Chapter 2
... your firewall. However, you should consider disabling all remote logins to your internal system. It is best to allow only interactive logins at your firewall hosts. If you must log in the firewall host from other machines, use only a relatively secure login application, such as SSH with one time ...
... your firewall. However, you should consider disabling all remote logins to your internal system. It is best to allow only interactive logins at your firewall hosts. If you must log in the firewall host from other machines, use only a relatively secure login application, such as SSH with one time ...
Third-Party Adapter
... Wireless USB Adapter: A wireless networking device that is connected to a USB port on your computer using a USB cable. Using the Wireless USB Adapter, you can communicate with one or more computers that are equipped with wireless adapters. Where a standard Ethernet card requires a cable connection t ...
... Wireless USB Adapter: A wireless networking device that is connected to a USB port on your computer using a USB cable. Using the Wireless USB Adapter, you can communicate with one or more computers that are equipped with wireless adapters. Where a standard Ethernet card requires a cable connection t ...
Chapter 2 Applications and Layered Architectures
... Layering simplifies design, implementation, and testing by partitioning overall communications process into parts Protocol in each layer can be designed separately from those in other layers Protocol makes “calls” for services from layer below Layering provides flexibility for modifying and evolving ...
... Layering simplifies design, implementation, and testing by partitioning overall communications process into parts Protocol in each layer can be designed separately from those in other layers Protocol makes “calls” for services from layer below Layering provides flexibility for modifying and evolving ...
chapter3
... UDP: more • often used for streaming multimedia Length, in apps bytes of UDP – loss tolerant segment, including – rate sensitive • reliable transfer over UDP: add reliability at application layer – application-specific error recovery! ...
... UDP: more • often used for streaming multimedia Length, in apps bytes of UDP – loss tolerant segment, including – rate sensitive • reliable transfer over UDP: add reliability at application layer – application-specific error recovery! ...
1 - Education Queensland
... When the device is delivered it is pre-loaded with a ‘data only’ 3G SIM card. The device serial number and SIM card number is linked to the allocated student. Phone calls cannot be made using the SIM card. If the SIM cards are swapped between devices or inserted into mobile phones, it may permanentl ...
... When the device is delivered it is pre-loaded with a ‘data only’ 3G SIM card. The device serial number and SIM card number is linked to the allocated student. Phone calls cannot be made using the SIM card. If the SIM cards are swapped between devices or inserted into mobile phones, it may permanentl ...
Cisco uBR900 Series Cable Access Router
... Software router in one platform that contains dedicated hardware to achieve high-speed IP Security (IPSec) VPN performance. Fully standards-based, Cisco uBR900 Series Cable Access Routers operate in DOCSIS bridge mode similar to compliant modems, but include routing, advanced firewall, and IPSec VPN ...
... Software router in one platform that contains dedicated hardware to achieve high-speed IP Security (IPSec) VPN performance. Fully standards-based, Cisco uBR900 Series Cable Access Routers operate in DOCSIS bridge mode similar to compliant modems, but include routing, advanced firewall, and IPSec VPN ...
Chapter 11
... your firewall. However, you should consider disabling all remote logins to your internal system. It is best to allow only interactive logins at your firewall hosts. If you must log in the firewall host from other machines, use only a relatively secure login application, such as SSH with one time ...
... your firewall. However, you should consider disabling all remote logins to your internal system. It is best to allow only interactive logins at your firewall hosts. If you must log in the firewall host from other machines, use only a relatively secure login application, such as SSH with one time ...
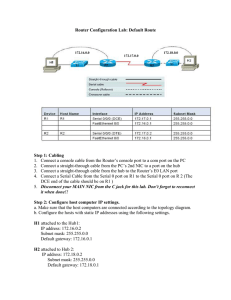
3 Router Configuration - Cisco Networking Academy
... b. Use some show commands to look around in your neighbor’s R1. c. Exit out of their R1 by typing exit Note: If you can NOT telnet to your neighbor’s Router, it is because the routing protocols and network numbers might not be configured properly, or the host names might not be configured properly. ...
