INR11%20-%20OSPF
... Manipulating the election process If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on th ...
... Manipulating the election process If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on th ...
A Software Development Kit to exploit RINA
... • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) between two or more application instances, with certain characteristics (delay, loss, in-order-delivery, etc ...
... • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) between two or more application instances, with certain characteristics (delay, loss, in-order-delivery, etc ...
cis82-mod7-DistanceVectorRouting-RIP
... problem can require a count to infinity. • To avoid this prolonged problem, distance vector protocols define infinity as a specific maximum number. • This number refers to a routing metric which may simply be the hop count. • When the metric value exceeds the maximum value, and as each router receiv ...
... problem can require a count to infinity. • To avoid this prolonged problem, distance vector protocols define infinity as a specific maximum number. • This number refers to a routing metric which may simply be the hop count. • When the metric value exceeds the maximum value, and as each router receiv ...
NGN_internship
... Infect he is only the person who help me to pick the knowledge about VoIP, Data Communication and NGN, providing friendly environment, soft corner to seek the knowledge. He is a dedicated professional having sound knowledge and skill in the field and cooperative attitude. I have no words that can pr ...
... Infect he is only the person who help me to pick the knowledge about VoIP, Data Communication and NGN, providing friendly environment, soft corner to seek the knowledge. He is a dedicated professional having sound knowledge and skill in the field and cooperative attitude. I have no words that can pr ...
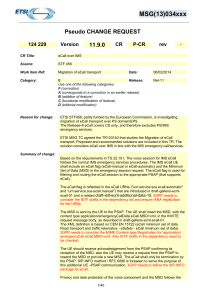
MSG(13)034xxx Pseudo CHANGE REQUEST 124 229 Version 11.9
... and "urn:service:sos.ecall.manual") that are introduced in draft-gellens-ecritecall-01 and a related draft-ietf-ecrit-additional-data-15. 3GPP needs to consider the IETF drafts in the dependency list and ensure IANA registration for the URNs. The MSD is sent by the UE to the PSAP. The UE shall inser ...
... and "urn:service:sos.ecall.manual") that are introduced in draft-gellens-ecritecall-01 and a related draft-ietf-ecrit-additional-data-15. 3GPP needs to consider the IETF drafts in the dependency list and ensure IANA registration for the URNs. The MSD is sent by the UE to the PSAP. The UE shall inser ...
Cisco RV180/RV180W Administration Guide
... The Cisco RV180/RV180W incorporates a Stateful Packet Inspection (SPI)-based router with Denial of Service (DoS) prevention and a Virtual Private Network (VPN) engine for secure communication between mobile or remote workers and branch offices. The Cisco RV180/RV180W supports up to ten gateway-to-ga ...
... The Cisco RV180/RV180W incorporates a Stateful Packet Inspection (SPI)-based router with Denial of Service (DoS) prevention and a Virtual Private Network (VPN) engine for secure communication between mobile or remote workers and branch offices. The Cisco RV180/RV180W supports up to ten gateway-to-ga ...
Chapter 7
... problem can require a count to infinity. • To avoid this prolonged problem, distance vector protocols define infinity as a specific maximum number. • This number refers to a routing metric which may simply be the hop count. • When the metric value exceeds the maximum value, and as each router receiv ...
... problem can require a count to infinity. • To avoid this prolonged problem, distance vector protocols define infinity as a specific maximum number. • This number refers to a routing metric which may simply be the hop count. • When the metric value exceeds the maximum value, and as each router receiv ...
PDF - Complete Book (3.07 MB)
... • A Cisco Cloud Services Router (CSR) 1000V virtual router with multiple networks on which workloads are placed and a single uplink with a Layer 3 connection to the datacenter network. • A Cisco Virtual Security Gateway (VSG) zone-based firewall to control and monitor segmentation policies within th ...
... • A Cisco Cloud Services Router (CSR) 1000V virtual router with multiple networks on which workloads are placed and a single uplink with a Layer 3 connection to the datacenter network. • A Cisco Virtual Security Gateway (VSG) zone-based firewall to control and monitor segmentation policies within th ...
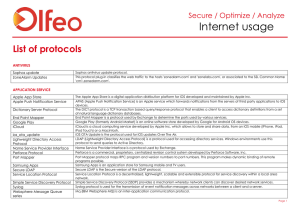
Protocols List
... Adobe Flash Media Playback is a dynamic HTTP streaming protocol used to access video contents from a smart client application. Fring is a peer-to-peer Mobile VoIP based Internet telephony network. GoToMeeting is an online meeting service developed by Citrix. Grooveshark is an online unlimited servic ...
... Adobe Flash Media Playback is a dynamic HTTP streaming protocol used to access video contents from a smart client application. Fring is a peer-to-peer Mobile VoIP based Internet telephony network. GoToMeeting is an online meeting service developed by Citrix. Grooveshark is an online unlimited servic ...
Analysis of Reliable Multicast Protocols
... Although the general format of the header is different for each message type, the first 4 bytes are common to all. ...
... Although the general format of the header is different for each message type, the first 4 bytes are common to all. ...
Cisco Industrial Ethernet 3000 Layer 2/Layer 3 Series Switches Data
... ● IEEE 802.1x with VLAN assignment, guest VLAN, and voice VLAN allows dynamic port-based security, providing user authentication. ● Port-based ACLs for Layer 2 interfaces allow application of security policies on individual switch ports. ● MAC address filtering prevents the forwarding of any type of ...
