ppt - Course Website Directory
... except the one it arrived on. Old LSA packets are dropped. The age of each packet, being stored after reception, is decremented once per time unit. When the age hits zero, the information is discarded. Initial age = high. Such state is often called soft state. ...
... except the one it arrived on. Old LSA packets are dropped. The age of each packet, being stored after reception, is decremented once per time unit. When the age hits zero, the information is discarded. Initial age = high. Such state is often called soft state. ...
Introduction to Computer Networks
... client host requests, receives service from always-on server e.g. Web browser/server; email client/server ...
... client host requests, receives service from always-on server e.g. Web browser/server; email client/server ...
Paper 1: A network test bed for highly mobile aerial nodes
... Source Routing (DSR) protocol at the network layer while communicating with other nodes via 802.11b at layer 2. We have implemented the DSR protocol ourselves using the Click Modular Router [Ref]. The reason we chose DSR over other ad-hoc protocols like AODV or TORA is because it’s routing is On-dem ...
... Source Routing (DSR) protocol at the network layer while communicating with other nodes via 802.11b at layer 2. We have implemented the DSR protocol ourselves using the Click Modular Router [Ref]. The reason we chose DSR over other ad-hoc protocols like AODV or TORA is because it’s routing is On-dem ...
HGiga PowerStation Product Presentation
... Internet connection is being closely monitored, such as response time, upstream / downstream traffic rate and the link utilization. The outbound traffic is redirected via the available best route(s). Enterprises benefit with more bandwidth at a lower cost. ...
... Internet connection is being closely monitored, such as response time, upstream / downstream traffic rate and the link utilization. The outbound traffic is redirected via the available best route(s). Enterprises benefit with more bandwidth at a lower cost. ...
No Slide Title
... – Preserve the Ethernet/802.3 frame format at the MAC Client Interface – Preserve the minimum and maximum frame size of the current 802.3 standard – Support full duplex operation only – Support star-wired local area networks using point-to-point links and structured cabling topologies – Support 802. ...
... – Preserve the Ethernet/802.3 frame format at the MAC Client Interface – Preserve the minimum and maximum frame size of the current 802.3 standard – Support full duplex operation only – Support star-wired local area networks using point-to-point links and structured cabling topologies – Support 802. ...
Chapter I: Introduction
... between the communicating end-points. In packet switching, packets are exchanged only as needed. In circuit switching, identity of the data being transferred is provided implicitly by its time slot or frequency assignment. In packet switching, identity of data must be explicitly specified by a hea ...
... between the communicating end-points. In packet switching, packets are exchanged only as needed. In circuit switching, identity of the data being transferred is provided implicitly by its time slot or frequency assignment. In packet switching, identity of data must be explicitly specified by a hea ...
(BPLC) Network
... receiver equipment or loads can be located. Every device connected to the power network represents a load to the network, whose model includes, besides its impedance value, noise source associated with it. The frequency dependent and time variant values of the loads can be obtained directly from mea ...
... receiver equipment or loads can be located. Every device connected to the power network represents a load to the network, whose model includes, besides its impedance value, noise source associated with it. The frequency dependent and time variant values of the loads can be obtained directly from mea ...
Communications - Pravin Shetty > Resume
... So What is The Internet ? • High speed Internet requires ISDN - but there is a catch ! This is not possible (at present) as it cannot be provided between a customer’s premises and the exchange where the length of copper wire is greater than 4.5Km. • Watch the outcomes of the Federal Government’s le ...
... So What is The Internet ? • High speed Internet requires ISDN - but there is a catch ! This is not possible (at present) as it cannot be provided between a customer’s premises and the exchange where the length of copper wire is greater than 4.5Km. • Watch the outcomes of the Federal Government’s le ...
Initial ranging scheme based on interpolated Zadoff-Chu sequences for OFDMA-PON Ali Razmtouz,
... The US transmission in an OFDMA-PON with K ONUs suffers from the fact that the received signal is a superposition of K components, which pass through different optical channels and thus experience different path delays (reflecting different fiber lengths from each ONU to the OLT) and different frequ ...
... The US transmission in an OFDMA-PON with K ONUs suffers from the fact that the received signal is a superposition of K components, which pass through different optical channels and thus experience different path delays (reflecting different fiber lengths from each ONU to the OLT) and different frequ ...
Detecting service violation in Internet and Mobile ad hoc networks
... • Stripe-based – Back-to-back packets experience similar congestion in a queue with a high probability – Receiver observes the incoming pattern – Infer internal characteristics using topology • Distributed (Overlay-based) – Edge routers form an overlay network for probing – Each edge router probes p ...
... • Stripe-based – Back-to-back packets experience similar congestion in a queue with a high probability – Receiver observes the incoming pattern – Infer internal characteristics using topology • Distributed (Overlay-based) – Edge routers form an overlay network for probing – Each edge router probes p ...
Week 2
... link. Many vendors support four links, and some up to 8 links, i.e., 8 times the speed. • It provides load balancing by divided data flow evenly over different links. • In the event of one link failure, it takes less than a second to recover from it. • Some NICs support Link Aggregation, allowing mu ...
