Introduction - School of Engineering
... is essential as it dictates how each computer on the Internet (i.e. corporate LAN, home computer etc.) must behave in order to facilitate data transfer. Without it, Internet computers could (and most probably would) have incompatible network architectures. The topmost layers are the most abstract, e ...
... is essential as it dictates how each computer on the Internet (i.e. corporate LAN, home computer etc.) must behave in order to facilitate data transfer. Without it, Internet computers could (and most probably would) have incompatible network architectures. The topmost layers are the most abstract, e ...
Presentation (ppt)
... – This would make data and services equal to hosts • It would also accommodate mobility and multihoming • And properly integrate middleboxes into the Internet Information-Centric Networks ...
... – This would make data and services equal to hosts • It would also accommodate mobility and multihoming • And properly integrate middleboxes into the Internet Information-Centric Networks ...
Other Link Layer Protocols and Technologies
... – Upon possession, a sending station changes one bit in token to make it SOF for data frame – Appends rest of data frame to the token – Frame makes round trip, reaches destination and is finally absorbed by transmitting station • sending station can perform some checks to see if frame was received c ...
... – Upon possession, a sending station changes one bit in token to make it SOF for data frame – Appends rest of data frame to the token – Frame makes round trip, reaches destination and is finally absorbed by transmitting station • sending station can perform some checks to see if frame was received c ...
Internet Model
... If the called telephone is attached to another end office, a different procedure has to be used. Each end office (local switch) has a number of outgoing lines to one or more nearby switching centers, called toll offices (or if they are within the same local area, tandem switches). These lines are ca ...
... If the called telephone is attached to another end office, a different procedure has to be used. Each end office (local switch) has a number of outgoing lines to one or more nearby switching centers, called toll offices (or if they are within the same local area, tandem switches). These lines are ca ...
A crash course in networking
... • Reed's law: the utility of large networks, particularly social networks, can scale exponentially with the size of the network. – The number of possible sub-groups of network participants is 2N-N-1 , where N is the number of participants. This grows much more rapidly than either • the number of par ...
... • Reed's law: the utility of large networks, particularly social networks, can scale exponentially with the size of the network. – The number of possible sub-groups of network participants is 2N-N-1 , where N is the number of participants. This grows much more rapidly than either • the number of par ...
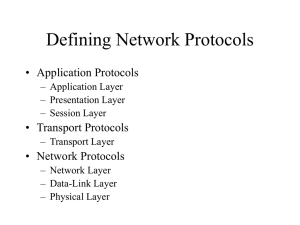
Defining Network Protocols
... • For small Microsoft networks • Sends a lot of data on the network wire ...
... • For small Microsoft networks • Sends a lot of data on the network wire ...
Chapter 4. Data Link Layer
... – Designed to transmit error-free data – Group data into blocks to be transmitted (rather sending character by character) ...
... – Designed to transmit error-free data – Group data into blocks to be transmitted (rather sending character by character) ...
Enterprise Wireless LAN (WLAN) Management
... Authentication problems (802.1x protocol issues) ...
... Authentication problems (802.1x protocol issues) ...
Addressing - Punjab University College of Information
... IEEE as G/L bit IEEE sets G/L = 0 when giving out the blocks of addresses Addresses with G/L = 1 can be used without paying IEEE but the network administrator is responsible to assign addresses such that there is no collision This leaves with 222 unique OUIs ...
... IEEE as G/L bit IEEE sets G/L = 0 when giving out the blocks of addresses Addresses with G/L = 1 can be used without paying IEEE but the network administrator is responsible to assign addresses such that there is no collision This leaves with 222 unique OUIs ...
peripherals
... • Information in computers is stored using the binary number system, in which the only possible symbols, or binary digits, 0 or 1. ...
... • Information in computers is stored using the binary number system, in which the only possible symbols, or binary digits, 0 or 1. ...
Nortel Networks Cable Media Solutions
... aggregation for over 32,000 subscribers within a single platform, with sophisticated provisioning and high-touch subscriber services, while the Passport 8600 provides the routing and switching capabilities, differentiated services, and Quality of Service (QoS). Core Backbone: Today, 75% of all the N ...
... aggregation for over 32,000 subscribers within a single platform, with sophisticated provisioning and high-touch subscriber services, while the Passport 8600 provides the routing and switching capabilities, differentiated services, and Quality of Service (QoS). Core Backbone: Today, 75% of all the N ...
(IPC) to communicate with other applications?
... Interprocess Communication (IPC) is the mechanism that facilitates communications and data sharing between applications. It enables one application to control another and multiple applications to share the same data without interfering with one another. IPC utilizes a set of programming interfaces, ...
... Interprocess Communication (IPC) is the mechanism that facilitates communications and data sharing between applications. It enables one application to control another and multiple applications to share the same data without interfering with one another. IPC utilizes a set of programming interfaces, ...
Exam - LIACS - Universiteit Leiden
... support requests in a timely manner. Support requests are initially received by a “first line” team through either an e-mail or a telephone call. This team then either addresses the support call directly or assigns it to a “second line” employee who will then address the problem at a later point in ...
... support requests in a timely manner. Support requests are initially received by a “first line” team through either an e-mail or a telephone call. This team then either addresses the support call directly or assigns it to a “second line” employee who will then address the problem at a later point in ...
Lecture 20: Transport layer
... – A clock runs continuously, use the lower k-bit as the ISN. – Host A port 10 talk to host B port 12, 8 bits sequence number, increments every 1 sec. Consider this situation: » A starts at time 100, choose ISN 100, sends 150 packets crashed. » A reboots at time 200 and, use local port 10 and connect ...
... – A clock runs continuously, use the lower k-bit as the ISN. – Host A port 10 talk to host B port 12, 8 bits sequence number, increments every 1 sec. Consider this situation: » A starts at time 100, choose ISN 100, sends 150 packets crashed. » A reboots at time 200 and, use local port 10 and connect ...
CSCI6268L10 - Computer Science
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
Introduction to computer communication networks
... typically implemented in hardware or firmware when you buy a network card, you get both physical and data link layer protocols in the card ...
... typically implemented in hardware or firmware when you buy a network card, you get both physical and data link layer protocols in the card ...
for Semester 1 Chapter 4
... – Insertion loss is measured in decibels at the far end of the cable. – The TIA/EIA standard requires that a cable and its connectors pass an insertion loss test before the cable can be used as a communications link in a ...
... – Insertion loss is measured in decibels at the far end of the cable. – The TIA/EIA standard requires that a cable and its connectors pass an insertion loss test before the cable can be used as a communications link in a ...
Network on Chip - Architectures and Design Methodology
... • Global control of information traffic is unlikely to ...
... • Global control of information traffic is unlikely to ...