Re-ECN - Bob Briscoe
... • initial designs of policer and dropper with bounded state using sampling • don’t need port numbers – can just use IP address(es) ...
... • initial designs of policer and dropper with bounded state using sampling • don’t need port numbers – can just use IP address(es) ...
No Slide Title
... • Performance starts with the application – VPN solution must take applications into consideration – Different applications have different needs ...
... • Performance starts with the application – VPN solution must take applications into consideration – Different applications have different needs ...
TIE Breaking: Tunable Interdomain Egress Selection
... of the Internet has multiple egress routers. In addition, many customers connect to their provider in multiple locations for fault tolerance and more flexible load balancing, resulting in multiple egress routers for these destinations as well. In this paper, we argue that selecting among multiple eg ...
... of the Internet has multiple egress routers. In addition, many customers connect to their provider in multiple locations for fault tolerance and more flexible load balancing, resulting in multiple egress routers for these destinations as well. In this paper, we argue that selecting among multiple eg ...
PowerConnect W-Series OS (OPERATING SYSTEM
... whether it is Wi-Fi roaming without loss of voice sessions or roaming from the office to home with no change in logon procedures or access experience. When the access network is unified under Dell PowerConnect W-Series infrastructure, users experience consistent network services that “just work.” Fo ...
... whether it is Wi-Fi roaming without loss of voice sessions or roaming from the office to home with no change in logon procedures or access experience. When the access network is unified under Dell PowerConnect W-Series infrastructure, users experience consistent network services that “just work.” Fo ...
20070228-IMSP2P-Paris
... What is so special about P2P technology? 1. Join/Leave: Nodes may come and go at any time, the network topology reconfigures itself 2. Lookup: The network can locate deterministically the node that serves a specific user or service 3. Routing: The network can route a message regardless of network to ...
... What is so special about P2P technology? 1. Join/Leave: Nodes may come and go at any time, the network topology reconfigures itself 2. Lookup: The network can locate deterministically the node that serves a specific user or service 3. Routing: The network can route a message regardless of network to ...
An Introduction to TCP/IP - Oakton Community College
... Transport Control Protocol (TCP)/IP The Internet Protocol (IP) is responsible for ensuring that data is transferred between two addresses without being corrupted. For manageability, the data is usually split into multiple pieces or packets each with its own error detection bytes in the control secti ...
... Transport Control Protocol (TCP)/IP The Internet Protocol (IP) is responsible for ensuring that data is transferred between two addresses without being corrupted. For manageability, the data is usually split into multiple pieces or packets each with its own error detection bytes in the control secti ...
Securing Cognitive Wireless Sensor Networks: A Survey Linköping University Post Print
... vulnerabilities are exploited by adversaries who can have several incentives, for example, network disruption, information theft, and so forth. In general, there are two types of attackers [38]: (i) external attackers that are not authorized participants of the sensor network and (ii) internal attac ...
... vulnerabilities are exploited by adversaries who can have several incentives, for example, network disruption, information theft, and so forth. In general, there are two types of attackers [38]: (i) external attackers that are not authorized participants of the sensor network and (ii) internal attac ...
r02
... Approaches Towards Congestion Control • Two broad approaches towards congestion control: • End-end congestion control: • No explicit feedback from network • Congestion inferred from end-system observed loss, delay • Approach taken by TCP ...
... Approaches Towards Congestion Control • Two broad approaches towards congestion control: • End-end congestion control: • No explicit feedback from network • Congestion inferred from end-system observed loss, delay • Approach taken by TCP ...
PROTOCOLS COMPARISON IN AD HOC NETWORKS
... initial packet radio network ideas both more applicable and feasible [2]. Packet switching techniques, such as asynchronous transfer mode (ATM) and the Internet Protocol (IP) are widely accepted. Therefore, a MANET must be able to interact with the dominant protocols of the existing infrastructure, ...
... initial packet radio network ideas both more applicable and feasible [2]. Packet switching techniques, such as asynchronous transfer mode (ATM) and the Internet Protocol (IP) are widely accepted. Therefore, a MANET must be able to interact with the dominant protocols of the existing infrastructure, ...
3rd Edition, Chapter 5
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delaye ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delaye ...
F33022028
... the nodes and utilize the, Multi-hop communication links to leverage the computation of expensive queries, such as those involving aggregation. Continuous monitoring queries and distributed join algorithms have also been considered. Alternative methods try to reduce the cost of data processing in se ...
