Uppsala University.
... and the network has recently been upgraded to have its own dual BGP peering with our ISP and local peering for university trafic. It is of course based on our own successful Linux/Bifrost [7] concept. The current network topologi is seen in Figure 3. Throughout the years there have been many problem ...
... and the network has recently been upgraded to have its own dual BGP peering with our ISP and local peering for university trafic. It is of course based on our own successful Linux/Bifrost [7] concept. The current network topologi is seen in Figure 3. Throughout the years there have been many problem ...
CS 105 - HMC Computer Science
... connections between clients and servers How to use Unix I/O to copy data from one host to another over an Internet connection ...
... connections between clients and servers How to use Unix I/O to copy data from one host to another over an Internet connection ...
Backhauling X2 - Cambridge Broadband Networks
... The rapid adoption of data services has forced the wireless industry to rethink the way that mobile services are delivered. Compared to voice, data requires significantly more traffic and must be delivered at a much lower cost per bit in order to be profitable for operators. The industry has been wo ...
... The rapid adoption of data services has forced the wireless industry to rethink the way that mobile services are delivered. Compared to voice, data requires significantly more traffic and must be delivered at a much lower cost per bit in order to be profitable for operators. The industry has been wo ...
Enabling secure remote access
... Internal application Runs on a web server New business requirement for providing access while not attached to corpnet E-mail (Outlook Web Access) File sharing (SharePoint varieties) Custom applications ...
... Internal application Runs on a web server New business requirement for providing access while not attached to corpnet E-mail (Outlook Web Access) File sharing (SharePoint varieties) Custom applications ...
Wireless Local Area Networks
... oven, Bluetooth, and others Security Current WEP algorithm is weak - usually not ON! Roaming No industry standard is available and propriety solution are not interoperable - especially with GSM Inter-operability Only few basic functionality are interoperable, other vendor’s features can’t be u ...
... oven, Bluetooth, and others Security Current WEP algorithm is weak - usually not ON! Roaming No industry standard is available and propriety solution are not interoperable - especially with GSM Inter-operability Only few basic functionality are interoperable, other vendor’s features can’t be u ...
Defense Against the DoS/DDoS Attacks on Cisco Routers
... tools are available. Many DoS/DDoS attackers lack the skill or motivation to create their own tools, and use programs found on the Internet; these tools tend to fall in and out of fashion. Many of the commonly used DoS/DDoS attacks are based on high-bandwidth packet floods, or on other repetitive st ...
... tools are available. Many DoS/DDoS attackers lack the skill or motivation to create their own tools, and use programs found on the Internet; these tools tend to fall in and out of fashion. Many of the commonly used DoS/DDoS attacks are based on high-bandwidth packet floods, or on other repetitive st ...
Document
... • The Layer 2 switch can only recognize its own local MAC addresses and cannot handle Layer 3 IP addresses • When a host has data for a non-local IP address, it sends the frame to the closest router, also known as its default gateway • The host uses the MAC address of the router as the destination ...
... • The Layer 2 switch can only recognize its own local MAC addresses and cannot handle Layer 3 IP addresses • When a host has data for a non-local IP address, it sends the frame to the closest router, also known as its default gateway • The host uses the MAC address of the router as the destination ...
test 1 - answer
... + Link layer retransmissions avoid having to retransmit over the entire path. Transport and application layer retransmissions must be sent over the entire path, thus incurring higher latency and wasting bandwidth. + Link layer retransmissions can hide non-congestion losses from higher layer protocol ...
... + Link layer retransmissions avoid having to retransmit over the entire path. Transport and application layer retransmissions must be sent over the entire path, thus incurring higher latency and wasting bandwidth. + Link layer retransmissions can hide non-congestion losses from higher layer protocol ...
Document
... none of the versions of Ethernet uses straight binary encoding with 0 volts for a 0bit and 5 volts for a 1 bit. all Ethernet systems use manchester encoding due to its simplicity ...
... none of the versions of Ethernet uses straight binary encoding with 0 volts for a 0bit and 5 volts for a 1 bit. all Ethernet systems use manchester encoding due to its simplicity ...
6 Lecture 6 Intro to Switching & Circuit Switching
... 2. at the data-link layer we can have packet switching. However, the packet can mean frame or cells here. Packet switching is done normally using Virtual Circuit Approach. 3. at the network layer we can have packet switching. Here, either a virtual circuit or datagram approach can be used. Internet ...
... 2. at the data-link layer we can have packet switching. However, the packet can mean frame or cells here. Packet switching is done normally using Virtual Circuit Approach. 3. at the network layer we can have packet switching. Here, either a virtual circuit or datagram approach can be used. Internet ...
The Network Layer
... This field defines the higher level protocol (transport-layer) that uses the services of IP-layer. An IP datagram can encapsulate data from several higher-level protocols such as: TCP=6, UDP=17, ICMP=1, IGMP=2, OSPF=89. This field specifies the final destination protocol to which the IP datagram sho ...