... link. Many vendors support four links, and some up to 8 links, i.e., 8 times the speed. • It provides load balancing by divided data flow evenly over different links. • In the event of one link failure, it takes less than a second to recover from it. • Some NICs support Link Aggregation, allowing mu ...
Document
... • Client first sends request-to-send (RTS) frame • Access point sends clear-to-send (CTS) frame when ready to receive • Requesting client sends data, all other clients must wait ...
... • Client first sends request-to-send (RTS) frame • Access point sends clear-to-send (CTS) frame when ready to receive • Requesting client sends data, all other clients must wait ...
The Network Layer
... each arc of the graph representing a communication line (often called a link). To choose a route between a given pair of routers, the algorithm just finds the shortest path between them on the graph. One way of measuring path length is the number of hops. Another metric is the geographic distance in ...
... each arc of the graph representing a communication line (often called a link). To choose a route between a given pair of routers, the algorithm just finds the shortest path between them on the graph. One way of measuring path length is the number of hops. Another metric is the geographic distance in ...
nisscReport
... four interrelated parts: a set of command handlers, a set of event handlers, an encapsulated fixed-size frame, and a bundle of simple tasks each of which operate on its task. Each component has its tasks clearly declared to facilitate modularity. The high level components issue commands to lower lev ...
... four interrelated parts: a set of command handlers, a set of event handlers, an encapsulated fixed-size frame, and a bundle of simple tasks each of which operate on its task. Each component has its tasks clearly declared to facilitate modularity. The high level components issue commands to lower lev ...
Data Classification And Protection Standard
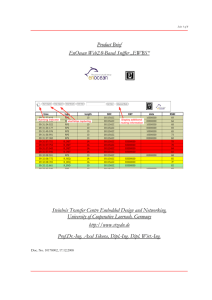
... See the table below for minimum standard protection requirements for each category of data when being used or handled in a specific context (e.g. Sensitive Data sent in an email message). Please note that the below protection standards are not intended to supersede any regulatory or contractual requ ...
... See the table below for minimum standard protection requirements for each category of data when being used or handled in a specific context (e.g. Sensitive Data sent in an email message). Please note that the below protection standards are not intended to supersede any regulatory or contractual requ ...
UDAY-DASARI_03112016
... districts of Rayalaseema region in A.P. by leading a team of 12 engineers Operation & Maintenance of Ericsson RBS, AXX, and SDH & PDH MW links with minimum down time. Responsible for TRU addition & deletion as per the site utilization report provided on Monthly basis by the DNP team. Coordinat ...
... districts of Rayalaseema region in A.P. by leading a team of 12 engineers Operation & Maintenance of Ericsson RBS, AXX, and SDH & PDH MW links with minimum down time. Responsible for TRU addition & deletion as per the site utilization report provided on Monthly basis by the DNP team. Coordinat ...
Outline
... • Works for idle connections (no deadlock) • Works for telnet (send one-byte packets immediately) • Works for bulk data transfer (delay sending) ...
... • Works for idle connections (no deadlock) • Works for telnet (send one-byte packets immediately) • Works for bulk data transfer (delay sending) ...
FFPF: Fairly Fast Packet Filters
... monitoring increasingly important hypothesis: multiple applications on single host ...
... monitoring increasingly important hypothesis: multiple applications on single host ...
Part I: Introduction
... 16-bit identifier flgs offset time to upper Internet layer live checksum ...
... 16-bit identifier flgs offset time to upper Internet layer live checksum ...
Overlay Networks and Tunneling Reading: 4.5, 9.4 Mike Freedman
... – A few friends who want beNer service – Just for their communicaVon with each other – E.g., VoIP, gaming, collaboraVve work, etc. ...
... – A few friends who want beNer service – Just for their communicaVon with each other – E.g., VoIP, gaming, collaboraVve work, etc. ...
layer - Open Learning Environment - Free University of Bozen
... OSI – Interaction Modalities • Connectionless: every package managed independently from the others – No guaranteed QoS – No memory nor negotiation, just isolated ...
... OSI – Interaction Modalities • Connectionless: every package managed independently from the others – No guaranteed QoS – No memory nor negotiation, just isolated ...
Datasheet - EnOcean Alliance
... with 256 telegrams), the application can even be used on a UMTS or GPRS connected device. ...
... with 256 telegrams), the application can even be used on a UMTS or GPRS connected device. ...
Software-Defined Wireless Transport Networks for - 5G
... The potential benefit of introducing SDN into the wireless and mobile world has already been identified in several works in the last years [14,15,16]. However few works have explicitly identified the opportunities of SDN to improve mobile backhaul performance. One of the few first works dealing with ...
... The potential benefit of introducing SDN into the wireless and mobile world has already been identified in several works in the last years [14,15,16]. However few works have explicitly identified the opportunities of SDN to improve mobile backhaul performance. One of the few first works dealing with ...
Mobile Applications and Web Services
... blocks of the TinyOS run-time environment. − Tasks are monolithic processes that should be executed until they are complete. − This means they can not be blocked by other tasks but they can be interrupted by events. − For example a packet reading task can schedule itself repeatedly (sending an event ...
... blocks of the TinyOS run-time environment. − Tasks are monolithic processes that should be executed until they are complete. − This means they can not be blocked by other tasks but they can be interrupted by events. − For example a packet reading task can schedule itself repeatedly (sending an event ...