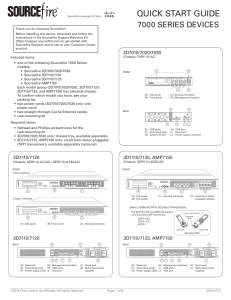
19_wireless
... Subtype – identifies function of frame To DS – 1 if destined for DS From DS – 1 if leaving DS More fragments – 1 if fragments follow Retry – 1 if retransmission of previous ...
... Subtype – identifies function of frame To DS – 1 if destined for DS From DS – 1 if leaving DS More fragments – 1 if fragments follow Retry – 1 if retransmission of previous ...
Slide 1
... • Security is especially important in a wireless network, since anyone walking or driving within the range of an AP (even outside a home or office) can use the network • A user can simply walk or drive around office buildings or homes with a WLAN-equipped computer and try to pick up a signal ...
... • Security is especially important in a wireless network, since anyone walking or driving within the range of an AP (even outside a home or office) can use the network • A user can simply walk or drive around office buildings or homes with a WLAN-equipped computer and try to pick up a signal ...
Principles of Electronic Communication Systems
... caller and callee must be established. It can easily take 10 seconds to set up the path ...
... caller and callee must be established. It can easily take 10 seconds to set up the path ...
85 Kyung Hee University BGP (cont`d)
... used by a router to withdraw destinations that have been advertised previously, announce a route to a new destination, or both ...
... used by a router to withdraw destinations that have been advertised previously, announce a route to a new destination, or both ...
Principles of Electronic Communication Systems
... caller and callee must be established. It can easily take 10 seconds to set up the path ...
... caller and callee must be established. It can easily take 10 seconds to set up the path ...
Document
... • Available on most but not all systems that have an IP stack. • Relies on the fact that routers should always decrement the TTL of a packet as it passes. • Generally uses ICMP packets on Windows and UDP packets on UNIX systems. However any IP protocol could be used in theory. ...
... • Available on most but not all systems that have an IP stack. • Relies on the fact that routers should always decrement the TTL of a packet as it passes. • Generally uses ICMP packets on Windows and UDP packets on UNIX systems. However any IP protocol could be used in theory. ...
POE - Altex
... The new IOGEAR Universal Wireless-N Adapter allows you to connect your device such as a Blu-ray player, HDTV, or game console to any Wireless-N network in your home or office. The Wireless-N (IEEE™ 802.11n) Adapter works with any device with an Ethernet port. No need to purchase an USB adapter that on ...
... The new IOGEAR Universal Wireless-N Adapter allows you to connect your device such as a Blu-ray player, HDTV, or game console to any Wireless-N network in your home or office. The Wireless-N (IEEE™ 802.11n) Adapter works with any device with an Ethernet port. No need to purchase an USB adapter that on ...
Semester 2 Chapter 12 - Institute of Technology Sligo
... Institute of Technology Sligo - Dept of Computing The assignment of a static route to reach the stub network 172.16.1.0 is proper for Cisco A because there is only one way to reach that network. A static route assignment is required for each destination network, in which case a default route may be ...
... Institute of Technology Sligo - Dept of Computing The assignment of a static route to reach the stub network 172.16.1.0 is proper for Cisco A because there is only one way to reach that network. A static route assignment is required for each destination network, in which case a default route may be ...
UDL Mesh Network over DVB-S
... Existing technology has inefficient spectrum usage Existing hub-based network averages two hops among nodes (high latency) DVB-S is a cost-effective method used in satellite TV broadcast (e.g., Astro) However, It is unidirectional in nature Unidirectional Link Mesh Network implements bidirectional n ...
... Existing technology has inefficient spectrum usage Existing hub-based network averages two hops among nodes (high latency) DVB-S is a cost-effective method used in satellite TV broadcast (e.g., Astro) However, It is unidirectional in nature Unidirectional Link Mesh Network implements bidirectional n ...
document
... Advantages of OSPF include: fast reconvergence, support for large networks, classless routing, VSLM, equal cost load balancing, and route tagging. Most Large networks use OSPF or IS-IS as their IGP. Existing working group for OSPF - show draft & website ...
... Advantages of OSPF include: fast reconvergence, support for large networks, classless routing, VSLM, equal cost load balancing, and route tagging. Most Large networks use OSPF or IS-IS as their IGP. Existing working group for OSPF - show draft & website ...
Survey of Routing Protocols for Mobile Ad-hoc - dl.edi
... Mobile ad-hoc network is deployed in applications such as disaster recovery and distributed collaborative computing, where routes are mostly multihop and network hosts communicate via packet radios[1]. Routing is one of the challenging issues in mobile ad-hoc network. Existing protocols for ad-hoc n ...
