DYNAMIC BUFFER ALLOCATION FOR TIME CRITICAL DATA IN
... Delay caused by the Link failure is minimized using the buffers allocated for the intermediate node these two schemes. Basically there are two problems in case of link failure (a) Packet loss: Each and every node carrying critical data is assigned a buffer that holds the data that is dropped. Packet ...
... Delay caused by the Link failure is minimized using the buffers allocated for the intermediate node these two schemes. Basically there are two problems in case of link failure (a) Packet loss: Each and every node carrying critical data is assigned a buffer that holds the data that is dropped. Packet ...
for TCP
... • Premise: Network is unreliable – Consequence: Sender must buffer all TPDUs sent – May need to retransmit • Receiver needs to buffer – Out of order TPDUs – Flow control to application(s) (maximize tranmission speed) • Sender TP layer also buffers to even flow from its application(s) (smooth out bur ...
... • Premise: Network is unreliable – Consequence: Sender must buffer all TPDUs sent – May need to retransmit • Receiver needs to buffer – Out of order TPDUs – Flow control to application(s) (maximize tranmission speed) • Sender TP layer also buffers to even flow from its application(s) (smooth out bur ...
Application Layer Functionality and Protocols
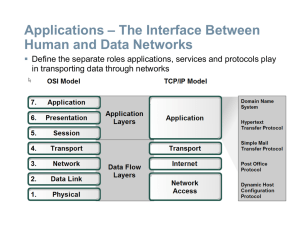
... Use the subnet mask to divide a network into smaller networks and describe the implications of dividing networks for network planners ...
... Use the subnet mask to divide a network into smaller networks and describe the implications of dividing networks for network planners ...
Semester 1 Chapter 11 - Institute of Technology Sligo
... When they try to communicate with devices whose IP addresses they know, they must determine the MAC addresses. ARP enables a computer to find the MAC address of the computer that is associated with an IP address. Some keep tables that contain all the MAC addresses and IP addresses of other devices t ...
... When they try to communicate with devices whose IP addresses they know, they must determine the MAC addresses. ARP enables a computer to find the MAC address of the computer that is associated with an IP address. Some keep tables that contain all the MAC addresses and IP addresses of other devices t ...
Microbursts - VSS Monitoring
... This is achieved by providing between 1,000 to 4,000 times more buffering behind each port than is available, in total, on a normal tap. Although, when smoothing out the bursts and fitting the packets into each aggregated or load balanced monitor port, the buffering may introduce some unavoidable ad ...
... This is achieved by providing between 1,000 to 4,000 times more buffering behind each port than is available, in total, on a normal tap. Although, when smoothing out the bursts and fitting the packets into each aggregated or load balanced monitor port, the buffering may introduce some unavoidable ad ...
ML-IP
... user port can be added to the 50 ms protected stream. The user traffic can be switched directly into the IP network by ML-IP’s internal switch, via one of the uplinks. All copper UTP Ethernet interfaces operate in both full- or half-duplex modes, at either 10 or 100 Mbps speed. Each interface termin ...
... user port can be added to the 50 ms protected stream. The user traffic can be switched directly into the IP network by ML-IP’s internal switch, via one of the uplinks. All copper UTP Ethernet interfaces operate in both full- or half-duplex modes, at either 10 or 100 Mbps speed. Each interface termin ...
Accounting Information Systems: Essential Concepts and
... Drawbacks of Distributed WANs Difficulty in maintaining adequate control and ...
... Drawbacks of Distributed WANs Difficulty in maintaining adequate control and ...
Systems Area: OS and Networking
... • All standards of the Internet are published as RFC (Request for Comments). But not all RFCs are Internet Standards ...
... • All standards of the Internet are published as RFC (Request for Comments). But not all RFCs are Internet Standards ...
VERDEX – the first mobile Verified Data Extraction solution
... • Reduce customer facing transaction times • Improve order-to-cash cycle time • Enables new revenue opportunities Stop by Intermec booth to see live demonstrations Look for launch announcements and news @ ...
... • Reduce customer facing transaction times • Improve order-to-cash cycle time • Enables new revenue opportunities Stop by Intermec booth to see live demonstrations Look for launch announcements and news @ ...
Local Area Networks
... computers and other devices when the distances exceed constraints of LANs and MANs. The public telephone system, or common carrier, is used for wide area networks. The great disadvantage of using the public telephone system is the reduction in transmission speed. The speed limitations are due to pro ...
