ITI 510 - CJU.com - The Homepage Site of Chris Uriarte
... • Options - Not normally used, but when used the IP header length will be > 5 32-bit words to indicate the size of the options field ...
... • Options - Not normally used, but when used the IP header length will be > 5 32-bit words to indicate the size of the options field ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... the time and collect routes from each node to every extra node by before they are required, thus they are also called table-driven protocols [4]. In reactive protocols, routes are created when they are required by the source using a route detection method [5]. MANET is suitable for emerging situatio ...
... the time and collect routes from each node to every extra node by before they are required, thus they are also called table-driven protocols [4]. In reactive protocols, routes are created when they are required by the source using a route detection method [5]. MANET is suitable for emerging situatio ...
Cooperation in Wireless Communication Networks
... Cooperation in wireless communication networks requires many unique features in the MAC layer design. The MAC layer plays a vital role on answering some questions related to such a cooperative strategy. These questions include: when to use cooperation, whom to cooperate with, and how to select the c ...
... Cooperation in wireless communication networks requires many unique features in the MAC layer design. The MAC layer plays a vital role on answering some questions related to such a cooperative strategy. These questions include: when to use cooperation, whom to cooperate with, and how to select the c ...
atm98-786
... » setting up this connection doesn’t usually require address resolution – setting up H.245 control channel between terminals » potentially more intensive exchange of messages ...
... » setting up this connection doesn’t usually require address resolution – setting up H.245 control channel between terminals » potentially more intensive exchange of messages ...
A Ph.D PROPOSAL ON
... Optical fibre is a physical transmission medium applied for high speed data communications. Optical networks are adopted for efficient accommodation of traffic. Information is send from one place to another in the form of light pulses. Today’s fibre optic data systems are very complex, expensive and ...
... Optical fibre is a physical transmission medium applied for high speed data communications. Optical networks are adopted for efficient accommodation of traffic. Information is send from one place to another in the form of light pulses. Today’s fibre optic data systems are very complex, expensive and ...
Networking Hardware Components
... Solid - each Conductor is a single relatively thick Copper Wire (Solid Core) Stranded - each Conductor consists of a number of thin Copper Wires Solid Cable is used for infrastructure Cabling. The cable is inflexible because of its structure and the maximum length would be 100 metres. Stranded Cable ...
... Solid - each Conductor is a single relatively thick Copper Wire (Solid Core) Stranded - each Conductor consists of a number of thin Copper Wires Solid Cable is used for infrastructure Cabling. The cable is inflexible because of its structure and the maximum length would be 100 metres. Stranded Cable ...
Document
... WAP or Wireless application protocol is a protocol or process which provides a method to communicate across wireless networks quickly, securely and efficiently. It is a standardized way that a mobile phone talks to server installed in the mobile phone network. It is an important development in the w ...
... WAP or Wireless application protocol is a protocol or process which provides a method to communicate across wireless networks quickly, securely and efficiently. It is a standardized way that a mobile phone talks to server installed in the mobile phone network. It is an important development in the w ...
CH2-Topologies
... An extranet is a network or internetwork that is limited in scope to a single organization or entity but which also has limited connections to the networks of one or more other usually, but not necessarily, trusted organizations or entities (e.g. a company's customers may be given access to some par ...
... An extranet is a network or internetwork that is limited in scope to a single organization or entity but which also has limited connections to the networks of one or more other usually, but not necessarily, trusted organizations or entities (e.g. a company's customers may be given access to some par ...
3rd Edition: Chapter 4
... NEXT-HOP: indicates specific internal-AS router to next-hop AS. (may be multiple links from current AS to next-hop-AS) when gateway router receives route ...
... NEXT-HOP: indicates specific internal-AS router to next-hop AS. (may be multiple links from current AS to next-hop-AS) when gateway router receives route ...
An Introduction to MySQL Cluster
... STATUS – show status of node
START – start individual node
STOP – stop individual node
START BACKUP – all nodes backup their data
ENTER SINGLE USER MODE
CLUSTERLOG ON|OFF – start/stop logging at
different detail levels
CLUSTERLOG … - change logging for node
QUIT ...
...
networking standards and the osi model
... • Synchronizing the dialog between the two nodes • Determining whether communications have been cut ...
... • Synchronizing the dialog between the two nodes • Determining whether communications have been cut ...
Paul Swenson - Article Presentation
... packets are sent to each of the known addresses on the other end of the link (and using multiple interfaces on that host’s side) Based upon the received responses the communications channel is redirected over links that were successful in reaching the other host, thus preserving the information flow ...
... packets are sent to each of the known addresses on the other end of the link (and using multiple interfaces on that host’s side) Based upon the received responses the communications channel is redirected over links that were successful in reaching the other host, thus preserving the information flow ...
PPT
... • Technology did not match people’s experience with IP • deploying ATM in LAN is complex (e.g. broadcast) • supporting connection-less service model on connection-based technology • With IP over ATM, a lot of functionality is replicated • Currently used as a datalink layer supporting IP. Lecture #19 ...
