disadvantages : Inefficient use of channels (when connection device are not using) and More expensive ...
Ch 2: Networking Standards and the OSI Model
... 2003: ICANN sued Verisign to make them shut down their "Site Finder" service, which captured all mistyped URLs and showed them Verisign ads 2004 Verisign sued ICANN saying they had overstepped their authority 2008 Ten worst spam offenders notified by ICANN Links Ch 2a, 2b, 2c The OSI Model Model f ...
... 2003: ICANN sued Verisign to make them shut down their "Site Finder" service, which captured all mistyped URLs and showed them Verisign ads 2004 Verisign sued ICANN saying they had overstepped their authority 2008 Ten worst spam offenders notified by ICANN Links Ch 2a, 2b, 2c The OSI Model Model f ...
Networks Adrian Janson
... packet sent by the sender CTS: Clear to send – packet sent by the intended recipient that alerts all other nodes to be ‘quiet’ ...
... packet sent by the sender CTS: Clear to send – packet sent by the intended recipient that alerts all other nodes to be ‘quiet’ ...
Wireless Network
... When a message is broken into packets, control information is added to each packet to provide source/ destination information and identification. ...
... When a message is broken into packets, control information is added to each packet to provide source/ destination information and identification. ...
Document
... Require active probing for probing idle links Blind to underlying retransmission at MAC ...
... Require active probing for probing idle links Blind to underlying retransmission at MAC ...
No Slide Title
... • iBGP when used as IGP • carries global routes around network • injected with eircom customer routes ...
... • iBGP when used as IGP • carries global routes around network • injected with eircom customer routes ...
$doc.title
... Why No Math in This Course? • Hypothesis #1: theory not relevant to Internet – Body of math created for telephone networks – Many of these models don’t work in data networks ...
... Why No Math in This Course? • Hypothesis #1: theory not relevant to Internet – Body of math created for telephone networks – Many of these models don’t work in data networks ...
Document
... Protocol layering and data Each layer takes data from above adds header information to create new data unit passes new data unit to layer below source ...
... Protocol layering and data Each layer takes data from above adds header information to create new data unit passes new data unit to layer below source ...