... ● IEEE 802.1x with VLAN assignment, guest VLAN, and voice VLAN allows dynamic port-based security, providing user authentication. ● Port-based ACLs for Layer 2 interfaces allow application of security policies on individual switch ports. ● MAC address filtering prevents the forwarding of any type of ...
Cisco Enhances per- IPSec Tunnel QoS, IOS Firewall Security for Unified
... © 2008 Cisco Systems, Inc. All rights reserved. ...
... © 2008 Cisco Systems, Inc. All rights reserved. ...
view pdf - Christoph Sommer and Falko Dressler: Vehicular
... “Vehicular Networking” by Christoph Sommer and Falko Dressler, published in December 2014 by Cambridge University Press. ▪ Except where otherwise noted (e.g., logos and cited works) this slide deck is Copyright © 2009‐2015 Christoph Sommer, but made available to you under a Creative Commons Attri ...
... “Vehicular Networking” by Christoph Sommer and Falko Dressler, published in December 2014 by Cambridge University Press. ▪ Except where otherwise noted (e.g., logos and cited works) this slide deck is Copyright © 2009‐2015 Christoph Sommer, but made available to you under a Creative Commons Attri ...
Cisco Wide Area Application Services Software Version 5.4
... the organization becomes increasingly difficult, causing IT departments to deploy costly and difficult-to-manage infrastructure at each location, including file services, email, video, software distribution, and print services. With continuous pressure from industry and federal regulation, IT depart ...
... the organization becomes increasingly difficult, causing IT departments to deploy costly and difficult-to-manage infrastructure at each location, including file services, email, video, software distribution, and print services. With continuous pressure from industry and federal regulation, IT depart ...
PAN‐OS Web Interface Reference Guide
... traffic allowed on the virtual wire. A tag value of zero indicates untagged traffic (the default). Multiple tags or ranges must be separated by commas. Traffic that has an excluded tag value is dropped. Tag values are not changed on incoming or outgoing packets. When utilizing virtual wire subint ...
... traffic allowed on the virtual wire. A tag value of zero indicates untagged traffic (the default). Multiple tags or ranges must be separated by commas. Traffic that has an excluded tag value is dropped. Tag values are not changed on incoming or outgoing packets. When utilizing virtual wire subint ...
PDF
... tool provides you with access to the Cisco bug tracking system, which maintains information about bugs and vulnerabilities in this product and other Cisco hardware and software products. For more information about the Bug Search Tool, see the Bug Search Tool Help & FAQ. ...
... tool provides you with access to the Cisco bug tracking system, which maintains information about bugs and vulnerabilities in this product and other Cisco hardware and software products. For more information about the Bug Search Tool, see the Bug Search Tool Help & FAQ. ...
On Modern DNS Behavior and Properties
... of 0.01% of packets in the worst case [21]. At this measurementbased loss rate we do not believe the insights from our analysis are skewed by our apparatus. Additionally, we experience measurement outages where no traffic is observed. These are caused by mundane logistical failures (e.g., temporaril ...
... of 0.01% of packets in the worst case [21]. At this measurementbased loss rate we do not believe the insights from our analysis are skewed by our apparatus. Additionally, we experience measurement outages where no traffic is observed. These are caused by mundane logistical failures (e.g., temporaril ...
On Modern DNS Behavior and Properties
... the routing system causing churn. Second, DNS responses are at the immediate and sole control of the content provider, and can be crafted to match content providers’ needs at the instant a client is interested in their content. The observation that DNS can deal with late binding of names to specific ...
... the routing system causing churn. Second, DNS responses are at the immediate and sole control of the content provider, and can be crafted to match content providers’ needs at the instant a client is interested in their content. The observation that DNS can deal with late binding of names to specific ...
slides 3
... side (expensive, time consuming, and good luck convincing your campus this is necessary…) – Mitigate the problems by moving your science equipment to the edge • Try to bypass that firewall at all costs • Get as close to the WAN connection as you can 37 – 5/25/2017, © 2009 Internet2 ...
... side (expensive, time consuming, and good luck convincing your campus this is necessary…) – Mitigate the problems by moving your science equipment to the edge • Try to bypass that firewall at all costs • Get as close to the WAN connection as you can 37 – 5/25/2017, © 2009 Internet2 ...
AMHS Connectivity - Airports Authority of India
... Ensure interoperability of products from different suppliers ASIA/PAC AMHS Manual • Conformance (Annex B) • Interoperability (Annex E) • Per-Operational (Annex F) ...
... Ensure interoperability of products from different suppliers ASIA/PAC AMHS Manual • Conformance (Annex B) • Interoperability (Annex E) • Per-Operational (Annex F) ...
Integrating Cisco Press Resources into the
... • Link-state routing raises two concerns: – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
... • Link-state routing raises two concerns: – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
Analysis of Reliable Multicast Protocols
... Although the general format of the header is different for each message type, the first 4 bytes are common to all. ...
... Although the general format of the header is different for each message type, the first 4 bytes are common to all. ...
Switch Router Design & Implementation
... New standards like DiffServ, RSVP, H.323, IPsec, can all be handled with the same chips at the same cost ...
... New standards like DiffServ, RSVP, H.323, IPsec, can all be handled with the same chips at the same cost ...