Networking Overview
... Reserved --- reserved for future use (or for clever attackers…) Window --- controls number of outstanding packets; prevents one side from sending too fast (flow control) Checksum --- error detection (uses CRC) ...
... Reserved --- reserved for future use (or for clever attackers…) Window --- controls number of outstanding packets; prevents one side from sending too fast (flow control) Checksum --- error detection (uses CRC) ...
Link Layer Topology Discovery in an Uncooperative Ethernet Environment by Johannes Petrus Delport
... a network’s physical topology, can be useful in a variety of network scenarios and applications. Administrators can use topology information for faultfinding, inventorying and network planning. Topology information can also be used during protocol and routing algorithm development, for performance p ...
... a network’s physical topology, can be useful in a variety of network scenarios and applications. Administrators can use topology information for faultfinding, inventorying and network planning. Topology information can also be used during protocol and routing algorithm development, for performance p ...
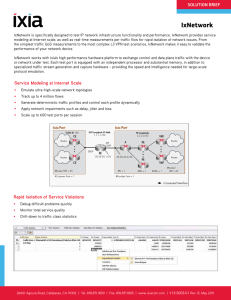
IxNetwork
... modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most complex L3 VPN test scenarios, IxNetwork makes it easy to validate the performance of your network device. IxNetwork works with ...
... modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most complex L3 VPN test scenarios, IxNetwork makes it easy to validate the performance of your network device. IxNetwork works with ...
Emulation of RDRN on an ATM-Testbed and a Comparative
... IP over ATM specification says that the MTU cannot be larger than 9180 bytes; hence the CLIP can pass a packet of the above size to the “glue_layer”. Hence, when the DLC layer would attach its own header and trailer, it would cause an overflow on the ENI card. In the above case the segmentation ...
... IP over ATM specification says that the MTU cannot be larger than 9180 bytes; hence the CLIP can pass a packet of the above size to the “glue_layer”. Hence, when the DLC layer would attach its own header and trailer, it would cause an overflow on the ENI card. In the above case the segmentation ...
PPTX - gozips.uakron.edu
... adaptor connected to that Ethernet. • Each adaptor recognizes those frames addressed to its address and passes only those frames on to the host. • In addition, to unicast address, an Ethernet address consisting of all 1s is treated as a broadcast address. – All adaptors pass frames addressed to the ...
... adaptor connected to that Ethernet. • Each adaptor recognizes those frames addressed to its address and passes only those frames on to the host. • In addition, to unicast address, an Ethernet address consisting of all 1s is treated as a broadcast address. – All adaptors pass frames addressed to the ...
EIGRP and OSPF Comparison
... up) constrains the number of neighbors that a router can support and the number of neighbors that can be in an area. When the network is stable, link-state protocols minimize bandwidth usage by sending updates only when a change occurs. A hello mechanism ascertains reachability of neighbors. When a ...
... up) constrains the number of neighbors that a router can support and the number of neighbors that can be in an area. When the network is stable, link-state protocols minimize bandwidth usage by sending updates only when a change occurs. A hello mechanism ascertains reachability of neighbors. When a ...
Chapter 7 outline
... delay loss: IP datagram arrives too late for playout at receiver delays: processing, queueing in network; endsystem (sender, receiver) delays typical maximum tolerable delay: 400 ms loss tolerance: depending on voice encoding, losses concealed, packet loss rates between 1% and 10% can be tol ...
... delay loss: IP datagram arrives too late for playout at receiver delays: processing, queueing in network; endsystem (sender, receiver) delays typical maximum tolerable delay: 400 ms loss tolerance: depending on voice encoding, losses concealed, packet loss rates between 1% and 10% can be tol ...
Document
... otherwise, query “rendezvous point” in S4(x) and build the level-4 routing entry to reach nodes in B5(x) E.g. Node A: B5(A)={E,F,G,H,J,K,L}; A queries “rendezvous point” in S4(A), say, D; learns B as ...
... otherwise, query “rendezvous point” in S4(x) and build the level-4 routing entry to reach nodes in B5(x) E.g. Node A: B5(A)={E,F,G,H,J,K,L}; A queries “rendezvous point” in S4(A), say, D; learns B as ...
IP Multicast
... • Between a host on a subnet (Ethernet) and the router for the subnet. • The router periodically broadcast an IGMP host-membership query message on its subnet. • A host subscribes to a group replies by multicasting a hostmembership report message. – Note: feedback implosion uses a random timer. ...
