sophisticated methods
... each individual host seen in the network. When a network connection is detected each endpoint host becomes a candidate peer. A candidate peer that has additional P2P traffic becomes an active peer and is reported as active. Otherwise is becomes a non-peer after it has had no P2P traffic for a probat ...
... each individual host seen in the network. When a network connection is detected each endpoint host becomes a candidate peer. A candidate peer that has additional P2P traffic becomes an active peer and is reported as active. Otherwise is becomes a non-peer after it has had no P2P traffic for a probat ...
wireless-transport
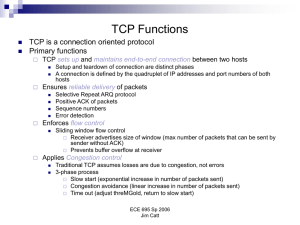
... – Provides “reliable, connection oriented transport protocol” – It is an “end-to-end protocol that supports flow and congestion control” – Used for Web, email, FTP and many other Internet applications (majority of Internet traffic is TCP) – Has been designed and optimised for wired networks ...
... – Provides “reliable, connection oriented transport protocol” – It is an “end-to-end protocol that supports flow and congestion control” – Used for Web, email, FTP and many other Internet applications (majority of Internet traffic is TCP) – Has been designed and optimised for wired networks ...
Chapter 1 Lecture Presentation
... E-mail & web build on reliable stream service Fax and modems build on basic telephone service ...
... E-mail & web build on reliable stream service Fax and modems build on basic telephone service ...
Paper - Asee peer logo
... remote host at a specific port number. The client reads a line from its standard input, takes a time stamp, and writes it to the server. The server reads a line from its network input echoes this line back to the client. The client reads the echoed line, again takes a time stamp and determines the r ...
... remote host at a specific port number. The client reads a line from its standard input, takes a time stamp, and writes it to the server. The server reads a line from its network input echoes this line back to the client. The client reads the echoed line, again takes a time stamp and determines the r ...
To start with, the Internet of Things is new
... cellular network has become the first access point to the internet for many mobile devices, however, this network is based on an addressing and transport architecture derived from switching technology, then from routing technology based on the IPv4. ...
... cellular network has become the first access point to the internet for many mobile devices, however, this network is based on an addressing and transport architecture derived from switching technology, then from routing technology based on the IPv4. ...
Network Security
... the firewall setup Firewall ensures that the internal network and the Internet can both talk to the DMZ, but usually not to each other The DMZ relays services at the application level, e.g. mail forwarding, web proxying The DMZ machines and firewall are centrally administered by people focused on s ...
... the firewall setup Firewall ensures that the internal network and the Internet can both talk to the DMZ, but usually not to each other The DMZ relays services at the application level, e.g. mail forwarding, web proxying The DMZ machines and firewall are centrally administered by people focused on s ...
Wanted: Systems abstractions for SDN
... Click satisfies our needs for configuring network processing in an abstract and holistic manner. Ths Click language helps specify an entire networking configuration in a single program with an intuitive syntax, as opposed to Linux, in which configurations are scattered across multiple files. In Clic ...
... Click satisfies our needs for configuring network processing in an abstract and holistic manner. Ths Click language helps specify an entire networking configuration in a single program with an intuitive syntax, as opposed to Linux, in which configurations are scattered across multiple files. In Clic ...
Document
... There are many technical reasons for the increasingly widespread use of networks. These include: ...
... There are many technical reasons for the increasingly widespread use of networks. These include: ...
Path Splicing with Network Slicing
... “It is not difficult to create a list of desired characteristics for a new Internet. Deciding how to design and deploy a network that achieves these goals is much harder. Over time, our list will evolve. It should be: 1. Robust and available. The network should be as robust, fault-tolerant and avail ...
... “It is not difficult to create a list of desired characteristics for a new Internet. Deciding how to design and deploy a network that achieves these goals is much harder. Over time, our list will evolve. It should be: 1. Robust and available. The network should be as robust, fault-tolerant and avail ...
Medium Access Control
... • If line is idle (no carrier sensed) send packet immediately • If line is busy (carrier sensed) wait until idle and transmit packet immediately • If collision detected – Stop sending and jam signal – Jam signal: make sure all other transmitters are aware of collision – Wait a random time (Exponenti ...
... • If line is idle (no carrier sensed) send packet immediately • If line is busy (carrier sensed) wait until idle and transmit packet immediately • If collision detected – Stop sending and jam signal – Jam signal: make sure all other transmitters are aware of collision – Wait a random time (Exponenti ...
chapter5d
... protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address negotiation: endpoint can learn/configure each o ...
... protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address negotiation: endpoint can learn/configure each o ...
WN7 92-93-2 Random Access and Wireless LAN
... Simple protocols, even if of low efficiency, are useful if the per node throughput that the protocol obtains is significant compared to the throughput required by the nodes in the network. Two key wireless MAC protocols: Aloha and CSMA/CA. ...
... Simple protocols, even if of low efficiency, are useful if the per node throughput that the protocol obtains is significant compared to the throughput required by the nodes in the network. Two key wireless MAC protocols: Aloha and CSMA/CA. ...
Securing Mobile Ad Hoc Networks Using Spread Spectrum Tech
... attacks cannot be classified as internal or external, especially at the network layer. The majority of the currently considered MANET protocols were not originally designed to deal with malicious behavior or other security threats and are the reason why they are so easy to abuse of. Spread Spectrum ...
... attacks cannot be classified as internal or external, especially at the network layer. The majority of the currently considered MANET protocols were not originally designed to deal with malicious behavior or other security threats and are the reason why they are so easy to abuse of. Spread Spectrum ...
Slides
... May want to use a LIFO queue on a node, to get latest packets delivered (least delay) Fairness for packets from different merging routes suggests round robin service over many queues May ...
... May want to use a LIFO queue on a node, to get latest packets delivered (least delay) Fairness for packets from different merging routes suggests round robin service over many queues May ...
Modeling Networks as Graphs
... The sliding window protocol can solve wasted bandwidth problems by using more sophisticated ARQ technique. In sliding window protocol sequence number is assigned to the messages that sender sends to receiver. The sliding window protocol begins by choosing a window size W. Data messages are i ...
... The sliding window protocol can solve wasted bandwidth problems by using more sophisticated ARQ technique. In sliding window protocol sequence number is assigned to the messages that sender sends to receiver. The sliding window protocol begins by choosing a window size W. Data messages are i ...
SPADE: Statistical Packet Acceptance Defense Engine
... algorithm analyzes the tree to identify which packets to remove, relative to their contribution to the excess load. Many DoS/DDoS detection systems use time intervals. At the end of each interval they try identifying suspicious traffic. As a result, short attacks that start and end within one interv ...
... algorithm analyzes the tree to identify which packets to remove, relative to their contribution to the excess load. Many DoS/DDoS detection systems use time intervals. At the end of each interval they try identifying suspicious traffic. As a result, short attacks that start and end within one interv ...
Network services - Internet Network Architectures
... • Fixed TCP/IP stack • Hardware implementation of forwarding ...
... • Fixed TCP/IP stack • Hardware implementation of forwarding ...
Lect15
... • Provides reliable data delivery by using IP unreliable datagram delivery • Compensates for loss, delay, duplication and similar problems in Internet components • Reliable delivery: applications do not worry about errors – rely on the layer below. IP ...
... • Provides reliable data delivery by using IP unreliable datagram delivery • Compensates for loss, delay, duplication and similar problems in Internet components • Reliable delivery: applications do not worry about errors – rely on the layer below. IP ...
KR2518691873
... devices to dynamically self organize into arbitrary and temporary wireless topologies without fixed communication infrastructure. One of the most popular MAC layer protocol used in Ad hoc network is 802.11b. Since the IEEE 802.11 standard support multiple data rates at the physical layer, many rate ...
... devices to dynamically self organize into arbitrary and temporary wireless topologies without fixed communication infrastructure. One of the most popular MAC layer protocol used in Ad hoc network is 802.11b. Since the IEEE 802.11 standard support multiple data rates at the physical layer, many rate ...
Overview and History
... most Web pages are static (contents are the same each time it is accessed) text/links/images are displayed in a page e.g., online documents, most homepages HyperText Markup Language (HTML) is used to specify text/image format ...
... most Web pages are static (contents are the same each time it is accessed) text/links/images are displayed in a page e.g., online documents, most homepages HyperText Markup Language (HTML) is used to specify text/image format ...
presentation
... Differentiated Services At the Ingress/Egress nodes Classify packets via packet inspection Meter the temporal state of the packet (i.e., rate) Mark the packets’ Diffserv Code Point (DSCP) according to its class Shape the packets (drop or delay) At other nodes, Per-Hop Behavior (PHB) is appli ...
... Differentiated Services At the Ingress/Egress nodes Classify packets via packet inspection Meter the temporal state of the packet (i.e., rate) Mark the packets’ Diffserv Code Point (DSCP) according to its class Shape the packets (drop or delay) At other nodes, Per-Hop Behavior (PHB) is appli ...