... This field defines the higher level protocol (transport-layer) that uses the services of IP-layer. An IP datagram can encapsulate data from several higher-level protocols such as: TCP=6, UDP=17, ICMP=1, IGMP=2, OSPF=89. This field specifies the final destination protocol to which the IP datagram sho ...
ppt - Carnegie Mellon University
... • Loops are detected as follows: • When AS gets route, check if AS already in path • If yes, reject route • If no, add self and (possibly) advertise route further ...
... • Loops are detected as follows: • When AS gets route, check if AS already in path • If yes, reject route • If no, add self and (possibly) advertise route further ...
Ensuring Service Quality While Increasing Revenue
... • Correlate signaling across both trusted and untrusted sides of SBC ...
... • Correlate signaling across both trusted and untrusted sides of SBC ...
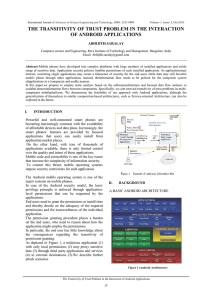
the transitivity of trust problem in the interaction of android
... Abstract-Mobile phones have developed into complex platforms with large numbers of installed applications and awide range of sensitive data. Application security policies limitthe permissions of each installed application. As applicationsmay interact, restricting single applications may create a fal ...
... Abstract-Mobile phones have developed into complex platforms with large numbers of installed applications and awide range of sensitive data. Application security policies limitthe permissions of each installed application. As applicationsmay interact, restricting single applications may create a fal ...
Internet of Things
... The DSL can replace more traditional mobile network OSS by providing transactional idempotent processes for massively distributed “Things” ...
... The DSL can replace more traditional mobile network OSS by providing transactional idempotent processes for massively distributed “Things” ...
200470 Exam Solution
... provided Use diagrams where appropriate to enhance your answer.) 1. Name and describe in as much detail as you can each of the seven layers of the OSI reference model? 7. Application Layer. Layer closest to user. Provides network services to users applications. 2 marks 6. Presentation Layer. Transla ...
... provided Use diagrams where appropriate to enhance your answer.) 1. Name and describe in as much detail as you can each of the seven layers of the OSI reference model? 7. Application Layer. Layer closest to user. Provides network services to users applications. 2 marks 6. Presentation Layer. Transla ...
Internetworking I - Carnegie Mellon School of Computer Science
... » Channel sending 8000 samples / second, up to 8-bits/sample – DAC encodes each sample with 92 or 128 voltage levels » Not enough precision on analog side to handle finer resolution – Receiver converts samples back to digital values » Must match frequency & phase of senders DAC ...
... » Channel sending 8000 samples / second, up to 8-bits/sample – DAC encodes each sample with 92 or 128 voltage levels » Not enough precision on analog side to handle finer resolution – Receiver converts samples back to digital values » Must match frequency & phase of senders DAC ...
VPN Traffic Explorer
... upgraded, or if CoS configurations need to be modified, avoiding guesswork and service disruptions. On-line routing and traffic modeling delivers the industry’s most accurate “what-if” simulations for failure analysis, planning network changes, or understanding the impact of adding new customers, si ...
... upgraded, or if CoS configurations need to be modified, avoiding guesswork and service disruptions. On-line routing and traffic modeling delivers the industry’s most accurate “what-if” simulations for failure analysis, planning network changes, or understanding the impact of adding new customers, si ...
Lecture 20: IP Protocol
... We need someway of defining smaller networks (subnets) for departments, buildings, etc. And be able to aggregate these into the designated network (left x bits) That is called classless addressing ...
... We need someway of defining smaller networks (subnets) for departments, buildings, etc. And be able to aggregate these into the designated network (left x bits) That is called classless addressing ...
Chapter 1 Slides
... For large file transfer, bandwidth is critical For small messages (HTTP, NFS, etc.), latency is critical Variance in latency (jitter) can also affect some applications (e.g., audio/video conferencing) ...
... For large file transfer, bandwidth is critical For small messages (HTTP, NFS, etc.), latency is critical Variance in latency (jitter) can also affect some applications (e.g., audio/video conferencing) ...
Chapter 1: Foundation
... For large file transfer, bandwidth is critical For small messages (HTTP, NFS, etc.), latency is critical Variance in latency (jitter) can also affect some applications (e.g., audio/video conferencing) ...
... For large file transfer, bandwidth is critical For small messages (HTTP, NFS, etc.), latency is critical Variance in latency (jitter) can also affect some applications (e.g., audio/video conferencing) ...
Slides
... ARROW runs on a small ISP we control Evaluation: ARROW effective even if only a single tier-1 ISP adopts ...
... ARROW runs on a small ISP we control Evaluation: ARROW effective even if only a single tier-1 ISP adopts ...
Congestion Control Problem
... • The capacity of the Premium Traffic is dynamically allocated up to a maximum. The algorithm uses the error (queue size x p (t ) – reference queue size xref ) as the feedback signal to calculate the capacity C p (t ) p (t ) to be allocated.The sampling interval is set to Ts . • The Ordinary Traffic ...
... • The capacity of the Premium Traffic is dynamically allocated up to a maximum. The algorithm uses the error (queue size x p (t ) – reference queue size xref ) as the feedback signal to calculate the capacity C p (t ) p (t ) to be allocated.The sampling interval is set to Ts . • The Ordinary Traffic ...