... b. Use some show commands to look around in your neighbor’s R1. c. Exit out of their R1 by typing exit Note: If you can NOT telnet to your neighbor’s Router, it is because the routing protocols and network numbers might not be configured properly, or the host names might not be configured properly. ...
Fiber Optic Network Solutions
... In the broadband communication, the fiber optic network deployment is increasingly applied to today’s cloud applications and high-demanding multimedia streaming service. The fiber optic transmission has large advantages over the existing copper wire as the optic fiber cable carries much lower attenu ...
... In the broadband communication, the fiber optic network deployment is increasingly applied to today’s cloud applications and high-demanding multimedia streaming service. The fiber optic transmission has large advantages over the existing copper wire as the optic fiber cable carries much lower attenu ...
06-ethernet_sh
... Ethernet System Elements The Ethernet system consists of three basic elements: 1. the physical medium used to carry Ethernet signals between computers, 2. a set of medium access control rules embedded in each Ethernet interface that allow multiple computers to fairly arbitrate access to the shared ...
... Ethernet System Elements The Ethernet system consists of three basic elements: 1. the physical medium used to carry Ethernet signals between computers, 2. a set of medium access control rules embedded in each Ethernet interface that allow multiple computers to fairly arbitrate access to the shared ...
Modern Internet architecture & technology
... behaviors and controls in NATs, which results in a proliferation of devices whose behavior is highly unpredictable, extremely variable, and uncontrollable. Ultimately, the solution is to make the environment less hostile, and to introduce controls and standardized behaviors into NAT. However, until ...
... behaviors and controls in NATs, which results in a proliferation of devices whose behavior is highly unpredictable, extremely variable, and uncontrollable. Ultimately, the solution is to make the environment less hostile, and to introduce controls and standardized behaviors into NAT. However, until ...
Slides - GMU Computer Science
... • Attack would be stopped by proxy firewall • Incoming packet destroyed (old TTL value also destroyed) • New outgoing packet will not exceed TTL. ...
... • Attack would be stopped by proxy firewall • Incoming packet destroyed (old TTL value also destroyed) • New outgoing packet will not exceed TTL. ...
Multilin D400 - GE Grid Solutions
... • Increased availability and reliability of data through the presence of a third Ethernet interface, hotstandby functionality and Parallel Redundancy Protocol (PRP), IEC® 62439-3 Ed 2 scheme • Direct support for industry standard communication protocols (including IEC 61850) ensures connectivity w ...
... • Increased availability and reliability of data through the presence of a third Ethernet interface, hotstandby functionality and Parallel Redundancy Protocol (PRP), IEC® 62439-3 Ed 2 scheme • Direct support for industry standard communication protocols (including IEC 61850) ensures connectivity w ...
thesis-final-pune
... Concurrent sharing. A file is concurrently shared if two or more processes have it opn at the same time. Depending on the mode of the open, it could be read-sharing or write sharing; when the modes are not same, it is said to be concurrently shared. ...
... Concurrent sharing. A file is concurrently shared if two or more processes have it opn at the same time. Depending on the mode of the open, it could be read-sharing or write sharing; when the modes are not same, it is said to be concurrently shared. ...
For Internal Use Only - Guillevin Industrial Automation Group
... EAM (Memory Back up Adapter) ● The TCSEAM0100 memory backup adapter is a device for storing and updating configuration data and software of a TCSESM switch. ● In the case of a switch failure, the EAM enables a very simple configuration data transfer by means of a substitute switch of the same type. ...
... EAM (Memory Back up Adapter) ● The TCSEAM0100 memory backup adapter is a device for storing and updating configuration data and software of a TCSESM switch. ● In the case of a switch failure, the EAM enables a very simple configuration data transfer by means of a substitute switch of the same type. ...
Spanning Tree Protocol (STP)
... Step 3 Elect Designated Ports • A Designated Port functions as the single bridge port that both sends and receives traffic to and from that segment and the Root Bridge. • Each segment in a bridged network has one Designated Port, chosen based on cumulative Root Path Cost to the Root Bridge. • The sw ...