... the nodes and utilize the, Multi-hop communication links to leverage the computation of expensive queries, such as those involving aggregation. Continuous monitoring queries and distributed join algorithms have also been considered. Alternative methods try to reduce the cost of data processing in se ...
2-LAN-MPLS-Internetworking - ETH TIK
... • Combination of switching speed and router functionality. • Similar terminology: Routing switches or IP switches. • Identification for common traffic flows on layer 3 and switch these flows on the hardware level for speed. Other traffic will be routed as usual. ...
... • Combination of switching speed and router functionality. • Similar terminology: Routing switches or IP switches. • Identification for common traffic flows on layer 3 and switch these flows on the hardware level for speed. Other traffic will be routed as usual. ...
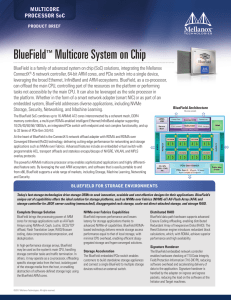
BlueField™ Multicore System on Chip
... BlueField enables the attachment of multiple GPUs through its integrated PCIe switch. BlueField PCIe 4.0 support is futureproof for nextgeneration GPU devices. Mellanox PeerDirect™ Mellanox PeerDirect is an accelerated communication architecture that supports peer-to-peer ...
... BlueField enables the attachment of multiple GPUs through its integrated PCIe switch. BlueField PCIe 4.0 support is futureproof for nextgeneration GPU devices. Mellanox PeerDirect™ Mellanox PeerDirect is an accelerated communication architecture that supports peer-to-peer ...
A Security Model for VoIP Steganography
... – Disguise information as natural “distortion” or noise. • Protocol Steganography for VoIP application – Hide information in unused data fields. ...
... – Disguise information as natural “distortion” or noise. • Protocol Steganography for VoIP application – Hide information in unused data fields. ...
A Security Model for VoIP Steganography
... – Disguise information as natural “distortion” or noise. • Protocol Steganography for VoIP application – Hide information in unused data fields. ...
... – Disguise information as natural “distortion” or noise. • Protocol Steganography for VoIP application – Hide information in unused data fields. ...
r02-review-transport..
... Approaches Towards Congestion Control • Two broad approaches towards congestion control: • End-end congestion control: • No explicit feedback from network • Congestion inferred from end-system observed loss, delay • Approach taken by TCP ...
... Approaches Towards Congestion Control • Two broad approaches towards congestion control: • End-end congestion control: • No explicit feedback from network • Congestion inferred from end-system observed loss, delay • Approach taken by TCP ...
NETWORK-ON-CHIP (NOC): A New SoC Paradigm
... In the case of variable packet size a length field is required ...
... In the case of variable packet size a length field is required ...
F. MILSA implementation considerations
... the data is transferred directly to the receiver through the routing infrastructure. Since RZBSs are dedicated signaling servers, MILSA offers better routing and forwarding performance than current Internet, and is more robust and efficient. Due to the design difference from SIP, the upper layer pro ...
... the data is transferred directly to the receiver through the routing infrastructure. Since RZBSs are dedicated signaling servers, MILSA offers better routing and forwarding performance than current Internet, and is more robust and efficient. Due to the design difference from SIP, the upper layer pro ...
Introduction to Routing and Packet Forwarding
... When designing a new network or mapping an existing network you must provide the following information in the form of a document: – Topology drawing that Illustrates physical connectivity – Address table that provides the following information: • Device name ...
... When designing a new network or mapping an existing network you must provide the following information in the form of a document: – Topology drawing that Illustrates physical connectivity – Address table that provides the following information: • Device name ...
IOSR Journal of Computer Science (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP 64-71 www.iosrjournals.org
... In the previous chapter, we reviewed some algorithms that can potentially be used in multicast routing protocols. Similar to unicast routing protocols (such as Routing Information Protocol (RIP) and Open Shortest Path First (OSPF) protocol), there should be multicast routing protocols such that mult ...
... In the previous chapter, we reviewed some algorithms that can potentially be used in multicast routing protocols. Similar to unicast routing protocols (such as Routing Information Protocol (RIP) and Open Shortest Path First (OSPF) protocol), there should be multicast routing protocols such that mult ...
A Survey on Sensor Networks
... No intermediate or carrier frequencies Pulse position modulation (PPM) Low transmission power and simple transceiver ...
... No intermediate or carrier frequencies Pulse position modulation (PPM) Low transmission power and simple transceiver ...