... computers and other devices when the distances exceed constraints of LANs and MANs. The public telephone system, or common carrier, is used for wide area networks. The great disadvantage of using the public telephone system is the reduction in transmission speed. The speed limitations are due to pro ...
Diapositiva 1
... developed at GSI for slow control and small DAQsystems, based on an ETRAX processor. It includes an ATMEL micro-controller, which allows a more precise timing and protocol handling than the ETRAX processor. Thus it performs the low level communication tasks to the specific 1-wire and CANbus devices, ...
... developed at GSI for slow control and small DAQsystems, based on an ETRAX processor. It includes an ATMEL micro-controller, which allows a more precise timing and protocol handling than the ETRAX processor. Thus it performs the low level communication tasks to the specific 1-wire and CANbus devices, ...
Chapter 5
... (There is also a “don’t fragment bit” that can be set). Fragment offset contains the offset (in 8-byte units) of current fragment in the original datagram. Total length is changed to be the size of the fragment. Panwar, Mao, Ryoo, Li: TCP/IP Essentials ...
... (There is also a “don’t fragment bit” that can be set). Fragment offset contains the offset (in 8-byte units) of current fragment in the original datagram. Total length is changed to be the size of the fragment. Panwar, Mao, Ryoo, Li: TCP/IP Essentials ...
planetLab
... has its own packages, has its own services, is a weaker form of root that provides a local super user, has its own users, i.e own GID/UID namespace is confined to using some IP numbers only and, is confined to some area(s) of the file system. ...
... has its own packages, has its own services, is a weaker form of root that provides a local super user, has its own users, i.e own GID/UID namespace is confined to using some IP numbers only and, is confined to some area(s) of the file system. ...
The Web of Data emerging industries
... (dereference) those names. 3. When someone looks up a URI, provide useful information. 4. Include links to other URIs so that they can discover more things. ...
... (dereference) those names. 3. When someone looks up a URI, provide useful information. 4. Include links to other URIs so that they can discover more things. ...
Unit 3 - NIST NACOL
... within a room, office, buildings or up to few kilometers (2KM or 3KM). It connects the network resources such as computers, faxes, printers, and various networking devices. Moreover, user also can share the resources such as data, file, software, etc in the network. Common example of LAN is network ...
... within a room, office, buildings or up to few kilometers (2KM or 3KM). It connects the network resources such as computers, faxes, printers, and various networking devices. Moreover, user also can share the resources such as data, file, software, etc in the network. Common example of LAN is network ...
File
... At time t0, y detects the link-cost change, updates its DV, and informs its neighbors. At time t1, z receives the update from y and updates its table. It computes a new least cost to x and sends its neighbors its DV. ...
... At time t0, y detects the link-cost change, updates its DV, and informs its neighbors. At time t1, z receives the update from y and updates its table. It computes a new least cost to x and sends its neighbors its DV. ...
Selling an Idea or a Product
... log, sends a “yes” vote to the coordinator (site A) and crashes. – Site A crashes – Site B wakes up, checks its log and realizes that it had voted “yes” on the update. » It sends a message to site A, asking what happened. » At this point, B cannot change its mind and decide to abort, because the upd ...
... log, sends a “yes” vote to the coordinator (site A) and crashes. – Site A crashes – Site B wakes up, checks its log and realizes that it had voted “yes” on the update. » It sends a message to site A, asking what happened. » At this point, B cannot change its mind and decide to abort, because the upd ...
unit3
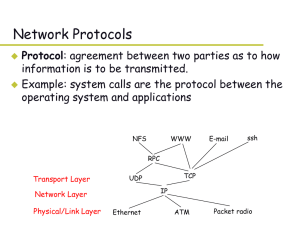
... Data segment format Timing Meanings of header fields Functions of TCP – also referred to as services provided by TCP ...
... Data segment format Timing Meanings of header fields Functions of TCP – also referred to as services provided by TCP ...
LAN Switching - Academic Server
... Switches perform two basic functions: Building and maintaining switching tables (similar to a bridge table) based on MAC addresses Switching frames out the interface to the destination Differences between switches & bridges Switches operate at higher speeds Switches are capable of creating virtual L ...
... Switches perform two basic functions: Building and maintaining switching tables (similar to a bridge table) based on MAC addresses Switching frames out the interface to the destination Differences between switches & bridges Switches operate at higher speeds Switches are capable of creating virtual L ...