No Slide Title
... • iBGP when used as IGP • carries global routes around network • injected with eircom customer routes ...
... • iBGP when used as IGP • carries global routes around network • injected with eircom customer routes ...
What`s a protocol? - CS Course Webpages
... Frequency - {number of oscillations per second of the electromagnetic field of the signal} Bandwidth - {the width/size, in Hz, of the signal -usually defined by where most of the energy is} Data Rate - {the number of bits per second. Distinct from, but related to, frequency and bandwidth} Baud - {Ch ...
... Frequency - {number of oscillations per second of the electromagnetic field of the signal} Bandwidth - {the width/size, in Hz, of the signal -usually defined by where most of the energy is} Data Rate - {the number of bits per second. Distinct from, but related to, frequency and bandwidth} Baud - {Ch ...
Data Network Connectivity
... protocols and limiting unnecessary network traffic between routers. ...
... protocols and limiting unnecessary network traffic between routers. ...
ppt
... distinguish between different classes. 3. Protection (isolation) for one class from another. 4. While providing isolation, it is desirable to use resources as efficiently as possible sharing. ...
... distinguish between different classes. 3. Protection (isolation) for one class from another. 4. While providing isolation, it is desirable to use resources as efficiently as possible sharing. ...
ppt - Computer Science Division
... – protocols needed for reliable data transfer, congestion control • Q: How to provide circuit-like behavior? – bandwidth guarantees needed for audio/video apps – still an unsolved problem (chapter 6) ...
... – protocols needed for reliable data transfer, congestion control • Q: How to provide circuit-like behavior? – bandwidth guarantees needed for audio/video apps – still an unsolved problem (chapter 6) ...
Interconnection networks 2, clusters
... • Cut-through routing or wormhole routing: switch examines the header, decides where to send the message, and then starts forwarding it immediately – In wormhole routing, when head of message is blocked, message stays strung out over the network, potentially blocking other messages (needs only buffe ...
... • Cut-through routing or wormhole routing: switch examines the header, decides where to send the message, and then starts forwarding it immediately – In wormhole routing, when head of message is blocked, message stays strung out over the network, potentially blocking other messages (needs only buffe ...
Communication - Princeton University
... • But, how should these applications co-exist? – Multiple customized traffic-management protocols – On a shared underlying network – To maximize the aggregate utility of the users ...
... • But, how should these applications co-exist? – Multiple customized traffic-management protocols – On a shared underlying network – To maximize the aggregate utility of the users ...
William Stallings Data and Computer Communications
... Level in architecture at which entity is named Unique address for each end system (computer) and router Network level address IP or internet address (TCP/IP) Network service access point or NSAP (OSI) ...
... Level in architecture at which entity is named Unique address for each end system (computer) and router Network level address IP or internet address (TCP/IP) Network service access point or NSAP (OSI) ...
ch12
... errors. The frame is next passed to the network layer. The network layer determines the address of the next node, and encapsulates the remainder of the frame with new addressing data for the next node. It then passes the frame back to the data link layer, which reformats the frame suitably for the n ...
... errors. The frame is next passed to the network layer. The network layer determines the address of the next node, and encapsulates the remainder of the frame with new addressing data for the next node. It then passes the frame back to the data link layer, which reformats the frame suitably for the n ...
Network and Perimeter Security
... Application layer filtering includes the following: Web browsing and e-mail can be scanned to ensure that content specific to each does not contain illegitimate data Deep content analyses, including the ability to detect, inspect, and validate traffic using any port and protocol ...
... Application layer filtering includes the following: Web browsing and e-mail can be scanned to ensure that content specific to each does not contain illegitimate data Deep content analyses, including the ability to detect, inspect, and validate traffic using any port and protocol ...
Networking
... Mid 70's: First form of IP was developed by Advanced Research Project Agency (ARPA), a US government organization. Late 70's: With the involvement of many government and university research groups, TCP/IP started to take its latest form. Early 80's: Many improvements were made in the usage of TCP/IP ...
... Mid 70's: First form of IP was developed by Advanced Research Project Agency (ARPA), a US government organization. Late 70's: With the involvement of many government and university research groups, TCP/IP started to take its latest form. Early 80's: Many improvements were made in the usage of TCP/IP ...
Internet Architecture
... more it knows about the best what it needs Add functionality in lower layers iff it (1) is used by and improves performance of a large number of (current and potential future) applications, (2) does not hurt (too much) other applications, and (3) does not increase (too much) complexity/overhead ...