... • Technology did not match people’s experience with IP • deploying ATM in LAN is complex (e.g. broadcast) • supporting connection-less service model on connection-based technology • With IP over ATM, a lot of functionality is replicated • Currently used as a datalink layer supporting IP. Lecture #19 ...
DoS
... • DoS is caused by asymmetric state allocation – If responder opens new state for each connection attempt, attacker can initiate thousands of connections from bogus or forged IP addresses ...
... • DoS is caused by asymmetric state allocation – If responder opens new state for each connection attempt, attacker can initiate thousands of connections from bogus or forged IP addresses ...
PDF
... TCP and SCTP are working on transport layer and they help in communication. SCTP is a four handshake scheme which also enhances the security of the system. In this work performance of TCP and SCTP is measured for Ad-hoc network and it has been analyzed that SCTP gives better result for all the netwo ...
... TCP and SCTP are working on transport layer and they help in communication. SCTP is a four handshake scheme which also enhances the security of the system. In this work performance of TCP and SCTP is measured for Ad-hoc network and it has been analyzed that SCTP gives better result for all the netwo ...
TCP/IP Basics
... A more efficient way to assign IP addresses than using IP address “classes” The network and host addresses boundary is not always made on octet boundaries, but may be made any specific number of bits from the beginning of the address Steal bits from the network address for use in the host address an ...
... A more efficient way to assign IP addresses than using IP address “classes” The network and host addresses boundary is not always made on octet boundaries, but may be made any specific number of bits from the beginning of the address Steal bits from the network address for use in the host address an ...
Scholarly Interest Report
... directly controls the behavior of the routers in an autonomous network and orchestrates network functions based on the DAG model. Maestro provides abstract views of the underlying network state and allows network functions to be realized as simple application programs that process and modify the abs ...
... directly controls the behavior of the routers in an autonomous network and orchestrates network functions based on the DAG model. Maestro provides abstract views of the underlying network state and allows network functions to be realized as simple application programs that process and modify the abs ...
Network Security
... Detecting Backdoors with NIDS Look for telltale signs of sniffer and rootkit activity Entrap sniffers into revealing themselves • Use bogus IP addresses and username/password pairs; open bogus TCP connections, then measure ping times – Sniffer may try a reverse DNS query on the planted address; r ...
... Detecting Backdoors with NIDS Look for telltale signs of sniffer and rootkit activity Entrap sniffers into revealing themselves • Use bogus IP addresses and username/password pairs; open bogus TCP connections, then measure ping times – Sniffer may try a reverse DNS query on the planted address; r ...
29 - BSNL Durg SSA(Connecting India)
... 1. Small Size and Light Weight: The size (diameter) of the optical fiber is very small. Therefore, a large number of optical fibers can fit into a cable of small diameter. 2. Easy availability and low cost: The material used for the manufacturing of optical fibers is silica glass. The material is ea ...
... 1. Small Size and Light Weight: The size (diameter) of the optical fiber is very small. Therefore, a large number of optical fibers can fit into a cable of small diameter. 2. Easy availability and low cost: The material used for the manufacturing of optical fibers is silica glass. The material is ea ...
2.1 Chapter 2 Network Models
... “Encapsulation”: Each layer has its own PDU that’s passes (as a parameter) to the layer beneath, which in turn adds a “ header ”(at layer 2 also adds trailer”) before assign to the next layer (except the physical layer). Why “header” and “trailer”? Physical movement of information PDU is “vertical” ...
... “Encapsulation”: Each layer has its own PDU that’s passes (as a parameter) to the layer beneath, which in turn adds a “ header ”(at layer 2 also adds trailer”) before assign to the next layer (except the physical layer). Why “header” and “trailer”? Physical movement of information PDU is “vertical” ...
Slide 1
... ORLA (Opportunistic Radio Link Adaptation) is the new improved routing algorithm for MeshConnex™, which enables faster route convergence and recovery. ORLA improves throughput by maintaining a high packet completion rate and it increases performance in noisy environments. ...
... ORLA (Opportunistic Radio Link Adaptation) is the new improved routing algorithm for MeshConnex™, which enables faster route convergence and recovery. ORLA improves throughput by maintaining a high packet completion rate and it increases performance in noisy environments. ...
document
... MSR failure can cause connection loss Hand-off latency increases due to state transfer Unless optimized, extra copying of data at MSR IFA’2004 ...
... MSR failure can cause connection loss Hand-off latency increases due to state transfer Unless optimized, extra copying of data at MSR IFA’2004 ...
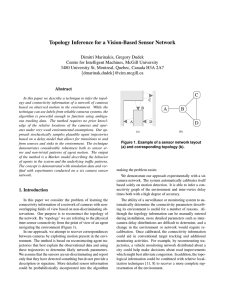
Topology Inference for a Vision-Based Sensor Network
... They are used to update our belief of the inter-node delay times and transition likelihoods. However, the data fit to the uniform distribution are believed to be transitions from the first vertex into the sink/source node and then from the sink/source node to the second vertex. Therefore, they are n ...
... They are used to update our belief of the inter-node delay times and transition likelihoods. However, the data fit to the uniform distribution are believed to be transitions from the first vertex into the sink/source node and then from the sink/source node to the second vertex. Therefore, they are n ...