... Mobile ad-hoc network is deployed in applications such as disaster recovery and distributed collaborative computing, where routes are mostly multihop and network hosts communicate via packet radios[1]. Routing is one of the challenging issues in mobile ad-hoc network. Existing protocols for ad-hoc n ...
Link
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? ...
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? ...
Riga Technical University
... The model that is presented in this chapter helps to determine the number of drive-thru vehicles, depending on the distance to the base station and to determine real speed of data transfer for N drivethru vehicles, which are located in the zone of Drive-thru Internet system the base station. In the ...
... The model that is presented in this chapter helps to determine the number of drive-thru vehicles, depending on the distance to the base station and to determine real speed of data transfer for N drivethru vehicles, which are located in the zone of Drive-thru Internet system the base station. In the ...
GBBN IPV6 LAUNCH EVENT GBBN is using Internet Protocol
... about 360 million data users which are primarily mobile data subscribers. Envisaging the shortage of IPv4 addresses, Internet Protocol version 6 (IPv6) was developed by the Internet ...
... about 360 million data users which are primarily mobile data subscribers. Envisaging the shortage of IPv4 addresses, Internet Protocol version 6 (IPv6) was developed by the Internet ...
MobiNet: A Scalable Emulation Infrastructure for Ad Hoc and Wireless Networks
... on a single client machine, each with its own unique IP address. Since MobiNet clients use internal IP addresses (10.*), the number of clients that can be multiplexed onto an edge node is not limited by IP address space limitations, but rather by the amount of computational resources ( e.g. threads, ...
... on a single client machine, each with its own unique IP address. Since MobiNet clients use internal IP addresses (10.*), the number of clients that can be multiplexed onto an edge node is not limited by IP address space limitations, but rather by the amount of computational resources ( e.g. threads, ...
Virtual Router VPN Architecture
... Two or more corporate have network access to a limited amount of each other’s corporate data It’s a matter of control of who can access what data, i.e. a policy decision VR model supports extranet by allowing two or more VRs connect to each other with policy control for data flow ...
... Two or more corporate have network access to a limited amount of each other’s corporate data It’s a matter of control of who can access what data, i.e. a policy decision VR model supports extranet by allowing two or more VRs connect to each other with policy control for data flow ...
Electronic Shepherd – A Low-Cost, Low-Bandwidth, Wireless Network System Bjørn Thorstensen Tore Syversen
... closest to ours. Indeed, they seek to find low-power, positionaware, wireless communication systems, also including biological sensors, all of which is very relevant to our project. They describe a system for tracking wild animals over a large area, where collars mounted at each animal operate in a ...
... closest to ours. Indeed, they seek to find low-power, positionaware, wireless communication systems, also including biological sensors, all of which is very relevant to our project. They describe a system for tracking wild animals over a large area, where collars mounted at each animal operate in a ...
Two-Step Delay Based Internet Gateway Selection Felix Hoffmann, Daniel Medina Adam Wolisz
... this problem becomes even more important. The application of ad hoc networks to civil aviation has received relatively little attention so far. General issues regarding system design and network architecture have been addressed by Karras et al. in [2]. Sakhaee and Jamalipour [3] define a network ar ...
... this problem becomes even more important. The application of ad hoc networks to civil aviation has received relatively little attention so far. General issues regarding system design and network architecture have been addressed by Karras et al. in [2]. Sakhaee and Jamalipour [3] define a network ar ...
Network Building Blocks
... The beauty of digital signals is that they require simple circuitry and are easy to "clean up" after being affected by noise. At its most primitive level, digital equipment must be sensitive to only two frequencies—one that represents 1s and one that represents 0s. In contrast, analog equipment ...
... The beauty of digital signals is that they require simple circuitry and are easy to "clean up" after being affected by noise. At its most primitive level, digital equipment must be sensitive to only two frequencies—one that represents 1s and one that represents 0s. In contrast, analog equipment ...
Spanning Tree Protocol (STP)
... – Asynchronous serial (RS-232) – Synchronous serial (RS422/V.35) – HSSI (High Speed Serial Interface) – ISDN ...
... – Asynchronous serial (RS-232) – Synchronous serial (RS422/V.35) – HSSI (High Speed Serial Interface) – ISDN ...
point-to-point deep fiber access - NET-im-web
... includes an advanced aggregation switch and controller node, the ECN430. ECN430 includes 20 optical/electrical combo ports. If, as an example, the EFN324 fiber access nodes are daisy-chained in pairs, each ECN430 will aggregate and control up to 40 fiber access nodes and 960 end users. For larger no ...
... includes an advanced aggregation switch and controller node, the ECN430. ECN430 includes 20 optical/electrical combo ports. If, as an example, the EFN324 fiber access nodes are daisy-chained in pairs, each ECN430 will aggregate and control up to 40 fiber access nodes and 960 end users. For larger no ...