投影片 1
... • The hypervisors implement vSwitch • Each VM has at least one virtual network interface cards (vNICs) and shared physical network interface cards (pNICs) on the physical host through vSwitch • Administrators don’t have effective solution to separate packets from different VM users • For VMs reside ...
... • The hypervisors implement vSwitch • Each VM has at least one virtual network interface cards (vNICs) and shared physical network interface cards (pNICs) on the physical host through vSwitch • Administrators don’t have effective solution to separate packets from different VM users • For VMs reside ...
IP Addresses - Paladin Group LLC
... A network Switch is just a multi-port bridge. Switches will often have 24 or more ports, and learns which MAC addresses are on which ports. • Works at layer 2 (data link) • On a switch a computer can send data AND receive data at the same time (full duplex… increasing performance by up to 2x) • On a ...
... A network Switch is just a multi-port bridge. Switches will often have 24 or more ports, and learns which MAC addresses are on which ports. • Works at layer 2 (data link) • On a switch a computer can send data AND receive data at the same time (full duplex… increasing performance by up to 2x) • On a ...
Tactical Information Operations for Autonomous Teams of
... Intra-team Communications UAV teams are highly collaborative in nature with a requirement for time-critical communications. Recall that UAVs in an autonomous team communicate amongst themselves via the wireless networking equipment carried aloft the individual vehicles. However, the transmission ran ...
... Intra-team Communications UAV teams are highly collaborative in nature with a requirement for time-critical communications. Recall that UAVs in an autonomous team communicate amongst themselves via the wireless networking equipment carried aloft the individual vehicles. However, the transmission ran ...
Internet PowerPoint - University at Albany
... only at system startup and is never a valid destination address. 2 Never a valid source address. 3 Should never appear on a network. ...
... only at system startup and is never a valid destination address. 2 Never a valid source address. 3 Should never appear on a network. ...
Packets and Protocols - St. Clair County Community College
... – WAN addresses in High-Level Data Link Control (HDLC) or frame relay network protocol addressing ...
... – WAN addresses in High-Level Data Link Control (HDLC) or frame relay network protocol addressing ...
Mobile Communications
... more than 1.2 billion subscribers in more than 630 networks more than 75% of all digital mobile phones use GSM (74% total) over 200 million SMS per month in Germany, > 550 billion/year worldwide (> 10% of the revenues for many operators) [be aware: these are only rough numbers…] ...
... more than 1.2 billion subscribers in more than 630 networks more than 75% of all digital mobile phones use GSM (74% total) over 200 million SMS per month in Germany, > 550 billion/year worldwide (> 10% of the revenues for many operators) [be aware: these are only rough numbers…] ...
History - Medical Imaging 1975-1980
... Tomography (the process of creating "slices" with x-rays) was originally (and not very effectively) conducted via physical manipulation of x-ray machinery. Prior to computerized tomography, there were only only had single plane films of the head showing bones or angiography, showing masses only when ...
... Tomography (the process of creating "slices" with x-rays) was originally (and not very effectively) conducted via physical manipulation of x-ray machinery. Prior to computerized tomography, there were only only had single plane films of the head showing bones or angiography, showing masses only when ...
Телекоммуникации: учебно
... Modern telecommunication centres on the problems involved in transmitting large volumes of information over long distances without damaging loss due to noise and interference. Figure 1 shows the basic components of a typical digital telecommunications system capable of transmitting voice, facsimile, ...
... Modern telecommunication centres on the problems involved in transmitting large volumes of information over long distances without damaging loss due to noise and interference. Figure 1 shows the basic components of a typical digital telecommunications system capable of transmitting voice, facsimile, ...
Collision domains vs. broadcast domains.
... burned in address of the interface. While the MAC address may be changed (or spoofed), most often it is set by the manufacturer and never changes. Switches and other Open Systems Interconnection (OSI) Layer 2 (data link layer) devices rely upon the MAC address in order to get network packets to the ...
... burned in address of the interface. While the MAC address may be changed (or spoofed), most often it is set by the manufacturer and never changes. Switches and other Open Systems Interconnection (OSI) Layer 2 (data link layer) devices rely upon the MAC address in order to get network packets to the ...
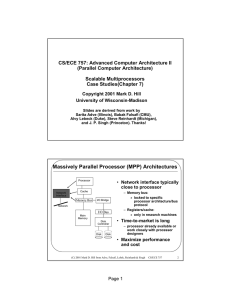
Massively Parallel Processor (MPP) Architectures
... 3D mesh direct interconnect Global address space up to 1 Mwords of DRAM per node MDP single-chip supports processing memory control message passing not an off-the-shelf chip ...