... more it knows about the best what it needs Add functionality in lower layers iff it (1) is used by and improves performance of a large number of (current and potential future) applications, (2) does not hurt (too much) other applications, and (3) does not increase (too much) complexity/overhead ...
presentation source
... Think of it as room in a house. The house has an address (IP), but each room (port) provides a certain function. Ports below 1024 are called “well known” ports. Only root has access to start services on these ports. Ports 1024 and above are called “ephemeral” ports. These ports are open to everyone ...
... Think of it as room in a house. The house has an address (IP), but each room (port) provides a certain function. Ports below 1024 are called “well known” ports. Only root has access to start services on these ports. Ports 1024 and above are called “ephemeral” ports. These ports are open to everyone ...
Class notes - Center For Information Management, Integration and
... • Aim of Internet2 is to install “gigapops” (gigabit capacity point of presence) capable of routing packets more quickly through the network (by launching a gigabit switch router to support speeds of 10Gbps) • With current Internet, real-time images have the same priority as email; Internet2 will be ...
... • Aim of Internet2 is to install “gigapops” (gigabit capacity point of presence) capable of routing packets more quickly through the network (by launching a gigabit switch router to support speeds of 10Gbps) • With current Internet, real-time images have the same priority as email; Internet2 will be ...
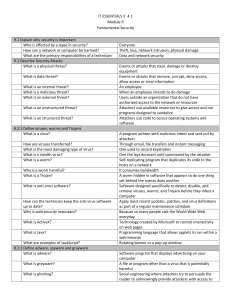
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
Chapter 3 OSI Model
... •Knowledge of both models is required by networking professionals.- According to article obtained from the internet networking professionals "need to know both models". •Both models assume that packets are switched.- Basically this means that individual packets may take differing paths in order to ...
... •Knowledge of both models is required by networking professionals.- According to article obtained from the internet networking professionals "need to know both models". •Both models assume that packets are switched.- Basically this means that individual packets may take differing paths in order to ...
ppt
... • First rule: test whether a packet destination is port 23 and drops the packet if it is • Second rule: tests whether a packet is received from the IP address 192.168.1.1 and alter the packet destination if it was ...
... • First rule: test whether a packet destination is port 23 and drops the packet if it is • Second rule: tests whether a packet is received from the IP address 192.168.1.1 and alter the packet destination if it was ...
Logic Programming for Software-Defined Networks Naga Praveen Katta Jennifer Rexford David Walker
... Recently [4, 10], however, we have seen the emergence of a new kind of network architecture, referred to as software-defined networking (SDN) that has the potential to do away with the plethora of special purpose network devices and the low-level interfaces we find in conventional networks. In a sof ...
... Recently [4, 10], however, we have seen the emergence of a new kind of network architecture, referred to as software-defined networking (SDN) that has the potential to do away with the plethora of special purpose network devices and the low-level interfaces we find in conventional networks. In a sof ...
Lecture Slides
... Each node generates independent data Any node can communicate with any other. No centralized controller (self-configuring) Data transmitted in (short) packets Links typically symmetric. Nodes may be mobile and/or power constrained. Typically a large number of nodes ...
... Each node generates independent data Any node can communicate with any other. No centralized controller (self-configuring) Data transmitted in (short) packets Links typically symmetric. Nodes may be mobile and/or power constrained. Typically a large number of nodes ...
IP, ATM, Wireless
... • Ethernet is one kind of link-level network. • IP is a more general form of network • IP packets are payload of an ethernet packet in an IP over ethernet network (most modern nets) – Those nets have packets with both ethernet and IP addresses in packet. – Locally, communication uses ethernet addres ...
... • Ethernet is one kind of link-level network. • IP is a more general form of network • IP packets are payload of an ethernet packet in an IP over ethernet network (most modern nets) – Those nets have packets with both ethernet and IP addresses in packet. – Locally, communication uses ethernet addres ...
Internet Telephony Gateway
... with other LAN users. With an optimized H.323 and routing architecture, the PLANET VIP-210 is the ideal choice for Voice over IP communications and providing integrated Internet sharing features, such as Virtual server, policy based firewall protection, QoS and DMZ support. With these features, user ...
... with other LAN users. With an optimized H.323 and routing architecture, the PLANET VIP-210 is the ideal choice for Voice over IP communications and providing integrated Internet sharing features, such as Virtual server, policy based firewall protection, QoS and DMZ support. With these features, user ...