... Step 3 Elect Designated Ports • A Designated Port functions as the single bridge port that both sends and receives traffic to and from that segment and the Root Bridge. • Each segment in a bridged network has one Designated Port, chosen based on cumulative Root Path Cost to the Root Bridge. • The sw ...
Barometric Pressure, Temperature + Humidity iServer by OMEGA
... Display and Chart Measurements: The iServer transmitters come complete with a barometric pressure, temperature and humidity probe for measurement of a single location. ...
... Display and Chart Measurements: The iServer transmitters come complete with a barometric pressure, temperature and humidity probe for measurement of a single location. ...
Slide 1
... • overcome bus bandwidth limitations • A crossbar switch is an interconnection network consisting of 2N busses that connect N input ports to N output ports. • A packet arriving at an input port travels along the horizontal bus attached to the input port until it intersects with the vertical bus lead ...
... • overcome bus bandwidth limitations • A crossbar switch is an interconnection network consisting of 2N busses that connect N input ports to N output ports. • A packet arriving at an input port travels along the horizontal bus attached to the input port until it intersects with the vertical bus lead ...
Universal Plug and Play - Dead simple or simply
... The Internet Gateway Device profile allows port forwarding (via WANIPConnection or WANPPPConnection subprofiles). Network Address Translation (NAT) does not easily work with predefined ports. Workaround: programs dynamically agree on ports. Firewalls need to be dynamically adapted for this to work. ...
... The Internet Gateway Device profile allows port forwarding (via WANIPConnection or WANPPPConnection subprofiles). Network Address Translation (NAT) does not easily work with predefined ports. Workaround: programs dynamically agree on ports. Firewalls need to be dynamically adapted for this to work. ...
PinPoint X CoverTitle Quick Start Guide for Verizon
... Setup a DUN Connection: Create a Dial-Up Networking entry for local connection. This part of the setup is only needed if you will be using your PinPoint X to connect directly from a computer to the Internet or other network. ...
... Setup a DUN Connection: Create a Dial-Up Networking entry for local connection. This part of the setup is only needed if you will be using your PinPoint X to connect directly from a computer to the Internet or other network. ...
Configuring Q-in-Q VLAN Tunnels
... Q-in-Q is supported on port channels and vPC. To configure a port channel as an asymmetrical link, all ports in the port channel must have the same tunneling configuration. Using the 802.1Q tunneling feature, service providers can use a single VLAN to support customers who have multiple VLANs. Custo ...
... Q-in-Q is supported on port channels and vPC. To configure a port channel as an asymmetrical link, all ports in the port channel must have the same tunneling configuration. Using the 802.1Q tunneling feature, service providers can use a single VLAN to support customers who have multiple VLANs. Custo ...
Lecture 7
... • The IP layer allows packets to be sent over gateways to machines not on the physical network • Addresses used are IP addresses, 32-bit numbers divided into a network address (used for routing) and a host address • The IP protocol is connectionless, implying: – gateways route discrete packets indep ...
... • The IP layer allows packets to be sent over gateways to machines not on the physical network • Addresses used are IP addresses, 32-bit numbers divided into a network address (used for routing) and a host address • The IP protocol is connectionless, implying: – gateways route discrete packets indep ...
Module 2 Transport Layer Protocols
... We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
Parallel port

A parallel port is a type of interface found on computers (personal and otherwise) for connecting peripherals. In computing, a parallel port is a parallel communication physical interface. It is also known as a printer port or Centronics port. It was an industry de facto standard for many years, and was finally standardized as IEEE 1284 in the late 1990s, which defined the Enhanced Parallel Port (EPP) and Extended Capability Port (ECP) bi-directional versions. Today, the parallel port interface is seeing decreasing use because of the rise of Universal Serial Bus (USB) devices, along with network printing using Ethernet.The parallel port interface was originally known as the Parallel Printer Adapter on IBM PC-compatible computers. It was primarily designed to operate a line printer that used IBM's 8-bit extended ASCII character set to print text, but could also be used to adapt other peripherals. Graphical printers, along with a host of other devices, have been designed to communicate with the system.