... 3D mesh direct interconnect Global address space up to 1 Mwords of DRAM per node MDP single-chip supports processing memory control message passing not an off-the-shelf chip ...
Case Report Forms
... Collect data from the investigational sites Helps project team and study site team • Reminder to investigator to perform specific evaluation • CRA uses to verify protocol is being followed and compare with source documents • Biometrics uses it to build database structures, develop edit checks and pr ...
... Collect data from the investigational sites Helps project team and study site team • Reminder to investigator to perform specific evaluation • CRA uses to verify protocol is being followed and compare with source documents • Biometrics uses it to build database structures, develop edit checks and pr ...
LURP
... So it sends an Address Resolution Protocol (ARP) packet to the broadcast ethernet address asking if anyone knows about mail.cs.byu.edu Everyone else will ignore it, mail.cs.byu.edu should respond with a packet indicating what his ethernet address is Your machine then puts this address into the desti ...
... So it sends an Address Resolution Protocol (ARP) packet to the broadcast ethernet address asking if anyone knows about mail.cs.byu.edu Everyone else will ignore it, mail.cs.byu.edu should respond with a packet indicating what his ethernet address is Your machine then puts this address into the desti ...
Transmission Control Protocol/Internet Protocol for the PC: an Ethernet implementation
... for the implementation of the communications package Transmission Control Protocol/Internet Protocol for the PC. A User's Manual is included as an appendix. The manual is specifically written for use in the Administrative Sciences Department Informations Systems laboratory at the Naval Postgraduate ...
... for the implementation of the communications package Transmission Control Protocol/Internet Protocol for the PC. A User's Manual is included as an appendix. The manual is specifically written for use in the Administrative Sciences Department Informations Systems laboratory at the Naval Postgraduate ...
Using ICT in an Organisational Environment (D3) IMIS DIPLOMA QUALIFICATIONS
... In local area networks where bus topology is used, each machine is connected to a single cable. Each computer or server is connected to the single bus cable through some kind of connector. A terminator is required at each end of the bus cable to prevent the signal from bouncing back and forth on the ...
... In local area networks where bus topology is used, each machine is connected to a single cable. Each computer or server is connected to the single bus cable through some kind of connector. A terminator is required at each end of the bus cable to prevent the signal from bouncing back and forth on the ...
Transmission-Control
... Costs of Congestion • Large queuing delays are experienced as the sending rate nears the output link capacity at a router • Sender must perform retransmissions in order to compensate for dropped (lost) packets due to buffer overflow • Router may send unneeded copies of packets if sender retransmits ...
... Costs of Congestion • Large queuing delays are experienced as the sending rate nears the output link capacity at a router • Sender must perform retransmissions in order to compensate for dropped (lost) packets due to buffer overflow • Router may send unneeded copies of packets if sender retransmits ...
FlexNIC: Rethinking Network DMA - Washington
... sharing a cache can benefit from low latency sharing. Even if most client requests arrive well-formed at the server and are of a common type—say, GET requests— network stacks and Memcached have to inspect each packet to determine where the client payload starts, to parse the client command, and to e ...
... sharing a cache can benefit from low latency sharing. Even if most client requests arrive well-formed at the server and are of a common type—say, GET requests— network stacks and Memcached have to inspect each packet to determine where the client payload starts, to parse the client command, and to e ...
Combining Feature Selection and Neural Networks for Solving
... The major criticisms of a neural network approach include the fact that because neural networks learn the classification rules by multiple passes over the training data set, the learning time, or the training time needed for a neural network to obtain a high classification rate, is usually long[1]. ...
... The major criticisms of a neural network approach include the fact that because neural networks learn the classification rules by multiple passes over the training data set, the learning time, or the training time needed for a neural network to obtain a high classification rate, is usually long[1]. ...
presentation
... than smoking (influence parameter significant). follow up on this, increase model complexity… ...
... than smoking (influence parameter significant). follow up on this, increase model complexity… ...
3rd Edition, Chapter 5 - Northwestern Networks Group
... fixed-length 40 byte header no fragmentation allowed ...
... fixed-length 40 byte header no fragmentation allowed ...
A Novel Back Up Wide Area Protection Technique for Power
... In the areas of power system automation and substation automation, there are two different trends: centralization and decentralization. More and more dynamic functions are moving from local and regional control centers toward central or national control centers. At the same time we also observe more ...
... In the areas of power system automation and substation automation, there are two different trends: centralization and decentralization. More and more dynamic functions are moving from local and regional control centers toward central or national control centers. At the same time we also observe more ...
Ad-hoc networks
... Simple routing protocol example Propagation of routing table Routing and transmitting ...
... Simple routing protocol example Propagation of routing table Routing and transmitting ...