... • Between a host on a subnet (Ethernet) and the router for the subnet. • The router periodically broadcast an IGMP host-membership query message on its subnet. • A host subscribes to a group replies by multicasting a hostmembership report message. – Note: feedback implosion uses a random timer. ...
“The Tenet Architecture for Tiered Sensor Networks.”
... sensor network will be small; wireless loss rates being what they are, large diameter sensor networks will be inefficient. The third cost is that in-mote fusion can reduce congestion inside the network. For instance, in pursuit-evasion, leader election within a one-hop neighborhood results in a sing ...
... sensor network will be small; wireless loss rates being what they are, large diameter sensor networks will be inefficient. The third cost is that in-mote fusion can reduce congestion inside the network. For instance, in pursuit-evasion, leader election within a one-hop neighborhood results in a sing ...
13 Signaling Protocols for Multimedia Communication
... – Client searches for Super Nodes and connects to a Super Node – Client gets address of communication partner from Super Node and establishes direct (peer-to-peer) communication link – Voice transmission: via UDP, adaptive between 24 and 128 kbit/s » Predictive codecs: iSAC (LPC based), SILK (hybrid ...
... – Client searches for Super Nodes and connects to a Super Node – Client gets address of communication partner from Super Node and establishes direct (peer-to-peer) communication link – Voice transmission: via UDP, adaptive between 24 and 128 kbit/s » Predictive codecs: iSAC (LPC based), SILK (hybrid ...
x510 Series Datasheet
... EPSRing support and VCStack LD (Long Distance), which enables stacks to be created over long distance fiber links, make the x510 Series the perfect choice for distributed environments. Reliable The x510 Series was designed with reliability in mind, and guarantees continual delivery of essential serv ...
... EPSRing support and VCStack LD (Long Distance), which enables stacks to be created over long distance fiber links, make the x510 Series the perfect choice for distributed environments. Reliable The x510 Series was designed with reliability in mind, and guarantees continual delivery of essential serv ...
Protocol Analysis
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
TR-M2M-0009v0.7.0 oneM2M Protocol Analysis
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
GMPLS-based provisioning of Ethernet connections over WSON with Quality of Service Ph.D. Thesis
... framework of GMPLS unified control plane. Firstly, we propose the usage of a FA TE link timer, which postpones the release of created FA TE link when there are no more upper-layer connections over such a link, rather than releasing it immediately. By doing so, we do reduce the signaling overhead due ...
... framework of GMPLS unified control plane. Firstly, we propose the usage of a FA TE link timer, which postpones the release of created FA TE link when there are no more upper-layer connections over such a link, rather than releasing it immediately. By doing so, we do reduce the signaling overhead due ...
lecture10 - Academic Server| Cleveland State University
... – When it realizes that there is no application that is waiting on the port, it will generate an ICMP packet of destination unreachable to the forged source address – If enough UDP packets are delivered to ports on victim, the system will go down Spring 2007 ...
... – When it realizes that there is no application that is waiting on the port, it will generate an ICMP packet of destination unreachable to the forged source address – If enough UDP packets are delivered to ports on victim, the system will go down Spring 2007 ...
The multimedia broadcast/multicast service
... options are the use of CBS, SMS or web page listings. In all cases, the Session Description Protocol (SDP) is used to describe the contents of a session, such as media types and bandwidth requirements. Users may choose to either activate or deactivate reception for each broadcast service locally, th ...
... options are the use of CBS, SMS or web page listings. In all cases, the Session Description Protocol (SDP) is used to describe the contents of a session, such as media types and bandwidth requirements. Users may choose to either activate or deactivate reception for each broadcast service locally, th ...
Ch. 3
... debug serial interface – Verifies whether HDLC keepalive packets are incrementing. If they are not, a possible timing problem exists on the interface card or in the network. • debug arp – Indicates whether the router is sending information about or learning about routers (with ARP packets) on the ot ...
... debug serial interface – Verifies whether HDLC keepalive packets are incrementing. If they are not, a possible timing problem exists on the interface card or in the network. • debug arp – Indicates whether the router is sending information about or learning about routers (with ARP packets) on the ot ...
TinyOS – A Skeleton OS for Networks of Embedded Systems
... nesC much nicer to use than TinyOS: ...
... nesC much nicer to use than TinyOS: ...